Review article on the topic of using modern private tunnels in routers of a popular Latvian brand. I will talk about how to set up a vpn server in mikrotik based on technologies such as l2tp, ipsec, openvpn, pptp, gre and eoip. Along the way, I’ll briefly talk about what these technologies are, how they differ, and also compare the performance of Mikrotik with all the specified tunnels.
If you have a desire to learn how to work with Mikrotik routers and become a specialist in this field, I recommend following a program based on information from the official MikroTik Certified Network Associate . The course is worthwhile, read the link for all the details.
This article is part of a single series of articles about Mikrotik.
Introduction
I would like to immediately point out that this article will be more of a review than a transfer of real experience, since I myself most often use openvpn as a vpn server. Nevertheless, I also had to deal with VPN in Mikrotik. I configured both pptp servers for connecting remote clients, and l2tp for combining two or more Mikrotik networks into a common private network. Mainly by default, without delving into the intricacies of the settings.
Today I want to look at this issue more carefully and see what Mikrotik generally offers out of the box for setting up VPN connections. I want to share my research with you by writing a short review on the topic of means of organizing a VPN server in mikrotik. And along the way, I want to collect feedback and corrections on the topic of what was written in order to strengthen my knowledge. I get a lot of advice from the comments to my articles, for which I am grateful to everyone who wrote useful things. So comments, additions and corrections are absolutely welcome.
For those who want to have a good understanding of networks, but for some reason do not yet know how to do this, I recommend this series of articles - networks for the little ones. Also, if you are not very familiar with Mikrotik, I recommend my article on setting up Mikrotik from scratch.
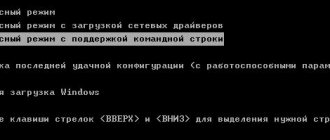
Timeline of PPTP use in operating systems
The pptp connection can be considered universal, since it is supported in many operating systems.
At the initial stages, when operating systems in the usual understanding of the user were just being formed, only one company, Cisco, was able to implement the protocol.
In subsequent stages ]Microsoft[/anchor] and its competitors were also able to fully implement this mechanism.
It was first used in Microsoft products in Windows 95 OSR2, and later developments even included built-in tools for configuring PPTP servers.
It is worth noting that PPTP support in Linux was introduced relatively recently. But modern versions still support it.
As for FreeBSD and Mac OS X systems, their architecture includes support for this technology through built-in PPTP clients, which allow you to fully experience all the benefits of such a connection.
rice. 3 – Where to configure PPTP in Linux
VPN server options in Mikrotik
With the vpn server options in Mikrotik, everything is complicated in the sense that there are many vpn implementations, which is not so easy to choose if you do not understand network technologies in detail. I don’t understand them much, but it seems to me that I get the gist a little. I will try to explain to you in my own words what the differences are.
in the sense that there are many vpn implementations, which is not so easy to choose if you do not understand network technologies in detail. I don’t understand them much, but it seems to me that I get the gist a little. I will try to explain to you in my own words what the differences are.
There are 2 fundamentally different solutions for organizing connections between two Mikrotik and external subscribers:
- Creating an l2 site-to-site tunnel using EOIP Tunnel . The easiest and fastest way to combine two Mikrotik. If encryption is not used, you will get the fastest VPN connections. Dedicated white IP addresses are required on both devices. Such connections are used to unite offices or branches via VPN. In general, it does not work through NAT. I’ll also add GRE Tunnel , although it works in l3 and uses routing, it also works on the site-to-site principle.
- VPN connections at level l3 using Client-Server technology, such as PPTP , L2TP , SSTP, OpenVPN . Such connections are used both to unite offices and to connect remote employees. Only one white IP address on the server side is enough to create VPN connections. Works through NAT.
I’ll tell you a little more about each type of VPN connection separately.
- GRE Tunnel - uses the simple gre protocol to build a basic, unsecured site-to-site VPN. Developed by CISCO. Allows you to encapsulate packets of various types inside IP tunnels. In simple words, this is what it does. It takes your data with all the headers, packs it into a packet, transmits it over the Internet to the other end, where this packet is parsed back into the original data. For end users of the network, all this looks as if they are communicating through a local network.
- EOIP Tunnel - Ethernet over IP is a proprietary MikroTik RouterOS protocol that creates an Ethernet tunnel between two routers over an IP connection. It uses the GRE protocol for data transfer. The fundamental difference between the eoip tunnel is that it operates in l2 and transmits frames directly, while the gre tunnel operates on packets and uses routing. I hope I explained it correctly and didn’t lie. Why mikrotik decided to create their own implementation of a tunnel via the gre protocol, I don’t know. Perhaps there are simply no similar solutions, so they came up with their own implementation.
