What is a ransomware virus?
The code itself, written in a self-copying virus, involves encrypting almost all user data with special cryptographic algorithms, without affecting the system files of the operating system.
At first, the logic of the virus’s impact was not entirely clear to many. Everything became clear only when the hackers who created such applets began demanding money to restore the original file structure. At the same time, the encrypted virus itself does not allow you to decrypt files due to its characteristics. To do this, you need a special decryptor, if you like, a code, a password or an algorithm required to restore the desired content.
How to set up ransomware protection in Windows 10?
We continue to build a deep, layered defense against ransomware viruses and not only ransomware. Files cannot be decrypted! And it is possible to restore their unencrypted versions. It's all about the settings. If you do this before the virus gets on your computer, it will be possible to restore the files.
The third line of defense is our computer. For a long time now, since 2003, Microsoft has been using “disk shadow copying” technology. For you and me, this means that any change to the system can be rolled back.
A “snapshot” of your hard drive is created in advance, automatically without your knowledge. And the system stores it, adding only changes. This technology is used to backup data. You just need to turn it on.
Depending on the disk size and settings, up to 64 previous “shadow copies” can be stored on the volume. If this option is enabled, then encrypted files can be restored from a shadow copy that is quietly created daily. First step - Go to This Computer - right mouse button "properties":
Extra options
Let’s open the “System Protection” tab. In the example, the protection option is disabled on one of the disks. Stand with the mouse on the selected drive and click “Configure”
Data can be restored from a copy from this window by clicking the “Restore” button
Make the settings as in the figure:
The next step is setting up User Account Control. By the way, virus epidemics practically do not affect Android and Linux devices. Why? Do attackers not notice them? They notice that viruses are being written intensively, but there is a completely different approach to security.
On Windows, you and I have to make the necessary settings ourselves. Microsoft (which means “small and delicate”), as part of its ideology, allows users to easily change them - for our convenience.
So easy and free that the virus, once in the “administrator” environment, already acts with administrator powers, nothing interferes with it. Hence the massive epidemics. I hope I convinced you. Everything is easy. Go to “user accounts”
Inside, click on the link “Change User Account Control Settings"
We move the slider as convenient for us.
Now, when you launch any program with your knowledge (or without yours), the system will ask you for permission and notify you. Small and delicate ones love such windows...
And if you have Administrator rights, then you can allow its execution. But if you are an ordinary user, you will not allow it. Hence, again, the conclusion is that it is best to have one password-protected Administrator account on your computer, and all the others should be ordinary users.
Of course, everyone has been familiar with this window for a long time, everyone is already tired of it, everyone turns it off. But, if User Account Control is enabled, it will prevent the malicious program from being executed even when directly connected to the computer remotely. Like this. But, of two evils, you have to choose the lesser. Who likes what. Here's another short video on this topic
The next step is to configure permissions and permissions for folders. For particularly important document folders, you can configure access rights for each such folder. In the properties of any folder (via the right mouse button - “Properties”) there is a “Security” tab.
For example, we have Users on our computer, let’s say these are our little children. We don't want them to be able to change the contents of this folder. Therefore, click “Change”.
Gray checkmarks are what is set by default. We can check the boxes and “ban” everything. Even viewing. You can ban a user group (as in the figure). You can “Add” a specific user. The virus will not be able to do anything if “change” or “write” permissions are denied in this folder. Try blocking writing, and then copying a file to such a folder.
And also, today we will consider such a measure of protection against viruses as file backup. For such a solution, you need to purchase and install in your computer in advance another hard drive with a capacity no less than that on which your Windows is installed. Then you need to set up archiving for it. In Control Panel there is a link to "Backup and Restore"
Having failed there we find ourselves in the settings:
Here's what they recommend to us:
I only have the “D” partition of my hard drive at hand right now. This is possible, but only for the first time. Later, you definitely need to buy yourself an external hard drive. Once you have chosen the archive location, click “Next”.
If you do not have a hard drive, we do everything as in the figure. In this case, only files in standard locations (My Documents, My Pictures Downloads, Desktop, etc.) will be saved. Click “Next”.
That's all, friends. The process has begun. Here is a video that tells you how to create a system image and restore a file from the image
So, to effectively protect against ransomware viruses, it is enough to be careful, preferably have a paid domestic antivirus and an operating system configured for normal security. “But how did the encryption virus get to you if you are so smart?” - the reader will ask me. I repent, friends.
