Today we will talk about one of the most common types of viruses – a hidden miner. Let's learn how to find and remove it ourselves.
But before that, I would like to briefly talk about its origin and symptoms of infection.
What is a virus miner
The miner virus is somewhat similar to a Trojan horse. The principle of its operation is to get into the system and begin to waste computer resources, loading the processor or video card to 100% in order to generate income for the attacker. Income is calculated in a special cryptocurrency in the form of bitcoins.
It turns out that the developer makes money thanks to the power of your computer. In my opinion, this is completely unfair.
The latest modifications of the mining virus can contribute to the loss of personal data, disable the Windows operating system and open doors for the penetration of new threats.
You can fight it using two methods: manual and automatic; below we will look at both methods.
What is a hidden miner and how to detect it on a PC
A hidden miner is not an ordinary virus, but a complex program that uses your computer to mine cryptocurrencies.
Black or hidden mining refers to the extraction of digital currency by third parties through the use of the power of other people's PCs. To do this, virus miners are introduced into computers, and we will now tell you what they are.
Equipment is infected through downloading and installing files, unauthorized remote access, and sometimes through direct injection. Next, the PC is connected to the scammer’s mining farm, and the earned coins are sent to his wallet.
Spyware is installed in silent mode, and crypto mining is disguised as the operation of an OS service or does not show itself at all. The new generation of virus miners have the ability to remain unnoticed: when the load increases, they turn off so as not to slow down the computer and not reveal their presence.
At first glance, such software does not cause any particular harm to either the computer or its owner (with the exception of increased electricity bills). In fact, the presence of a shadow miner harms the operating system, “eats” the power of the PC, affects productivity, and most importantly, it can open access to personal data, including information about payment transactions and e-wallet passwords.
The most common hidden miner is Bitcoin miner, developed as a single tool for mining various cryptocurrencies on other people's computers. It consists of an unlimited number of nodes and loads the equipment at 90-100%. The mining process is accompanied by noticeable noise from the video card cooler. Bitcoin miner is simple in technical terms, cannot disguise itself and can be easily detected in the task manager, but there are also more “cunning” mining viruses:
- Bad Miner;
- Epic Scale
- Miner Gate.
How does infection occur?
Typically, infection occurs in several ways:
- Via browser. For example, when you visit an infected site, the miner can load directly into the system and begin to operate. The second option is that the miner virus acts only while you are on the infected resource, like a special script, but after it is closed, everything returns to normal.
- Through installing programs, downloading and opening various files. In this case, the threat penetrates Windows and only then begins its activity.
Based on the above points, we can conclude that in our time it is impossible to do without good antiviruses. Even if you are a very careful user, there is still a risk of infection. At the very least, you should have Windows 10 Defender enabled.
Types of hidden mining
There are two main types of hidden mining:
- With installation of the program on the PC. In this case, the miner program is secretly installed on the victim’s computer. It encrypts files and quietly uses the power of the processor and video card for mining. This process occurs continuously while the computer is turned on and connected to the network.
- Browser mining. In this case, hidden mining is launched only when the user goes to a site where the attackers have placed malicious code.
Of course, gaming PCs are of the greatest value to “shadow” miners, because they are most often assembled from the latest versions of hardware, but smartphones should not be overlooked. Modern models of mobile gadgets also have a lot of power, so attackers do not neglect them and actively distribute malicious mobile applications.
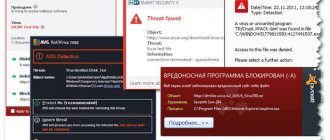
How to recognize a miner virus
There are several effective ways that will help you recognize the threat and take timely measures to eliminate it.
And so, it is necessary to check your computer for miners in the following cases.
- The device is constantly slowing down. When you open the task manager, you can see a graph of processor load up to 40-100%.
- Miner is capable of loading a video card. This can be seen when opening any program that displays the load percentage, such as GPU-Z. You can also determine the loading of the video card by hearing and touch. When overloaded, the cooler starts to spin faster and make noise; the card becomes hot when touched.
- Even less often, RAM consumption increases. This is also visible through Device Manager.