- PPTP is a Point-to-Point Tunneling Protocol. It uses the GRE protocol to operate and supports encryption. At one time, pptp gained great popularity due to the fact that it was supported out of the box by Windows starting from version 95. Today, pptp is not recommended to be used, since it is very easy to hack. The encryption key is obtained from the traffic dump in a short time (several hours) and all traffic is decrypted. Perhaps this can somehow be combatted by using different encryption protocols, but I have not looked into this topic in detail. I decided for myself that pptp can be used as the simplest solution where there are no increased security requirements and traffic decryption, if it happens, will not bring any problems. PPTP supports out of the box not only Windows but also Android, which is very convenient. It's very easy to set up.
- L2TP - Layer 2 Tunneling Protocol. Despite the fact that the name says l2, in reality in an IP network it works at the session level, that is, l3. Uses UDP port 1701. Can work not only in IP networks. Out of the box, like pptp, it supports user authentication. It does not provide encryption on its own. It can use ipsec to encrypt traffic, which is considered very secure and does not have serious vulnerabilities. Currently supported by almost all devices and systems out of the box, just like pptp. It's not much more difficult to set up. In general, I recommend using this type of encrypted tunnel to organize a VPN.
- OpenVPN is a very popular implementation of encrypted connections. The main advantage is the flexibility of settings. For example, a very cool feature of openvnp is to push routes directly to the client upon connection. I've been using openvpn servers for a long time. When I first needed to transfer a pptp route to a client, I couldn’t figure out how to set it up. It turned out that there was no way, he simply couldn’t do it. I had to configure it using third-party tools. Unfortunately, for unknown reasons, mikrotik openvpn does not support the udp protocol, which greatly limits the possibilities of using this vpn server. It works much slower over tcp than over udp. Packet header compression also does not work. So in general, it doesn’t make sense to use an openvpn server in Mikrotik, unless you need it for some specific reason.
- SSTP - Secure Socket Tunneling Protocol - was introduced by Microsoft in Windows Vista SP1. The main advantage is that it is integrated into Windows and can use port 443, which sometimes helps bypass firewalls. Considered very secure, uses SSL 3.0. The downside, as far as I know, is that Mikrotik is very demanding on processor resources. On weak hardware it will provide the lowest speed compared to all other VPN connections. For this reason, I will not consider it in my review at all.
From everything written we can draw the following conclusion. In general, it is best to use a VPN based on l2tp + ipsec in Mikrotik. Main reasons:
- Simplicity and ease of setup.
- Strong encryption.
- Support for l2tp connections by almost all modern devices and systems. There is no need to install additional software.
- Suitable for both combining offices and remote workers - site-to-site and client-to-site connections.
If you need maximum performance without encryption, then build connections between networks or offices using EOIP Tunnel, a proprietary development from Mikrotik.
Next, I will show how to configure all the described tunnels, except SSTP, and take speed measurements for comparison. My test bench of two Mikrotik RB951G-2hnD will have the following settings.
| m-server | name of Mikrotik acting as a server |
| m-remote | the name of Mikrotik acting as a remote router |
| 192.168.13.1 | WAN ip address on m-server |
| 192.168.13.197 | WAN ip address on m-remote |
| 10.20.1.0/24 | local network behind m-server |
| 10.30.1.0/24 | local network for m-remote |
| 10.10.5.1-10.10.5.100 | vpn network |
Let's start setting up and testing VPN connections in mikrotik.
Data encryption
PPTP may (or may not) use data encryption using the MPPE (Microsoft Point-to-Point Encryption) protocol. MPPE supports 40, 56 and 128 bit keys. However, not all devices using PPTP can use encryption. Many older modems and home routers do not support MPPE encryption.
It is worth noting that when working with VPNKI, to use a connection with encryption you need in the connection settings: - use MS-CHAPv2 authorization and indicate that encryption (MPPE) will be used. For a connection without encryption you need: - use CHAP authorization and indicate that no encryption will be used.
Setting up an l2tp tunnel in mikrotik
First, let's set up a simple l2tp tunnel without encryption and measure the speed. To configure l2tp vpn in mikrotik, follow the following sequence of steps.
Go to the IP -> Pool and add a pool of IP addresses for the vpn tunnel.
Create a profile for the tunnel in PPP -> Profiles .
On the remaining tabs, the settings are default. Next, create a user in PPP -> Secrets .
Now let's start the l2tp server. Go to PPP and click on the L2TP Server .
We set the settings for the l2tp server. We do not enable ipsec yet.
The VPN server is configured. Now let's create a permanent interface for it so that we can create static routes based on it. Go to Interfaces and create L2tp Server Binding .