All of the above settings were made to me. But, I turned everything off myself for about a couple of hours. My colleagues and I were remotely setting up a connection to a database that just didn’t want to be established.
It was decided to urgently use my computer as a test option. To make sure that the packets were not interfered with by the antivirus, network settings, and firewall, I quickly uninstalled the antivirus for a while and turned off user account control. Just everything. Read below to see what came of it.
The principle of penetration into the system and operation of the virus code
As a rule, it is quite difficult to “pick up” such crap on the Internet. The main source of spread of the “infection” is email at the level of programs installed on a specific computer terminal, such as Outlook, Thunderbird, The Bat, etc. Let us note right away: this does not apply to Internet mail servers, since they have a fairly high degree of protection, and access access to user data is possible only at the level of cloud storage.
Another thing is an application on a computer terminal. This is where the field for the action of viruses is so wide that it is impossible to imagine. True, it’s also worth making a reservation here: in most cases, viruses target large companies from which they can “rip off” money for providing a decryption code. This is understandable, because not only on local computer terminals, but also on the servers of such companies, not only completely confidential information can be stored, but also files, so to speak, in a single copy, which cannot be destroyed under any circumstances. And then decrypting files after a ransomware virus becomes quite problematic.
Of course, an ordinary user can be subject to such an attack, but in most cases this is unlikely if you follow the simplest recommendations for opening attachments with extensions of an unknown type. Even if an email client detects an attachment with a .jpg extension as a standard graphic file, it must first be scanned with a standard anti-virus scanner installed on the system.
If this is not done, when you open it by double-clicking (standard method), the activation of the code will start and the encryption process will begin, after which the same Breaking_Bad (encryptor virus) will not only be impossible to remove, but also the files will not be able to be restored after the threat is eliminated.
Paths of distribution of encrypting viruses
The main way malware gets onto the computers of private users and organizations is email, or more precisely, files and links attached to emails.
An example of such a letter intended for “corporate clients”:
The content of the letter prompts you to click on a link or launch a Trojan file. Attackers often use the following plots:
- “Repay your loan debt immediately.”
- “The claim has been filed in court.”
- “Pay the fine/fee/tax.”
- “Additional charge of utility bills.”
- “Oh, is that you in the photo?”
- “Lena asked me to urgently give this to you,” etc.
This is interesting: Buying a licensed antivirus in an online store.
Using the example of Kaspersky Internet Security and the softkey.ua store Agree, only a knowledgeable user would treat such a letter with caution. Most people, without hesitation, will open the attachment and launch the malicious program themselves. By the way, despite the cries of the antivirus.
The following are also actively used to distribute ransomware:
- Social networks (mailing from the accounts of friends and strangers).
- Malicious and infected web resources.
- Banner advertising.
- Mailing via messengers from hacked accounts.
- Vareznik sites and distributors of keygens and cracks.
- Adult sites.
- Application and content stores.
Encryption viruses are often carried by other malicious programs, in particular, advertising demonstrators and backdoor Trojans. The latter, using vulnerabilities in the system and software, help the criminal gain remote access to the infected device. The launch of the encryptor in such cases does not always coincide in time with potentially dangerous user actions. As long as the backdoor remains in the system, an attacker can penetrate the device at any time and initiate encryption.
To infect the computers of organizations (after all, more can be extracted from them than from home users), especially sophisticated methods are being developed. For example, the Petya Trojan penetrated devices through the update module of the MEDoc tax accounting program.
Encryptors with the functions of network worms, as already mentioned, spread across networks, including the Internet, through protocol vulnerabilities. And you can become infected with them without doing absolutely anything. Users of Windows operating systems that are rarely updated are at greatest risk because updates close known loopholes.
Some malware, such as WannaCry, exploit 0-day vulnerabilities, that is, those that system developers are not yet aware of. Unfortunately, it is impossible to fully resist infection in this way, but the likelihood that you will be among the victims does not even reach 1%. Why? Yes, because malware cannot infect all vulnerable machines at once. And while it is planning new victims, system developers manage to release a life-saving update.
General consequences of penetration of all viruses of this type
As already mentioned, most viruses of this type enter the system through email. Well, let’s say a large organization receives a letter to a specific registered email with contents like “We have changed the contract, scanned copy is attached” or “You have been sent an invoice for shipping the goods (a copy there).” Naturally, the unsuspecting employee opens the file and...
