In practice, proxies are more suitable for everyday protection of web traffic, without creating the inconvenience of a noticeable loss of speed and indiscriminate tunneling. That is, when using a good proxy, there is no need to disable it for comfortable Internet use.
This article explains the advantages of a secure proxy over a VPN and offers various ready-to-use implementations.
What is the difference between a VPN and a proxy?
VPN is the general name for technologies for connecting internal networks at the level of network packets or frames through a connection established over another network (usually a public one).
A proxy is a server application that makes connections or requests on its own behalf and network address in favor of the client connected to it, as a result sending it all received data.
A VPN forwards payloads located at layer three or layer two of the OSI network model. Proxies forward payloads between the fourth and seventh layers of the OSI network model, inclusive.
Both VPNs and proxies may or may not have encryption between the client and server. Both technologies are suitable for routing user traffic through a trusted server, applying encryption along the way. However, connecting through a proxy does this in a more straightforward way, without introducing the additional encapsulation of network packets, gray addresses of the VPN network itself, and routing table changes that a VPN introduces simply to ensure that the user's system's network stack routes traffic through the desired server.
Free Proxy
These are the simplest addons that are presented in the extension store of each browser. The only thing they can do is mask the IP address, but some services like Flash or Java can still detect the real address. Often such extensions may contain VPN in the name, but be a proxy. For example, this is exactly what happened with the Opera browser, which was positioned as a browser with a built-in VPN, but it was a simple Proxy, and not very high quality.
Advantages:
- There are a lot of free proxies, unlike VPNs, and they can be installed literally in a minute, so you can easily change them and try new ones.
- Registration is usually not necessary.
- You can easily and quickly hide your geo-location, albeit in a basic way.
Minuses:
- There is no such thing as free: either they will show you advertising, or they will limit your speed and traffic, encouraging you to pay for a package, or they will collect and resell traffic.
- In worst cases, your device can be used in a chain, and attacks and illegal actions will be carried out through it.
- The information flow is not encrypted.
Advantages of a proxy
- In a real network with losses, the practical speed of a proxy is often higher than that of VPN solutions. This is because when proxying TCP connections, retransmits in the client-proxy and proxy-target sections occur independently. The proxy has its own TCP buffers and short-term I/O delays in both directions do not affect transmission from the opposite side. VPN only works at the network layer (IP) and lost TCP segments will be forwarded along the entire path from the VPN client to the target server.
- Flexibility. It's easier to set up selective proxying. The use of proxies can be limited to specific applications, and in the browser - to specific domains. You can use several different proxies for different destination addresses at the same time.
- Difficult to detect using DPI, including DPI performing active probes. However, this requires some additional setup. In the case of a proxy via TLS, such a connection can be passed off as a regular HTTPS connection. In the case of a VPN, the fact of its use is visible even to passive DPI. Even if it's Wireguard.
- There is no whole class of problems with a VPN connection that suddenly breaks. In a worst-case scenario, the VPN connection may be interrupted and the user will not notice that his traffic is no longer protected and/or he is already working from his “home” IP address. In the case of a proxy, such problems are excluded.
- There is no fundamental possibility of carrying out attacks that allow traffic past the VPN tunnel. An example of such a problem.
- High privileges in the system are not needed for either the proxy client or the server. This can be very useful in cases where you do not have high rights in the system.
Choice of our specialists (recommended)
- Monthly $11.95
- 12 months $83.88
- 24 months $95.75
Read the review →
Nord VPN in the ranking of VPN services is especially recommended for those who need increased security and anonymity on the network
pros
- Increased security
- No logs
Minuses
- No Bitcoin refund
- No technical support by phone
from $4.95 month, 58% discount
Get a discount
→
1.
Pros:
- When choosing a good provider, you are completely protected, and you can even hide the very fact of connecting to a VPN server.
- Unlimited traffic, minimal speed reduction, very wide selection of countries.
- Servers for various tasks - P2P file sharing, watching videos, surfing.