Finishing touch. We create a static route with the help of which subscribers of the server’s local network will be able to connect to a local network subscriber behind a remote router via VPN. Go to IP -> Routes and add a route.
I didn’t consider the issue of setting up a firewall, because I didn’t want to bloat an already lengthy article. This is not directly related to this topic. Read more about setting up a firewall separately at the link provided. Here I will only indicate what needs to be opened on the firewall to configure l2tp correctly.
We need to create the following firewall rules on the server so that we can reach our L2TP server. IP -> Firewall -> Filter Rules . You need to create an allow rule in the input chain for the following ports and protocols:
- Protocol: UDP
- Allow ports: 1701,500,4500
- As In.Interface we indicate the one through which the l2tp connection occurs.
Separately, we add another rule that allows the ipsec-esc .
Everything is ready on the server. Let's go set up the l2pt client on a remote Mikrotik.
L2tp client
Everything is quite simple here. Let's go to PPP and add L2TP Client . We indicate the settings that were previously specified on the server.
We add a static route so that clients of this router know where to contact subscribers of the remote local network for VPN.
That's all. We configured l2tp on a remote Mikrotik and thus united 2 local networks using vpn. In the list of IP addresses, with an active l2tp connection on the server and client, you should see IP addresses from the range specified on the server for the vpn network - 10.10.5.1-10.10.5.100. Now you can ping opposite networks from both networks.
I have laptops connected to both Mikrotik for testing. Now I will measure the connection speed using iperf3. behind the m-remote on the laptop 10.30.1.254, and the agent on 10.20.1.3. Let's run a VPN connection speed test:
Average speed 194 Mbit/sec . Frankly speaking, I didn’t understand why the speed was so low. My test bench is assembled on two Mikrotik routers and a gigabit Mikrotik switch between them. I expected to see something around 500 Mbit/sec. Let me remind you that the tunnel is not yet encrypted. At the same time, the processor load on the routers was around 90-95%. That is, in fact, the ceiling of these pieces of iron.
Let's now try to enable ipsec encryption and measure the speed with it.
Setting up ipsec
I was stuck with setting up ipsec for l2tp for a while. There are many instructions on the Internet, but they are all outdated. As it turned out, in the latest firmware versions, launching ipsec in the default settings is not easy, but very simple. To do this, you just need to specify Use IPsec - yes in the l2tp server properties and set a password.
All necessary ipsec settings will be created automatically. On the agent, do the same - enable ipsec encryption and specify a password.
After connecting the l2tp client, you will see similar lines in the log:
19:17:00 l2tp,ppp,info l2tp-out1: initializing… 19:17:00 l2tp,ppp,info l2tp-out1: connecting… 19:17:03 ipsec,info initiate new phase 1 (Identity Protection): 192.168 .13.197[500]<=>192.168.13.1[500] 19:17:04 ipsec,info ISAKMP-SA established 192.168.13.197[500]-192.168.13.1[500] spi:407844c0ceb5d2ab:46ce7ffb25495efd 19:17:07 l2tp ,ppp,info l2tp-out1: authenticated 19:17:07 l2tp,ppp,info l2tp-out1: connected
In order to make sure that ipsec encryption is working, you can go to the IP -> Ipsec -> Installed SAs and look at the counter of encrypted packets. If it grows, then everything is in order, the traffic is encrypted.
There, in the Remote Peers , you can see a list of remote clients for which ipsec encryption works, and see the algorithms used. All default ipsec settings live in this section. You can view them, change or add new profiles. By default, the sha1 authorization algorithm and AES encryption are used. You can change these parameters if you understand the topic. I won’t be clever, I didn’t dig into the topic of encryption. I don’t know which algorithms are the fastest and most secure.
Let's test the speed of a vpn connection l2tp + ipsec.
I got it like this - 26 Mbit/sec on average. At the same time, the processor load is 100%. Not much. These pieces of hardware are very poorly suited for encrypted channels. In these tests they are not loaded with anything other than the test itself. In real conditions the speed will be even lower.
We are done with the VPN settings based on l2tp + ipsec. Let's continue setting up the remaining VPN tunnels and compare their speed.
Configure settings for VPN network connections
Operating systems of the Windows family have a number of distinctive features. But they all have in common the ability to connect and configure a VPN PPTP connection. The only question is which version of the Microsoft OS is used on a particular computer or laptop.
In this regard, several instructions are offered that are relevant for the most popular versions of Windows OS. Namely:
- XP.
- Windows 7.
- Windows 8.
- Windows 10
Each of them has its own order and configuration settings.