All user files at the level of office documents, multimedia, specialized AutoCAD projects or any other archival data are instantly encrypted, and if the computer terminal is located on a local network, the virus can be transmitted further, encrypting data on other machines (this becomes noticeable immediately after “braking” of the system and freezing of programs or currently running applications).
At the end of the encryption process, the virus itself apparently sends a kind of report, after which the company may receive a message that such and such a threat has penetrated the system, and that only such and such an organization can decrypt it. This usually concerns a virus. Next comes a requirement to pay for decryption services with an offer to send several files to the client’s email, which is most often fictitious.
The first time I encountered a virus that encrypts files was in early 2014.
An administrator from another city contacted me and told me the most unpleasant news - All files on the file server are encrypted! The infection occurred in an elementary way - the accounting department received a letter with the attachment “Act of something there.pdf.exe”, as you understand, they opened this EXE file and the process began... it encrypted all personal files on the computer and went to the file server (it was connected network drive). The administrator and I started digging for information on the Internet... at that time there was no solution... everyone wrote that there was such a virus, it was not known how to treat it, the files could not be decrypted, perhaps sending the files to Kaspersky, Dr Web or Nod32 would help. You can only send them if you use their anti-virus programs (licensed). We sent the files to Dr Web and Nod32, the results were 0, I don’t remember what they said to Dr Web, and Nod 32 was completely silent and I didn’t get any response from them. In general, everything was sad and we never found a solution; we restored some of the files from backup. The second story - just the other day (mid-October 2014) I received a call from an organization asking me to solve a problem with a virus; as you understand, all the files on the computer were encrypted. Here's an example of what it looked like.
As you can see, the extension *.AES256 was added to each file. In each folder there was a file “Attention_open-me.txt” which contained contacts for communication.
When trying to open these files, a program with contacts opened to contact the authors of the virus to pay for decryption. Of course, I do not recommend contacting them, or paying for the code either, since you will only support them financially and it is not a fact that you will receive the decryption key.
The infection occurred during the installation of a program downloaded from the Internet. The most surprising thing was that when they noticed that the files had changed (icons and file extensions had changed), they did nothing and continued to work, while the ransomware continued to encrypt all files.
Attention!! ! If you notice encryption of files on your computer (change in icons, change in extension), immediately turn off your computer/laptop and look for a solution from another device (from another computer/laptop, phone, tablet) or contact IT specialists. The longer your computer/laptop is turned on, the more files it will encrypt.
In general, I already wanted to refuse to help them, but I decided to surf the Internet, maybe a solution to this problem had already appeared. As a result of searching, I read a lot of information about things that cannot be decrypted, that you need to send files to antivirus companies (Kaspersky, Dr Web or Nod32) - thanks for the experience. I came across a utility from Kaspersky - RectorDecryptor. And lo and behold, the files were decrypted. Well, first things first...
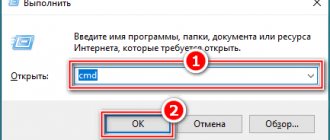
The first step is to stop the ransomware. You won’t find any antiviruses, because the installed Dr Web didn’t find anything. First of all, I went to startup and disabled all startups (except antivirus). Rebooted the computer. Then I started looking at what kind of files were in startup.
As you can see in the “Command” field it is indicated where the file is located, special attention needs to be removed for applications without a signature (Manufacturer - No data). In general, I found and deleted the malware and files that were not yet clear to me. After that, I cleared temporary folders and browser caches; it is best to use CCleaner .
Another way to roll back the system before the problem occurred .
Next, I started decrypting the files, for this I downloaded the decryption program RectorDecryptor . I launched it and saw a rather ascetic interface of the utility.
I clicked “Start scanning” and indicated the extension that all changed files had.
And indicated the encrypted file. In newer versions of RectorDecryptor you can simply specify the encrypted file. Click the "Open" button.
Tada-a-a-am!!! A miracle happened and the file was decrypted.
After this, the utility automatically checks all computer files + files on the connected network drive and decrypts them. The decryption process may take several hours (depending on the number of encrypted files and the speed of your computer).
As a result, all encrypted files were successfully decrypted into the same directory where they were originally located.
All that remains is to delete all files with the .AES256 extension; this could be done by checking the “Delete encrypted files after successful decryption” checkbox if you click “Change scan parameters” in the RectorDecryptor window.
But remember that it is better not to check this box, because if the files are not successfully decrypted, they will be deleted and in order to try to decrypt them again, you will have to first restore .
When I tried to delete all encrypted files using standard search and delete, I encountered freezes and extremely slow operation of the computer.