- Operability even in countries where network access is tightly controlled.
- The Kill Switch function will protect you even if the connection with the VPN server is interrupted.
- The CyberSec feature (or similar) blocks unwanted advertising and malware.
- Military-grade encryption - it will take decades to decrypt.
Minuses:
- Good services are paid, the cost can be 10-13 dollars per month, and if you buy large packages - 3-5 dollars, but then you need to pay the entire amount at once (about 60-100 USD).
- Some providers greatly reduce the speed and slow down the device.
When to use:
- If you need maximum protection.
- In countries with severe censorship or internet restrictions.
- When you want to maintain absolute anonymity.
Select VPN
Typically, one paid license can be used for several devices - from 3 to 6, so it is relatively inexpensive. All providers offer discounts for large packages.
Proxy requirements
When choosing an implementation of a secure proxy server for myself, I noted several criteria that it must satisfy:
- Mandatory encryption and protection of data integrity within the connection.
- Reliable and proven cryptography. Homegrown crypto protocols are highly undesirable.
- Resistant to DPI, including active samples. Ideally, the protocol should look indistinguishable from protocols to which there are usually no complaints. For example, like HTTPS.
- No multiplexing of multiple TCP connections within one. The reason for this requirement is that it is not desirable for multiple connections to be speed-limited by a single TCP connection. In addition, when multiplexing multiple connections within one, pausing the receipt of data from one internal (multiplexed) connection can stall all others indefinitely. To do this, it is enough that the proxy server expects to send more data than the total size of the sending buffer of the demultiplexer client and the socket receive buffer of the application that stopped the reception. In particular, this effect can sometimes be achieved by starting to download a large file through an SSH SOCKS5 proxy (ssh -ND 1080), and pausing the download. If things go wrong, no more traffic will be accepted through the tunnel. Learn more about the head-of-line blocking problem.
- No connection to a supplier or service.
I've looked at several well-known protocols for encrypting a proxy connection:
| Name | Summary |
| OpenSSH dynamic port forwarding (ssh -ND 1080) | Uses multiplexing: low speed, delays |
| shadowsocks | DPI failure |
| obfs4 | In appearance it meets all the requirements, but there are points that raise doubts |
obfs4 Features
There are places in the obfs4 protocol specification that raise questions.
The client handshake uses the hour number from the start of the UNIX epoch, which is then used in the HMAC signature. The server, receiving such a packet from the client, checks it, substituting the hour number according to its time. If everything is correct, then he answers with his part of the handshake. To combat the spread of hours, the server must also check the previous and next hour. Knowing this characteristic behavior, you can check the server at the boundary of the next and next hour by replaying one of the past recorded handshakes from the client. If the server stops responding with its part of the handshake at this very time, then this is sufficient reason to judge that the server is serving the obfs4 protocol.
Apparently, the author eventually realized this problem and the obfs4 code implemented protection against detection through replay. It is not described anywhere in the specification.
However, such protection, on the contrary, simplifies the work of blocking the protocol: in case of doubt, it is enough for the network filter to delay sending the handshake from the client, intercepting it, and then send the message with the handshake first. Thus, it will trigger replay protection against the client, forcing the server itself to block the client.
The next point that raises doubts is the format of the “frame” with the data. It looks like this:
+————+———-+———+—————+————+————+ | 2 bytes | 16 bytes | 1 byte | 2 bytes | (optional) | (optional) | | Frame len. | Tag | Type | Payload len. | Payload | Padding | +————+———-+———+—————+————+————+ \_ Obfs. _/ \___________ NaCl secretbox (Poly1305/XSalsa20) ___________/ The first two bytes of each frame are the packet length, scaled with the key, which is calculated from the previous keys. How the key is calculated is not so important, the main thing is that the real length of the packet is subjected to a bitwise exclusive OR operation by some key. This means that you can invert a bit in this part of the data and the substitution will not be immediately noticed. If you invert the least significant bit of this field, the frame length will become either one less than the true one, or one more. In the first case, this will lead to the connection being reset after a short random time due to an error in unpacking the NaCl secretbox.