Settings for Windows XP
The first in line will be the already outdated, but still actively used by users with weak computers operating system in the form of Windows XP.
Here to set up a PPTP VPN connection you need to:
- open the control panel by clicking the "Start" button;
- select the “Network and Connections” section;
- click on the “Create a network connection” option on your desktop;
- There will be 2 options to choose from;
- this is a remote access connection, as well as a virtual private network;
- you need to select the second option and put a tick in front of it;
- Next, you should specify any name you like for connecting;
- at the same time, open my account, where there should be a list of IP addresses for PPTP VPN services, user login and password;
- enter the found IP address in the connection creation line;
- add a checkmark next to the item asking you to create a connection shortcut;
- then the “Done” button.
All that remains is to click “Start”, enter the “Connection” section and select the new created network.
When connecting for the first time, you will be required to specify a login and password, after which you can save the entered data.
If all operations were completed correctly, the connection will be completed successfully.
Settings for Windows 7
Despite the end of support, Windows 7 continues to be popular.
Setting up PPTP on Windows 7 yourself should not pose any particular difficulties. The instructions can be presented as follows:
- Through the Start menu, or through the network connection in the lower right corner, open the Network Sharing Center menu.
- Here you should click on setting up a new connection or network.
- Among the suggested options, look for desktop connection, and then click “Next”.
- Now 2 options will appear. This is direct dialing, or using an existing VPN connection. You need to select the first option in the list, that is, your Internet connection.
- Now you will again have to go to “My Account”, where you should look at the list of PPTP VPN servers, login and password for the VPN. Copy them or rewrite them for yourself.
- In the next settings menu, you just need to specify the IP address, come up with a name for the connection and check the box next to the “Don’t connect now” item.
- Next, you need to specify the username and password for the VPN. To avoid having to enter the same data again each time you connect, check the “Remember password” checkbox.
That's it, the connection is created, you can close the window.
Next, right-click again on the network connection icon at the bottom of the screen and look at the list of current connections. The previously created VPN network should appear here.
Click on the “Connection” button. In the window that opens, click on “Properties”. Look at what items are ticked in the “Options” section. They need to be placed on the first two lines and removed from the last one, where it says “Include login domain”.
Go to the "Security" section. The VPN type must be PPTP, and data encryption is required.
All that remains is to click “OK” and in the main connection window click the Connect button.
This completes the setup. You can safely use PPTP VPN on your computer or laptop running Windows 7.
Setting up for Windows 8
The Windows 8 operating system remains current and supported.
You may also need to configure PPTP here.
A user of a PC or laptop running Windows 8 will need:
- open “Networks” by clicking on the network connection icon at the bottom of the screen;
- select the item to view connection parameters;
- then click on the plus icon in the VPN section, thereby starting to add a new connection;
- Open “My Account”, copy the VPN login and password, and view the list of PPTP servers.
When adding a new VPN connection, you will need to provide a number of data. Namely:
- the OS developer, that is, Microsoft, is indicated as the service provider;
- come up with a name for the connection yourself;
- paste or enter the IP address of the PPTP VPN server used;
- for authorization, select a username in combination with a password;
- then the user name itself, as well as the password;
- Don't forget to check the box to remember your login details;
- Now click on the “Save” button.
Next, click on the network connection icon again, and the connection created in the previous step will appear in the “Networks” section. Here you should click on “Connect”.
If the status displays as “Connected”, you have done everything correctly.
Setting up for Windows 10
Now to the question of setting up PPTP for Windows 10. The task is not the most difficult. Especially if you already have experience configuring on other versions of operating systems.
To create a PPTP connection for Windows 10, you will need to perform several sequential procedures. Namely:
- click on the notification icon located in the lower right corner of the computer or laptop screen;
- choose the option with a virtual network, that is, VPN;
- a new window with parameters will appear, where you need to click on the add connection button;
- select Windows as your service provider;
- come up with the connection name you want to use;
- indicate the existing VPN server address by looking at it in your account;
- connection type will be PPTP;
- It is better to use your login and password to log in;
- create a fairly complex password;
- check the box to remember the entered information;
- save the changes in the settings of the new connection.
Now that the PPTP VPN has been created, you should connect to it by clicking the corresponding button. It may take some time to establish the connection. When the connection is complete, the window with parameters can be closed.
Setting up a pptp server in mikrotik
Setting up a pptp server is not fundamentally different from l2tp. The logic and sequence of actions are the same. First, we create a pool of addresses in IP -> Pool for the vpn network. I will use the same pool that we created earlier.
Next, create a profile for the pptp tunnel in the PPP -> Profiles .