Therefore, to remove it, it is best to use the command line, run it and write del “<drive>:\*.<encrypted file extension>” /f /s . In my case del "d:\*.AES256" /f /s.
Don’t forget to delete the “Attention_open-me.txt” files; to do this, in the command line, use the command del “<drive>:\*.<file name>” /f /s, for example del “d:\ Attention_open-me. txt" /f /s
Thus, the virus was defeated and the files were restored. I want to warn you that this method will not help everyone, the whole point is that Kapersky in this utility has collected all the known decryption keys (from those files that were sent by those infected with the virus) and uses a brute force method to select the keys and decrypt them. Those. if your files are encrypted by a virus with an unknown key, then this method will not help... you will have to send the infected files to antivirus companies - Kaspersky, Dr Web or Nod32 to decrypt them.
If you know other ways to combat a virus that encrypts files, please share them in the comment.
I really hope my article helped you! Please share the link with your friends:
Harm from exposure to code
If anyone hasn’t realized yet: decrypting files after a ransomware virus is a rather labor-intensive process. Even if you don’t give in to the demands of the attackers and try to involve official government agencies in combating and preventing computer crimes, usually nothing good comes of it.
If you delete all files, perform a system restore, and even copy the original data from removable media (of course, if there is a copy), everything will still be encrypted again if the virus is activated. So you shouldn’t delude yourself too much, especially since when you insert the same flash drive into a USB port, the user won’t even notice how the virus will encrypt the data on it too. Then you won't have any problems.
Description of the Crusis (Dharma) ransomware virus
Then the investigation began. Encrypted files received the extension .combo . There were a lot of them. The cryptographer began working late in the evening, at approximately 11 p.m. We were lucky - the backup of the affected disks had just been completed by this time. The data was not lost at all, since it was backed up at the end of the working day. I immediately started restoring from the backup, which is on a separate server without SMB access.
Overnight, the virus managed to encrypt approximately 400 GB of data on network drives. The banal deletion of all encrypted files with the combo extension took a long time. At first I wanted to delete them all at once, but when just counting these files lasted for 15 minutes, I realized that it was useless at this point in time. Instead, I started downloading the latest data, and cleaned the disks of encrypted files after.
I’ll tell you the simple truth right away. Having up-to-date, reliable backups makes any problem solvable. I can’t even imagine what to do if they are not there or they are not relevant. I always pay special attention to backups. I take care of them, I cherish them, and I don’t give anyone access to them.
After I launched the recovery of encrypted files, I had time to calmly understand the situation and take a closer look at the Crusis (Dharma) encryption virus. Surprises and surprises awaited me here. The source of infection was a virtual machine running Windows 7 with an rdp port forwarded through a backup channel. The port was not standard - 33333. I think it was the main mistake to use such a port. Although it is not standard, it is very popular. Of course, it’s better not to forward rdp at all, but in this case it was really necessary. By the way, now, instead of this virtual machine, a virtual machine with CentOS 7 is also used; it runs a container with xfce and a browser in Docker. Well, this virtual machine has no access anywhere, only where it is needed.
What's scary about this whole story? The virtual machine was updated. The cryptographer started working at the end of August. It is impossible to determine exactly when the machine was infected. The virus wiped out a lot of things in the virtual machine itself. Updates to this system were installed in May. That is, there should not be any old open holes on it. Now I don’t even know how to leave the rdp port accessible from the Internet. There are too many cases where this is really needed. For example, a terminal server on rented hardware. You won’t also rent a VPN gateway for each server.
Now let’s get closer to the point and the ransomware itself. The network interface of the virtual machine was disabled, after which I started it. I was greeted by a standard sign, which I had already seen many times from other cryptographers.
All your files have been encrypted! All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail Write this ID in the title of your message 501BED27 In case of no answer in 24 hours write us to theese e-mails: [email protected] You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files. Free decryption as guarantee Before paying you can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.) How to obtain Bitcoins The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price. https://localbitcoins.com/buy_bitcoins Also you can find other places to buy Bitcoins and beginners guide here:
How Can I Buy Bitcoin?
Attention!
Do not rename encrypted files. Do not try to decrypt your data using third party software, it may cause permanent data loss. Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam. On the desktop there were 2 text files named FILES ENCRYPTED.TXT with the following content:
all your data has been locked us Do you want to return? write email
It is curious that the rights to the Desktop directory have changed. The user did not have write permissions. Apparently, the virus did this to prevent the user from accidentally deleting information in text files from the desktop. There on the desktop there was a directory troy , which contained the virus itself - the file l20VHC_playload.exe .
