Types of passwords
Currently, gadgets offer several options:
- graphic code;
- digital sequence;
- fingerprint, face, voice (if the device is equipped with this option);
- a combination of letters and numbers of different registers.
Most often we choose them based on patterns and stereotypes. This helps attackers hack the system. To prevent this from happening, read the instructions below.
On a note! The most common number sequences: “1234” - 10.7% of users; "1111" - 6%, "0000" - 1.9%. We strongly advise you not to fall into the statistical majority and take a more conscious approach to the security of your personal data.
How passwords are cracked
For brute force, there are programs into which a list of popular words and combinations (dictionary) is loaded. Such a list can be found in the public domain. The program substitutes combinations one by one, automatically, until it finds a working sequence.
How long will it take to select a combination?
Selecting a 4-character password does not present any difficulties for an attacker. In 2012, at a cybersecurity conference in Norway, a system capable of matching 348 billion hashes per second was demonstrated!
A hash is the transformation of information using a specific algorithm, which allows you to encode, store, and then restore this information.
If more complex hashing algorithms are used to store the codeword, for example, md5 combinations, then a sequence of 6 characters (letters of different case + numbers) can be selected in 95 minutes (speed of about 10 million sequences per minute). But in order to select a password of 10 characters, it will take more than two and a half thousand years.
Such values are achieved under ideal conditions: without restrictions on the number of attempts, and with maximum data exchange speed. In a real situation, hacking will take much longer
Passwords longer than 10 random characters are rarely cracked, because this will require hackers a lot of time and power, and why make such an effort if more than 10% of all sequences are variations of the numbers 12345 and the letters qwerty.
How passwords are cracked
Which passwords are weak?
A code consisting of letters in one case is extremely easy to crack. Especially if these are commonly used words, book titles, names of characters or events.
Complicating such combinations with the help of additional words will also not be enough: “This is my password” or “this is my cool password” will be guessed in the same amount of time.
How combinations leak into the network
First of all, less popular sites are hacked, without serious protection. Hackers make hacked accounts publicly available in order to enter all login+password combinations into dictionaries, using them in social networks, payment systems or email services.
Which password is harder to crack?
From a digital literacy perspective, the most secure password should contain the following attributes:
- be no shorter than 8 characters;
- contain letters and numbers;
- contain uppercase and lowercase characters;
- use punctuation marks.
When it comes to your phone password, there are a lot fewer options. Both the graphic and digital combination can be selected, guessed, or found out by the marks on the touchscreen. However, digital original sequences are still safer.
To find out the graphic password, just look closely at the surface of the smartphone screen. Usually the path of the unlocking curve can be recognized by oil marks and stains. They can be restored even from a surface that visually seems perfectly clean.
You can see the option for hacking a password on your phone at this link:
Rating of the most popular combinations
There have long been ratings of the most frequently used combinations on the Internet. According to statistics, its average length is from 6 to 8 characters.
In first place in the ranking are the number sequences and the first row of letters on the keyboard:
- 123456 and similar.
- Qwerty.
- Password
- ABC123.
- Superman, Sp1derm4n and other combinations of English words and numbers.
Rating of the most popular combinations
Combinations less than 4 characters or numbers long. Cracking such sequences is not difficult. The easiest way to gain access to an account is by brute force hacking.
What password can you put on your phone to make it easy to remember?
It should be noted that a password on the phone is not a serious protection against professional attackers. Rather, this is an option to delineate personal boundaries and block access to information among household members.
It is important to consider the correlation between the complexity of the key and the situation for entering it. Typically, the password on your phone should be easy to remember and enter fairly quickly. Otherwise, this option will begin to interfere with the use of basic functions of the device.
Memorable dates
One of the main requirements for a password is that it must be easy to remember. If you have forgotten the password for your gadget, problems may arise.
When creating digital passwords, the principle of choosing memorable dates is often chosen. It could be:
- birthday of the owner of the gadget or relatives;
- important event or event;
- public holiday and other date option.
There are special applications (for example, Screen Lock - Time Password) that allow you to set a dynamic password. Those. You will have to enter the current date or current time. The system will change the password automatically without user intervention.
Abbreviation
This is a good way to create a short, non-obvious password using letters. An abbreviation can be:
- Full Name;
- professional and author's abbreviation;
- mnemonic passwords (the first letters of words in a phrase).
Visual Key
Represents a sequence of strokes within a given grid of points. Only the correct sequential passage of all marks guarantees unlocking.
This type of password is interesting because it is difficult to guess. It is best suited for people with developed spatial thinking.
Terminology
If you understand the complex terminology of a particular industry, you can set the term as a password. The advantage of this method is that the word will be familiar and understandable to you. For attackers, it will not be obvious and difficult to find.
Any password has a degree of security. However, even the most complex combination will be cracked by automatic means and special programs.
Replacing characters
The option with character replacement is often used when one or more Latin letters can be inserted into a word in Russian. Considering that case sensitivity can also be set, the complexity of the password increases significantly.