- High traffic consumption, loss or deletion of important files, periodic Internet shutdowns or PC slowdown when visiting a particular site.
- Periodically occurring Windows crashes or errors in installed programs.
I recommend checking for the presence of miners even if you have at least one of the above points.
How to prevent hidden mining
The program for removing miners is the last resort. Everyone's task is to learn how to prevent attempts to use the resources of your device for personal gain. To do this, just follow simple safety rules:
- Install only licensed software and try to avoid pirated content and resources.
- Limit the list of people who can access your PC. To do this, set a user password and block the ability of third parties to install software.
- Be sure to use a firewall on your PC and router, as well as licensed antivirus programs. The latter, by the way, need to be updated upon request.
- Avoid visiting dubious sites and those that operate without SSL certificates.
If the consumption of PC resources has increased sharply, then do not ignore the alarm signals. Hidden mining is not something out of science fiction, but a completely earthly threat hanging over millions of gullible PC users. Cases of hidden mining are growing exponentially. The antivirus company Malwarebytes recorded over 16 million attempts to illegally use user power in March last year alone.
Post Views: 883
Preparing for the test
Before you start scanning, you need to download and install antivirus applications.
Ideally, have an antivirus installed, even if it is a free version. In most cases, finding a miner hidden in the system will not be difficult for him.
The following programs will be useful to us
- Kaspersky Rescue Disk or Live Disk from Dr.Web. These are special emergency boot disks with a built-in anti-virus scanner. The main distinctive advantage of such disks is that when loading from such media, all existing viruses will be inactive, which means nothing will prevent them from being removed.
- Dr.Web Cureit is a special program that can detect and remove hidden miners, Trojans and other spyware.
- Malwarebytes Anti-Malware - will analyze the entire computer and get rid of threats that standard antiviruses usually do not see.
- Adwcleaner - will help you get rid of any infection from your browser. In my opinion, it is simply an irreplaceable thing.
- CCleaner is a utility for cleaning up Windows. It will effectively remove residual garbage from the system and correct registry entries.
After all the utilities have been downloaded and installed, you can proceed to the test.
Prevention methods
As they say, it is easier to avoid a problem than to solve it. But you won’t be able to completely protect yourself from miners. Any operating system involves installing all kinds of software and uninstalling it, which fills the registry and causes PC malfunctions. Even remote programs save separate files in the registry, which is why various viruses are masked. The right solution would be to use portable software. This will rid your registry of unnecessary clutter and free up your processor. Another useful program is WinPatrol Monitor. The application notifies about attempts of files to get into the registry without the user's knowledge.
ADVICE. Download content only from trusted sites!
To summarize, I would like to say the following: don’t waste your time on your computer! If you notice any changes in operation, do not be lazy to find out the reason. Many users prefer to simply lower the settings in their favorite game rather than try to understand why the game has become uncomfortable. All this is fraught with unpleasant consequences not only in terms of the OS, but also for the operation of the equipment itself. Have you encountered mining bots and how did you fight them? Describe your experience in the comments.
Scanning
Checking your computer for hidden miners should start with a standard antivirus installed on the system. Immediately after it, you can proceed to the programs strictly in the order indicated above in the previous section.
If you do not want to start scanning using a Live CD, then boot into safe mode (to minimize threat activity) and start from the second point. If the effect is insufficient, you must use a rescue disk.
Upon completion of the scan, remove the found mining viruses, clean them using the CCleaner program and restart your computer.
Manual detection method - task manager
The search for hidden miners can also be done manually. To do this, launch the “Task Manager” by pressing the “Ctrl+Shift+Esc” combination and go to the “Processes” section (in Windows 7) or “Details” (if you have Windows 10).
Then follow the instructions:
- You need to find the process that is using the most CPU resources. Most often, it has an incomprehensible name, consisting of a set of arbitrary letters or symbols.
- Next, open the registry by pressing the combination “Win + R” and entering “regedit”, click “OK”.
- Press “Ctrl+F”, enter the name of the process obtained in the first step and click “Find”.