Firstborn in the family
Now let's turn our attention to the first encryption virus. At the time of its appearance, no one had yet thought how to cure and decrypt files after being exposed to an executable code contained in an email attachment with a dating offer. Awareness of the scale of the disaster came only with time.
That virus had the romantic name “I Love You”. An unsuspecting user opened an attachment in an email message and received completely unplayable multimedia files (graphics, video and audio). Back then, however, such actions looked more destructive (harm to user media libraries), and no one demanded money for it.
How does a ransomware virus get onto a computer?
Virus files are retrieved through Internet links and email. And then further on the local network (if the security settings are not made). Emails containing a virus contain attachments or a link to the downloader of the virus itself.
To disguise the attachment, it is almost always sent in an archive. Therefore, first we will check the unusual letter with an antivirus. You need to save the file to your computer (the antivirus will already “look” at it). And then additionally right-click on the file saved on disk and check again:
When you click on a suspicious Internet link or email (again, in the case of a paid version of the antivirus installed), the system displays the following useful window:
The site is in the non-recommended database. This means that there have already been “alarm calls” from him. Also, paid versions check the Internet more effectively - links to viruses “hardwired” into them - than free ones. And when you click on such a link, they neutralize the virus, or add it to the “suspicious” list and block its execution.
At the end of March, I used these simple methods to catch another “quarterly” encryption virus from the mail. The only thing he managed to do was write me a message all over the computer that the files were encrypted, but this was not the case. They remained intact, the code worked only to create a message:
Please note that the email address of a certain Vladimir Shcherbinin, born in 1991, is indicated here. Generation of the 90s... This is a false trail, because the real address is below. The Tor browser allows an attacker to avoid tracking your computer on the Internet using standard means. Through such a browser, the attacker invites you to contact him. Everything is anonymous. Nobody wants to sit in prison.
Unfortunately, it often happens that sometimes viruses bypass our first two lines of defense. In our haste, we forgot to scan the file, or maybe the antivirus has not yet received data about the new threat. But you can configure protection in the operating system.
The newest modifications
As we see, the evolution of technology has become quite a profitable business, especially considering that many managers of large organizations immediately run to pay for decryption efforts, without thinking at all that they could lose both money and information.
By the way, don’t look at all these “wrong” posts on the Internet, they say, “I paid / paid the required amount, they sent me a code, everything was restored.” Nonsense! All this is written by the developers of the virus themselves in order to attract potential, excuse me, “suckers.” But, by the standards of an ordinary user, the amounts to pay are quite serious: from hundreds to several thousand or tens of thousands of euros or dollars.
Now let's look at the newest types of viruses of this type, which were recorded relatively recently. All of them are practically similar and belong not only to the category of encryptors, but also to the group of so-called ransomware. In some cases, they act more correctly (like paycrypt), seemingly sending official business offers or messages that someone cares about the security of the user or organization. Such an encrypting virus simply misleads the user with its message. If he takes even the slightest action to pay, that’s it – the “divorce” will be complete.
XTBL virus
The relatively recently appeared XTBL virus can be classified as a classic version of ransomware. Typically, it enters the system through email messages containing attachments in the form of files with the .scr extension, which is the standard for Windows screensavers. The system and user think everything is fine and activate viewing or saving the attachment.
Unfortunately, this leads to sad consequences: the file names are converted into a set of characters, and .xtbl is added to the main extension, after which a message is sent to the desired email address about the possibility of decryption after paying the specified amount (usually 5 thousand rubles).
The virus has encrypted files on a Windows 10 computer, what to do, how to cure it and how to fix it?
This is what our would-be hackers have not yet managed to get to. The last line of defense. Present only in Windows 10, I haven’t checked it yet, but I think the “seven” and “eight” do not have this new wonderful feature. I noticed her recently. This is a truly new and exciting feature. In the search bar we hit the word “recovery”
In Control Panel, click "Recover Files Using File History"
I was delighted and immediately went, of course, to “Documents” and “Desktop”.
And I saw that the files were not encrypted. Hooray! “Thank you Green Arrow! The process has begun. The files have been restored. The computer has been cured of viruses. Security settings are done. What else is left to do?
You also need to delete encrypted files. You never know... But there are very, very many of them. How to quickly find and remove them? I have been using the Total Comander file manager for a long time. For my taste there is nothing better. Anyone who started with Far Manager will understand me. Tonal can quickly search files, and much more. We will clean the disks one by one.