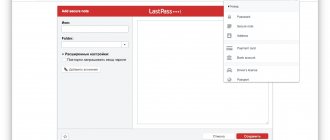
Password managers
Of the most famous multi-platform password managers, it should be noted:
- Managers in Chrome, Opera, Firefox browsers;
- lastpass;
- 1password;
- Dashlane;
- SafeInCloud;
- Other.
Passwords will be securely encrypted, and most applications are integrated with browsers. Every time a user logs into their mailbox or social network account, such applications will automatically fill in the login and saved password. Moreover, the combinations are synchronized and will be available from any user device.
Password manager Lastpass
How to work with a password manager in browsers
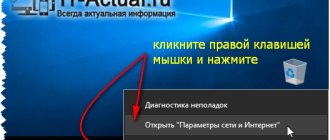
If autofill is enabled in the browser settings (this function can be accessed by going to the browser settings and opening the “passwords” or “autofill” menu), then every time the user gets to a site where he is required to log in, the browser will prompt him generate random symbols and save them in the manager.
How to set a password on your phone
In any smartphone, through the operating system, you can enter the “Security” menu, where, among other things, it is possible to set different types of passwords. Here are the most common ones.
Graphic password
A graphic key and its installation is a standard option of any modern operating system. The installation instructions in general boil down to the following steps:
- open the main settings menu;
- select the “Security” section;
- in the list that opens, look for the line “Screen lock”;
- find the “Graphic key” service;
- then the system will ask you to enter the author's path point by point;
- The correctness of the input is checked by repeating the route;
- the “Confirm” button completes the process of setting a graphic password.
After this, as soon as the phone goes into sleep mode and turns off the screen power, when you access the device again, you will be asked to enter a sequence that is the access key.
Pin
This code is a 4-character combination of numbers. The element is named by analogy with the PID code - a unique password for SIM cards. Installing this protection option will require the following:
- in the main settings menu we find the section that is responsible for system security;
- select the “Screen lock” option;
- Among the options, select the “PIN code” element;
- enter the desired sequence;
- repeat it again;
- We complete the password setting process by pressing the “Finish” button.
The “quick lock” and “shuffle buttons” functions will help increase the level of security and difficulty for hacking. However, you need to enter a password with such settings more often and more carefully, since the arrangement of numbers will change by default.
Digital password
A digital password longer than 4 characters, and also containing letters and symbols, can be set in the same section through the “Password” option. Installation occurs in a similar way. This is the most reliable and difficult to hack option.
How to come up with a strong password
A password of 10-12 characters in length, using capital letters, lowercase letters, numbers and special characters is considered very complex and the best:
- L2jh3d61e%Fh is an example of a complex and strong password.
- Superman1 or ivanov007 - these combinations are selected first.
Advice
You should not use a password that matches your login. To steal an account, such a link does not even have to be hacked.
There are several ways to come up with the best and most complex password:
- Open your text editor and hit the keys blindly. The resulting combination can be adjusted - change capital letters to capital letters, add special characters or numbers.
- Using a password generator
- Using password managers. Opera, chrome, Yandex and firefox browsers have built-in managers that not only store them in a secure form for each site, but also allow you to generate new, safe combinations.
Example of a complex password
Advice
When generating passwords, you should avoid using meaningful phrases or words. Changing the layout will also be unsafe - in a foreign segment of the Internet this can work, but most hackers on the RuNet work with both layouts.
How to remember an invented sequence
- Write it down on paper. The most unreliable way. There are many sites, so many combinations, pieces of paper are constantly getting lost. Entering a password one letter at a time takes a long time and is easy to make a mistake.
- Save on your computer as a text file. And to make it even easier for attackers, it is advisable to name the file “my_passwords” and place it in the root of the C:\ drive. It may be much more convenient to insert saved combinations than to rewrite them manually, but in this case there can be no question of any security.
- Use password managers. The optimal way to store data. There are applications for desktop PCs, smartphones and even cloud services with constant synchronization. (The password of all your passwords is .... the most important password in your life!)
Ways to protect your smartphone from hacking
You can protect your device from hacking using additional applications. However, the most reliable option is not to lose the device and always keep it with you.
Alexandra
I work in IT and device development. I believe that good instructions solve 90% of the problems. Open to questions and comments
Ask a Question
Question to the expert
Using which service can you set a dynamic password that will change every hour?
This will require an additional program. For example, Screen Lock - Time Password 1.2.7.
What is the maximum length of a phone password?
The default limit is from 4 to 17 characters.
Is it convenient to use a fingerprint scanner as a password?
This is quite a convenient feature. You can enter data about fingers on different hands (up to 5) into the program. To increase reliability, you can scan only one finger, for example, the little finger of your left hand.
What does Smart Lock mean?
This is a feature that makes locking comfortable. The point is to prevent the phone from being blocked under certain conditions (physical contact, verified location, face or voice scanner).
4.6 / 5 ( 25 votes)
Author
Alexandra
I work in IT and device development. I believe that good instructions solve 90% of the problems. Open to questions and comments
Rules for creating passwords
- Do not use the same link on different sites.
- Try not to use the same combinations on different sites.
- The most complex and persistent combinations should be used for the most important sites - payment systems, email accounts, with which you can reset passwords for payment systems, etc.
- Use a password manager.
Rules for creating passwords