This profile contains the default encryption settings, in which it is disabled. Let's first check the speed of the VPN channel without them. Create a new user for a remote pptp connection.
We enable the pptp server in the PPP section.
Now let’s create a PPTP Server Binding , similar to the previous section.
And finally, add a static route to the remote network via a pptp connection.
The pptp server setup is complete. On the firewall, you will need to open the following things for incoming connections from the external interface:
- TCP port 1723
- GRE protocol
Let's set up the pptp client.
pptp client
We go to the remote router and configure the connection via the pptp client. We go, as usual, to the PPP and add PPTP Client . On the General tab we do not touch anything, but on Dial Out we indicate the address of the pptp server and the user name to connect.
Add a static route to a remote office via a VPN tunnel.
All is ready. We activate the pptp connection and try to ping addresses on the local network. You can make sure that encryption is disabled in the pptp connection status on the client.
Let's now check the speed of the VPN connection via pptp.
The same 194 Mbit/sec as on unencrypted l2tp at 100% processor load. In general, it was a little strange to see exactly the same numbers. I ran the tests several times, but always had the same result. Without encryption, there is no difference in speed between l2tp and pptp connections.
Now let's enable encryption in pptp on the server and look at the speed. To do this, we explicitly indicate in the pptp profile that encryption is used. Go to PPP -> Profiles and edit our profile.
Let's make sure the client status is working.
I am testing the speed of a VPN connection via pptp with encryption enabled.
The result was an average of 71 Mbit/sec . Not a bad result compared to ipsec encryption in l2tp. As I said earlier, a pptp server is well suited where encryption is either not needed at all, or the possibility is allowed that encrypted traffic will be decrypted. But at the same time, it is still closed with encryption and everyone passing by will not be able to see anything. At a minimum, you need to dump the traffic and somehow select a key using a dictionary or brute force. I don't know exactly how this is implemented in practice. Didn't study the issue.
Let's now move on to the openvpn server in Mikrotik. It is very interesting to look at the speed tests of this type of VPN connection.
Structure
Figure 1 shows the structure of a PPTP packet. In general, nothing special; a PPP frame and a GRE header are encapsulated in the IP packet.
Rice. 1
Briefly about GRE. This is a tunneling protocol that operates at Layer 3 of the OSI model. The GRE function is the encapsulation of network layer packets of the OSI network model into IP packets.
Tunneling involves three protocols:
- passenger - encapsulated protocol (IP, CLNP, IPX, Apple Talk, DECnet Phase IV, XNS, VINES and Apollo);
- encapsulation protocol (GRE);
- transport protocol (IP).
The header takes 4 bytes (Fig. 2) and consists of 2 parts:
1) 1-2 bytes
- flags
:
- ChecksumPresent
– bit 0, if equal to 1, then the GRE header contains an optional checksum field – Checksumfield;
— Key Present
– bit 2, if equal to 1, then the GRE header contains an optional field containing the key – Key field;
— Sequence Number Present
– bit 3, if equal to 1, then the GRE header contains an optional sequence number field – SequenceNumberfield;
— Version Number
– bits 13–15. This field indicates the GRE implementation version. A value of 0 is typically used for GRE. Point-To-Point Protocol (PP2P) uses version 1.
2) 3-4 bytes.
Contains the protocol type (ethertype) of the encapsulated packet.
Rice. 2
Setting up openvpn server in Mikrotik
There is nothing complicated in setting up an openvpn server on mikrotik, except for the nuance with certificates. To someone who has never worked with them, everything may seem too complicated. In addition, Mikrotik itself does not have any tools for creating server and client certificates. It is necessary to use third-party utilities. If you have a Linux machine, you can use my instructions for creating certificates for openvpn on Linux.
If you don’t have a Linux machine, but you are still determined to set up a vpn tunnel using openvpn in Mikrotik, then let’s look at the setup further. First of all, we need an openvpn distribution for windows. You can download it from the link - https://openvpn.net/community-downloads/. We will be interested in Windows Installer.
We perform the installation as an administrator and specify in the process a component called EasyRSA 2 Certificate Management Scripts .
Go to the directory C:\Program Files\OpenVPN. We move the easy-rsa folder from there to somewhere else so that we don’t have to constantly stumble over UAC, which will not allow us to work calmly in Program files. I moved it to D:\tmp\easy-rsa. Rename the file vars.bat.sample to vars.bat. We open it for editing and bring it approximately to the following form.
For those who don't understand, these are just variables that I specified to suit my needs. You can write whatever you want there, it’s not important for our task. You can not change anything at all, but leave it as is. Create a folder called keys in the directory. Next, launch the command line as administrator and move to the specified directory D:\tmp\easy-rsa.