The second case is more interesting: the server will wait one more byte in order to start unpacking the cryptobox. Having received exactly one more byte, it will also reset the connection due to an error in unpacking the cryptobox. This behavior can be considered specific to obfs4 and we can judge that we are most likely dealing with it. Thus, by successfully destroying one of the client connections, you have approximately a 50% chance of detecting obfs4.
Of course, determining the boundaries of one frame in a stream can also be a difficult task, but there are no clear guarantees that it is unsolvable. In the case of short message exchange, the boundaries of one frame may coincide with the boundaries of a TCP segment.
Well, the last feature is that the protocol itself does not look like any of the generally accepted ones. It is designed with the assumption that DPI plays by the rules and simply does not touch unfamiliar protocols. Harsh reality may show that this is not the case.
For all these reasons I have refrained from using obfs4.
TLS and SSH as cryptographic transport
It would be reasonable to use standard secure network protocols like TLS or SSH to wrap connections with the proxy.
Indeed, there are usually no complaints from DPI about such protocols, because they can encrypt legitimate traffic. As for active probes on the DPI side, this issue can be resolved privately, depending on the specific proxy protocol. Below we will present several ready-made solutions based on these protocols, suitable for everyday ongoing traffic protection.
SOCKS5 inside SSH
The option of using OpenSSH's dynamic port forwarding function was discussed above, but it has big speed problems.
The only way to get rid of connection multiplexing is to use an alternative SSH client implementation that would provide each proxied connection with a separate SSH session. I did this kind of work and implemented it: Rapid SSH Proxy. This implementation provides each proxied connection with a separate SSH session, maintaining a pool of provisioned SSH sessions to satisfy incoming connection requests with minimal latency.
The procedure for working with it is the same as for ssh -ND 1080: a local SOCKS5 proxy is launched on the client side, accepting connections and forwarding them to the tunnel through the SSH server.
A key feature worth noting is that no third-party software needs to be installed on the server - rsp works as an ssh client with a regular OpenSSH server. The server can be any unix-like operating system, as well as Windows and Windows Server (in new versions OpenSSH is now available in system components).
Here's a comparison of speeds via a server in the USA:
| OpenSSH | rsp |
What is a proxy and how is it different from a VPN?
A proxy server is an intermediate device between a laptop (or other equipment) and an Internet resource. To bypass the blocking, the proxy server also changes the IP address, after which the geographic location of the device from which the Internet is accessed changes. Together with him, you can visit any country on the globe (Germany, France, Italy, etc.), however, only virtually and to bypass the blocking or remain anonymous (alas).
For example, if you want to log into VK, choose the geographic location of a country where it is not prohibited to use this social network. Russian IP is suitable for this purpose.
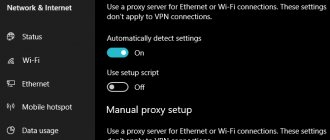
Installing and configuring a proxy will not take much effort and time, because everything happens quickly and “painlessly”. A proxy server can be installed both in the browser and on Windows. The second option will be more extensive, since the location changes in several browsers at once. Even a child can do the initial setup if you use our visual instructions with pictures.
Important! Russian proxies or any other country can be used on any device: laptop, tablet or phone.
When you first connect, you can use a free proxy. But, of course, it does not have such a high speed and is weakly protected compared to private, which can lead to loss of information. Therefore, it is recommended to use it temporarily.
Proxy servers that you can buy have many advantages:
- High speed Internet connection (does not load when bypassing restrictions);
- Customization for comfortable use;
- When resuming a lost Internet connection, you do not need to restart your browsers for the proxy server to work again (as is the case with a VPN);
- Carrying out any type of activity anonymously.