- Thus, we search for and delete all entries that contain a command to launch a mining virus.
- Upon completion of the procedure, reboot the PC.
This was the first method, let's move on to the second.
Anvir Task Manager
If for some reason the task manager cannot be started, you can use an alternative method - the Anvir Task Manager program. You can download it from here.
- Install and launch the software.
- Find a suspicious process in the general list and hover over it with your mouse to see detailed information. Pay attention to all fields; there should be no dashes or arbitrary sets of characters or letters anywhere.
- Right-click and open the “Detailed Information” section.
- Move to the “Performance” tab and in the “Period” column set the value to “1 day”. It can be useful to conduct analysis in real time; to activate it, uncheck the previous item and place it next to the “Realtime” value.
- We analyze the activity, if it exceeded 20-30%, then remember the name of the process.
- By analogy with the previous method, open the registry editor, search by name and delete all mentions.
- We do the same with local disks.
- At the very end, it wouldn’t hurt to go through anti-virus utilities along with Ccleaner.
I hope that my instructions helped you get rid of hidden mining. If not, then you can describe your situation in the comments, and we will solve it together.
Step-by-step video to solve the problem
Find and delete
Having found out that hidden mining will not lead to any good, we move on to the “search and destroy” operation.
To begin with, it is recommended to run the standard process of scanning your computer with any sufficiently effective antivirus. It cannot be ruled out that in one case or another the user will encounter an ordinary and relatively safe miner. It does not hide its presence in the system, and therefore it can be easily detected through scanning and permanently deleted.
But practice shows that identifying a Trojan in a system is quite difficult. Malicious software developers do everything possible to ensure that the miner’s work is carried out as quietly as possible, but at the same time brings benefits. It’s just a pity that it didn’t happen to the injured party.
Modern miners hide their presence very well. They are capable of many things, including:
- turn off while the user is working with programs and applications that are particularly demanding;
- simulate the operation of other applications and standard processes when you launch the Task Manager;
- work only while the computer is idle, that is, the user does nothing.
That’s why it often turns out that a computer has been seriously infected for a long time, and the user doesn’t even know about it. This was made possible due to the careful work of hackers.
Botnets place a heavy load on your computer's processor.
But it is still possible to detect malware. And it is not necessary to contact specialized specialists for this.
ATTENTION. If you are not sure, you should not delete certain files. Especially system ones. Otherwise, this can lead to dire consequences, including damage to the OS with the need to reinstall it.
First you need to make sure that this is a malicious miner that is well camouflaged. And only after that can it be safely demolished.
You can implement your plans in 2 main ways. To do this, you should use the functionality of the Task Manager, or use a powerful system utility to check all active processes such as AnVir.
Task Manager
Many people have encountered Internet mining. And some don’t even know about it. There are websites on the Internet that use special scripts that allow you to access PC performance by bypassing protection. Having bypassed the security on the site, the hacker uploads malicious code to the resource. It starts mining when a user visits this site.
It is quite easy to guess and somehow understand that you have visited such a site. After all, when visiting it, the computer immediately begins to slow down greatly, and the Task Manager displays a high load on the computer hardware. Once you close the site, mining will stop and your computer will return to normal.
To detect malicious software that has entered your computer and system using Task Manager, you need to follow several steps:
- First, open the Task Manager itself. To do this, just press the key combination Ctrl, Shift and Esc at the same time.
- Now just watch. Literally 10 minutes. In this case, it is important that the computer is idle. Try not to even press anything on the keyboard or use the mouse.
- There are viruses that activate the dispatcher blocking, or simply close the window. This is done for a completely banal reason. This is how malware hides its presence. Therefore, if the dispatcher closes spontaneously, or when the system boots during inactivity, you can safely conclude that there is a miner on the computer.
- If nothing suspicious was found during monitoring, open the Details tab in the dispatcher window.
- In the list that opens, look for a process that is somehow different from all the others. This may include the use of strange symbols and other distinctive features. Rewrite its name.
- Now, through the Windows search engine, enter the word regedit and open the registry by launching this application. And it’s better to do it on behalf of the administrator.