Next, write vars on the command line and press enter. This will load the variables from the vars.bat file, then enter clean-all . Next, we generate the Root CA with the command - build-ca .
We answer the questions asked and complete the creation of the root certificate. It will appear in the D:\tmp\easy-rsa\keys folder. Next, we create the openvpn server certificate with the command - build-key-server server_name .
Now let's generate a certificate for the client. I have only one client in the form of a remote Mikrotik. You create exactly as much as you need. We use the command build-key certificate_name .
We are done with creating certificates. We have them all in the keys directory. You need to transfer the following files to Mikrotik, which will act as an openvpn server:
- ca.crt
- ovpnserver.crt
- ovpnserver.key
Import certificates from added files. Go to System -> Certificates and import first ca.crt, then ovpnserver.crt and ovpnserver.key.
It should look something like this. Now let's start setting up an openvpn server in mikrotik. Let's create a separate profile for it in PPP -> Profiles .
All settings are default. As a local and remote address I use the Ip Pool, which I created at the very beginning of the l2tp setup. Let's add a remote user for openvpn in PPP ->Secrets .
Go to the PPP and click OVPN Server . Specify the settings and the downloaded ca certificate.
OVPN Server Binding , by analogy with other VPN servers .
This completes the setup of the openvpn server in Mikrotik. By default, the BF-128-CBC . It can be changed in the client properties, and a list of all supported ciphers in the VPN server properties.
For the specified openvpn server setting to work, you must open incoming TCP port 1194 on the firewall. Now let's set up the openvpn client and test the connection speed via vpn based on openvpn.
openvpn client
To configure openvpn client on mikrotik, you need to transfer the certificates generated in the previous step there. Specifically these files:
- m-remote.crt
- m-remote.key
We import the certificate from these files, just like on the server. Please note that there must be the characters KT next to the certificate name.
Now configures the openvpn client. Let's go to PPP and add OVPN Client .
Add a static route to access remote network resources behind the openvpn server.
All is ready. You can connect and test the speed of your VPN connection via openvpn.
The result was an average of 24 Mbit/sec with 100% processor load. The result is comparable to l2tp + ipsec. The result was a little surprising. I thought it would be worse than l2tp, but in reality it’s the same. I personally generally like the option with openvpn better, although due to the limited openvpn settings in Mikrotik, the advantages of openvpn are difficult to realize. Let me remind you that I tested with BF-128-CBC encryption, that is, blowfish.
Here is the result with AES-128-CBC - 23 Mbit/sec, about the same.
Mikrotik has sorted out the client-server implementations of the VPN server. Now let's look at the speed of l2-vpn in the form of eoip tunnel.
Securing the connection
As noted above, the data is transmitted in the form of an encrypted packet.
To encrypt it, special tools are used, a full list of which can be viewed in the connection settings.
We will highlight those that are characterized by a high degree of security, in particular:
- MSCHAP-v1;
- MSCHAP-v2;
- EAP-TLS;
- MPPE.
To provide an increased level of protection, you can additionally use dialers—response calls implemented programmatically.
They allow you to verify whether the data packet was transmitted completely or whether it was damaged during the transfer process.
In the meantime, let’s look at what makes the options presented above stand out.
It is worth noting that MSCHAP-v1 is not particularly reliable.
To extract password hashes from it, you can use special interception utilities.
MSCHAP-v2 in this sense differs from its predecessor, but is vulnerable to dictionary attacks on intercepted data packets, for which special programs are also used, the data processing speed of which can take only a day to decrypt.
Cryptanalysts can also decrypt data from MPPE, which is based on the use of the RC4 stream.
For example, you can decrypt it using the bit substitution method.
However, if desired, such a vulnerability can be detected using appropriate methods that calculate checksums.
Thus, it becomes clear that the protection installed on PPTP can be bypassed. And that is why it is necessary to use additional security measures.
rice. 5 – Simplified scheme of a secure PPTP channel
You may be interested in:
How to enter router settings - TP-Link, D-Link, Asus, Zyxel Keenetic, Rostelecom
How to connect a router to a router via WiFi - 2 easy ways
Top Tips: How to Strengthen Your Router's WiFi Signal
Setting up EOIP Tunnel + Ipsec
Let's set up a VPN network based on EOIP in Mikrotik. Here you need to understand one important difference from all the previous settings that we made earlier. The EOIP tunnel operates at the l2 level, that is, both network segments will consider themselves to be on the same physical network. The address space for both will be the same. In my example it is 10.20.1.0/24. There should only be one DHCP server for both networks. In my case it will remain on m-server .
Create an EOIP tunnel on m-server. Go to Interface list -> EoIP Tunnel and add a new one.