Of course, proxies also have disadvantages, but fortunately they are not serious, which is why you can turn a blind eye to this:
- There is no data encryption, the location is simply replaced;
- If you choose to connect to a prohibited site on the other side of the globe, the connection will probably not be as fast in this case (for example, if this is the USA). But, you can ask support for help, specialists will select the necessary addresses for a quick connection.
SOCKS5 inside TLS
In the case of TLS, the obvious solution would be to use stunnel or a similar TLS wrapper for TCP connections to the SOCKS5 server.
This actually works quite well, but the problem is that the TLS handshake for each new connection takes extra time and there is a noticeable delay when establishing new connections from the browser. This somewhat worsens the comfort when surfing the web. In order to hide this latency, I prepared a specialized stunnel replacement on the client that maintains a pool of already established, ready-to-request TLS connections. Even two - the first of them served as a prototype:
- Pooling TLS Wrapper
- steady-tun
As a server I offer two options:
- A combination of haproxy reverse proxy and dante SOCKS5 proxy, configured to protect against active probes from clients that have not passed certificate authentication: github.com/Snawoot/ptw/tree/master/docker_deploy
- My fork of go-socks5-proxy with built-in TLS support: github.com/Snawoot/socks5-server
HTTP proxy inside TLS aka HTTPS proxy
There is a little confusion regarding the combination of the words "HTTPS" and "proxy". There are two interpretations of this phrase:
- A regular HTTP proxy without encryption that supports the HTTP CONNECT method and through which HTTPS can successfully work.
- HTTP proxy that accepts TLS connections.
Let's talk about the second one.
All paid and free browser extensions that provide a “VPN” essentially configure the browser to use such a proxy. It is noteworthy that not a single browser has a simple option to set an HTTPS proxy in the settings through the user interface (the HTTPS proxy field that is there relates to the first case). But this does not present much difficulty.
After looking through various ready-made options, I decided to write my own HTTP(S) proxy server: dumbproxy.
The key feature of the resulting solution is that modern browsers (Firefox and the Chrome family, including the new MS Edge) can work with it without any additional software on the client (see the client setup guide).
It is worth noting the implementation features regarding counteraction to active samples from the DPI. An HTTP proxy can be easily recognized by connecting to it and attempting to make some kind of request to a third-party resource. If a proxy has authorization, then according to the standard it should reject the request with code 407, which is specific to an HTTP proxy, and offer a possible authorization scheme. If the proxy works without authorization, then it will fulfill the request, which will also give itself away. There are at least two ways to solve this problem (and both of them are implemented in dumbproxy).
The first way is to use client authentication using certificates at the TLS handshake stage. This is the most robust method, and is indeed a valid reason why any normal web server would reject a client.
The second method is to hide the 407 response code from unauthorized clients by returning any other error response instead. This causes another problem: browsers will not be able to understand that the proxy requires authorization. Even if the browser has a saved login and password for this proxy, the 407 response is important in determining the authorization scheme under which these credentials should be sent (Basic, Digest, etc.). To do this, you need to allow the proxy to generate a 407 response to the secret request so that the browser can remember the authorization scheme. A custom secret domain (not necessarily a real one) is used as such a secret request. By default this mode is disabled. Details can be found in the section on authentication.
How to Download and Install iNinja VPN & Proxy Extension in Google Chrome
Installing the plugin is completely free and can be done from the extension store. To install the iNinja extension in Google Chrome, go to the application store: https://chrome.google.com/webstore/category/extensions and search for [iNinja proxy].
On the page that opens, find the extension you need and click “Install”.
A pop-up window will appear asking you to confirm installation and give the extension access to manage site visit settings.
The installation process will begin, after which you will have a new icon in the top bar of your browser.
When you click on the icon, a menu will appear where you can enable or disable the use of a proxy server. Here you can select the geolocation that will be used when visiting sites.
You can check the change in IP address using our free service: https://socproxy.ru/ip.
In other browsers - Yandex.Browser, Safari, Mozilla Firefox and Opera, the extension cannot be installed.