- With Registry Editor open, click on the Edit tab in the top left corner and then click on the Find button. Enter here the name of the process that aroused your suspicions.
- When matches with this name are displayed in the list, right-click on them and click “Delete”. But if you are not sure that this is malware and not system important files, it is better not to touch anything.
- Start scanning your system with your antivirus. And here you can even use the built-in tool from Windows. To launch it, you need to click on “Start”, then go to the “Settings” section, then to “Update and Security”, and here you will find “Windows Defender”.
- Upon completion of the scan, the system will display a list of detected threats. Give permission to delete them.
Now all that remains is to restart the computer.
You should not rely solely on the built-in antivirus of the operating system. It will be better if you additionally run a scan with third-party software or even a utility like Dr.Web. The more effective the antivirus, the higher the likelihood of detecting hidden threats.
ADVICE. Before running a scan, update your antivirus to the latest version.
Malware can be quite recent, and an outdated antivirus simply does not know about it, and therefore it does not have the appropriate search and removal algorithms. By updating the program, it will certainly find this miner and neutralize it.
AnVir Task Manager
Many people perceive this program as anti-virus software. In fact, it is a useful system utility that can display all the processes on the computer.
With the help of this multifunctional process manager, you can quickly and easily find all hidden viruses and miners. You just need to take advantage of the opportunities offered correctly.
The sequence of procedures here will be as follows:
- First download the installation file. It is better to do this through the official website of the developer. Now install the process manager and run it.
- After a short scan, the window that opens will display all the processes currently running on your computer.
- The dispatcher himself has a special algorithm for determining the risk level. It is displayed as a percentage. But you shouldn't rely on it completely. When you see high-risk processes or suspicious names, move your mouse cursor over them. After this, detailed information will open.
- A number of Trojans are really good at camouflaging themselves, imitating system applications and processes. But the details give them away. It is through them that the real threat can be detected.
- Select one of the processes whose security you doubt. Right-click, click on “Detailed Information”, and then open the “Performance” tab.
- In the list on the left, check the “1 Day” option. Now look at the load on the computer during the specified period.
- If a suspicious process heavily loaded the system, move the mouse cursor to it, and then rewrite the name of the process itself, as well as the path to it.
- Next in the same process, right-click and select the option to complete the process.
- Again, enter regedit through the Windows search engine and launch Registry Editor. Through the “Edit” tab, click on “Find” and write down the values of suspicious processes.
- All matches with the file name are removed.
- Run an updated antivirus program for a full scan. If threats are found, remove them.
At the end, all that remains is to send the computer to reboot.
After this, check whether the situation has changed, whether the load on the system has decreased. If there are other suspicious processes, do the same with them.
Removing a miner from your computer
After checking for malware, we proceed to eliminate it. This can be done in several ways, including without the help of third-party programs for detecting miners. Important: delete manually only if you are absolutely sure that you have found exactly the miner.
- We try to find the file through Task Manager - Details or through the programs mentioned above for viewing PC processes.
- We close all kinds of processes, except those necessary for the operation of the OS. We check the remaining ones one by one. We are looking for a process with an incomprehensible set of random characters in the name.
- Having discovered a suspicious file masquerading as system updates, launch the search engine. Let's see what opens when you try to download a file.
- We find matches in the registry by pressing regedit and pressing Ctrl + F to search. Delete. You can additionally clean the registry using, for example, CCleaner.
- Reboot the PC and evaluate changes in load.
ATTENTION. Often miners are stored on the C drive in the users\user\appdata folder.
You can try using antivirus programs. Old versions, of course, will not correct the situation, but some have a sufficient set of utilities to find hidden miners. For example, Dr.Web CureIt, Kaspersky Virus Removal Tool or Junkware Removal Tool.
If you couldn’t find the miner, but you are sure that it exists, use the AVZ program. There you need to update and run “System Research”. As a result, you will receive an avz_sysinfo.htm file, with which you can go to the forum and ask for help from specialists. Perhaps you will get a script that runs through the same AVZ and thereby solve the problem. A regular reinstallation of the operating system will also help.