From the settings, it is enough to specify only the remote address of the second Mikrotik. The new EoIP interface must be added to the local bridge along with the physical interfaces.
We go to the remote Mikrotik and do the same thing there, only we specify a different Remote Address.
This is enough for the EoIP tunnel to work immediately. His condition will be RS.
On the second Mikrotik, the EoIP interface also needs to be added to the local bridge with other interfaces.
The easiest way to check that everything is in order is to request the m-slave IP address for the bridge interface via dhcp. He must obtain an IP address from the dhcp server on m-server, provided that there are no other dhcp servers on the network. The same will happen with local machines on the network behind m-slave. They will receive IP addresses from the dhcp server on m-server.
Let's now check the performance of such a VPN tunnel based on EoIP.
I show the maximum result that I got - 836 Mbit/sec . For some reason, in different tests the speed fluctuated in the range between 600-850 Mbit/sec. In order for the speed to change, it was necessary to disable and re-enable the EoIP interface. The speed is impressive. At the same time, the processor is not 100% loaded. That is, he is not the bottleneck. Looks like I'm stuck with network performance. Let me remind you that there is no encryption or traffic routing here. Direct l2 channel between two Mikrotik via EoIP vpn.
Let's add Ipsec encryption to the EoIP tunnel and look at the speed. To do this, change the channel settings on both Mikrotik. Add the Ipsec password and local addresses, disable Fast Path.
We measure the connection speed.
27 Mbit/sec using EoIP + Ipsec . The speed is comparable to L2tp and Openvpn encrypted tunnels. In this regard, there were no pleasant surprises. Encryption is very difficult for this piece of hardware. One might say that it is practically not intended for him at all.
Example of setting PPTP parameters in OS MS WINDOWS 7
To understand all the intricacies of a PPTP connection, you should try to configure such a connection yourself.
We will look at how this process occurs in Windows, in particular in its popular seventh version. This is easy to do following our recommendations.
Initially, you will need to launch the Control Panel. The easiest way to do this is from the Start menu.
In it you will need to select the Network Sharing Center category.
You can get there without going through the described chain. In this case, you should select the same item from the context menu called up by the network connection.
You can find it in the notification area located at the bottom right of the screen.
rice. 6 – Control Panel Categories
After launching the Control Center, you can make changes to the network adapter properties.
To do this, you will need to select the Change network adapter settings command in the left area of the window.
You can then call Properties from the context menu for your existing local connection.
Next, in the dialog that opens, you will need to install the TCP/IPv4 protocol data received from your communication provider.
At the same time, most providers allow you to set addresses on workstations for DNS and IP servers automatically.
After entering the data, you will need to save it.
Once you have completed making changes to the settings, you will need to activate the connection.
To do this, in the main window of the Control Center, you need to select the previously configured connection and call the menu for it with the right mouse button.
In it you should select the Enable item.
rice. 7 – Network and Sharing Center category window
GRE tunnel + Ipsec in mikrotik, creation and configuration
To configure a GRE tunnel in Mikrotik, go to the Interfaces -> GRE Tunnel and add a new one with the following settings:
We assign an IP address to the GRE tunnel in IP -> Adresses .
We immediately create a static route to access remote network resources.
To organize a VPN connection via GRE tunnel, we do the same on a remote Mikrotik, only we change the corresponding addresses.
Create a GRE Tunnel.
We assign an IP address.
Add a route to the remote local network.
After this, routing traffic between local networks should work. Don't forget to enable the gre protocol on your firewall.
Let's now check the connection speed via the GRE tunnel.
I got 247 Mbit/sec . Let me remind you that this is an unencrypted routable VPN tunnel. The difference from the l2 EoIP tunnel is approximately 3 times lower in speed. Draw your own conclusions about which tunnels to use. If routing is not needed, then definitely EoIP.
Now let's check the same thing, only by configuring Ipsec encryption in GRE. We add the appropriate settings to the GRE tunnels on both Mikrotik.
I measure the speed of GRE + Ipsec, encryption algorithm aes-128 cbc.
The result was an average of 29.7 Mbit/sec , which approximately corresponds to all results with ipsec. Not surprising, because the encryption algorithm is the same in all cases. But nevertheless, the speed in GRE Tunnel is slightly higher than all other participants. From this we can conclude that exclusively for l3 site-to-site connections, GRE Tunnel is best suited in terms of performance.
How it works and the connection process
It works like this:
- PPTP organizes PPP session . The Generic Routing Encapsulation protocol is used.
- Another connection is made on port 1723 . It is needed for transition and management of GRE.
- MPPE protocol is used . It protects data in transit.
- Client authentication occurs using MSCHAPv 2, EAP - TLS .
- At the other end of the line, information is extracted from the IPX .
- Sent for processing by the system's own protocol.
Ways to change your computer's IP address
To receive transmitted data at the human level, the user uses a login and password .
Important! While sending information, the channel can be hacked by guessing your login and password. But when data is transferred, hacking is impossible!
Comparison of speed of L2tp, Pptp, EoIP, GRE and OpenVPN tunnels
I will summarize all measurement data in a single table for a visual and convenient analysis and comparison of the speeds of all mentioned VPN connections in Mikrotik.
| VPN Tunnel | Encryption | Speed (Mbps) |
| l2tp | No | 194 |
| l2tp | IPsec AES-128 CBC | 26 |
| pptp | No | 194 |
| pptp | MPPE128 | 71 |
| openvpn | BF-128-CBC | 24 |
| eoip | No | 836 |
| eoip | IPsec AES-128 CBC | 27 |
| gree | No | 247 |
| gree | IPsec AES-128 CBC | 29,7 |
The table below clearly shows the difference in various encryption methods. Using it, you can quickly assess what performance losses encryption may cause. Now everyone encrypts everything by default, but if you look at it, very often this is not required. You can make a compromise and use a pptp server, which, although it does not provide 100% secure encryption, nevertheless hides traffic from simply prying eyes and has good performance. In any case, the traffic cannot be read just like that; you need to make a deliberate effort to decrypt it. In some cases, such protection will be sufficient.
Description of technology
The specification was first released to the public in July 1999 and was developed by Microsoft subsidiary Ascend Communications (today part of Alcatel-Lucent). PPTP has not been adopted or standardized by the Internet Engineering Task Force. The protocol is created by communicating with a peer on PPTP port 1723. This TCP connection is then used to initiate and control the peer.
The PPTP GRE packet format is non-standard, including a new acknowledgment number field that replaces the typical routing field. However, as in a normal GRE connection, these modified GRE packets are directly encapsulated in IP packets and are treated as protocol IP number 47. The GRE tunnel is used to transport PPP packets. In Microsoft's implementation, tunneled PPP traffic can be authenticated using PAP, CHAP, MS-CHAP v1/v2.
Online courses on Mikrotik
If you have a desire to learn how to work with Mikrotik routers and become a specialist in this field, I recommend taking courses in a program based on information from the official MikroTik Certified Network Associate . In addition to the official program, the courses will include laboratory work in which you will be able to test and consolidate your acquired knowledge in practice. All details on the website. The cost of training is very affordable, a good opportunity to gain new knowledge in a subject area that is relevant today. Course Features:
- Practice-oriented knowledge;
- Real situations and tasks;
- The best of international programs.
Conclusions and parting words
If we approach the assessment with full responsibility and give a detailed description, we can note that a PPTP connection is a very controversial method of data transfer.
It is designed for secure data transmission over the network, but does not provide complete security.
This is partly due to the fact that this protocol is somewhat outdated (the date of initial implementation was 1999).
The communication channel created using such a connection is quite reliable, but for the average network user it is not justified.
For the same purpose, at home it is easier to use anonymous proxy servers and anonymizers.
They will provide no less reliability and can be used not constantly, but periodically as needed.
As for commercial organizations, for their communications, networks built on this principle will be the easiest way to ensure network security.
But, at the same time, you can use other more reliable means.
rice. 8 – Example of a corporate network based on PPTP
Preparatory operations
Regardless of which VPN server option you prefer, client access to the Internet will be provided by standard operating system tools. In order to open access to the Internet from the internal network through the external interface of the server, you must allow packet forwarding between interfaces (packet forwarding) and configure address translation.
To enable packet forwarding, open the file “/etc/sysctl.conf” and change the value of the “net.ipv4.ip_forward” to 1 .
To apply the changes without rebooting the server, run the command
sudo sysctl -p /etc/sysctl.conf
Address translation is configured using iptables . Let’s first clarify the name of the external network interface by running the “ip link show” ; it will be needed in the next step. In our case, the interface name is “ens3” .
We enable address translation on the external interface for all local network nodes.
sudo iptables -t nat -A POSTROUTING -o ens3 -j MASQUERADE
Please note that you must specify the real name of the network interface in the command. It may differ on your server.
By default, all created iptables are reset after the server is rebooted; in order to avoid this, we use the “iptables-persistent” . Install the package.
sudo apt install iptables-persistent
During the installation process, a configuration window will open in which the system will offer to save the current iptables rules. Since the rules are already configured, we agree and click “Yes” . Now, after rebooting the server, the rules will be restored automatically.