Let's start with the system partition, select it by clicking the mouse or from the drop-down list in the upper left corner:
Press Alt + F7 on the keyboard simultaneously. We called up the file search panel.
You can search by name. You can do whatever you want. But we will use a mask. That is, we indicate the extension of the encrypted file *.freefoam through an asterisk and a dot (your “author” may be different, and the extension will be different). By this we indicated that ALL files with this extension need to be searched. Search location "C:". You can also specify all sections in this panel, not just “C:”. Click “Start Search”.
The search is over. Next, click “Files to panel”.
By pressing the “star” on the side keyboard, we highlight all the files in the panel in pink. To delete files to the trash, press F8 or Del:
We cleaned out all the remaining encrypted garbage like a vacuum cleaner. Let it sit in the basket for now. Then I'll delete it. In the same way, I cleaned all the sections one by one in about forty minutes. I have a lot of things encrypted.
But I was lucky, because it can happen worse. This new feature literally saved me. I'm not sure if enabling shadow copies affects this new feature. It looks like yes, but I haven't specifically checked. Somehow I don’t want to anymore :)
Write if you know. And the following conclusions can be drawn. If you have a good antivirus and correctly configure the Windows 10 operating system, you can wipe the attacker’s nose and leave him with nothing. Bye, friends.
Author of the publication
offline for 5 days
CBF virus
This type of virus also belongs to the classics of the genre. It appears on the system after opening email attachments, and then renames user files, adding an extension like .nochance or .perfect at the end.
Unfortunately, decrypting a ransomware virus of this type to analyze the contents of the code even at the stage of its appearance in the system is not possible, since after completing its actions it self-destructs. Even what many believe is a universal tool like RectorDecryptor does not help. Again, the user receives a letter demanding payment, for which two days are given.
Breaking_Bad virus
This type of threat works in the same way, but renames files in the standard version, adding .breaking_bad to the extension.
The situation is not limited to this. Unlike previous viruses, this one can create another extension - .Heisenberg, so it is not always possible to find all infected files. So Breaking_Bad (a ransomware virus) is a fairly serious threat. By the way, there are cases where even the Kaspersky Endpoint Security 10 license package misses this type of threat.
Virus
Here is another, perhaps the most serious threat, which is mostly aimed at large commercial organizations. As a rule, some department receives a letter containing seemingly changes to the supply agreement, or even just an invoice. The attachment may contain a regular .jpg file (like an image), but more often it may contain an executable .js script (Java applet).
How to decrypt this type of encryption virus? Judging by the fact that some unknown RSA-1024 algorithm is used there, no way. Based on the name, you can assume that this is a 1024-bit encryption system. But, if anyone remembers, today 256-bit AES is considered the most advanced.
Encryptor virus: how to disinfect and decrypt files using antivirus software
To date, no solutions have yet been found to decipher threats of this type. Even such masters in the field of antivirus protection as Kaspersky, Dr. Web and Eset cannot find the key to solving the problem when the system is infected with an encrypting virus. How to disinfect files? In most cases, it is suggested to send a request to the official website of the antivirus developer (by the way, only if the system has licensed software from this developer).
In this case, you need to attach several encrypted files, as well as their “healthy” originals, if any. In general, by and large, few people save copies of data, so the problem of their absence only aggravates an already unpleasant situation.
File recovery methods
If system protection has been enabled on your computer, then even after the effect of a ransomware virus there is a chance to return files to their normal state using shadow copies of files. Ransomware usually tries to remove them, but sometimes they fail to do so due to lack of administrator rights.
Restoring a previous version:
- Right-click on the encrypted file and open its properties.
- Then go to the “Previous Versions” tab. Select the shadow copy and click Restore.
In order for previous versions to be saved, you need to enable system protection.
Important: system protection must be enabled before the ransomware appears, after which it will no longer help.
- Open Computer properties.
- From the menu on the left, select System Protection.
- Select drive C and click "Configure".
- Choose to restore settings and previous versions of files. Apply the changes by clicking "Ok".
If you took these steps before the file-encrypting virus appeared, then after cleaning your computer from malicious code, you will have a good chance of recovering your information.
Possible ways to identify and eliminate the threat manually
Yes, scanning with conventional antivirus programs identifies threats and even removes them from the system. But what to do with the information?
Some try to use decryption programs like the already mentioned RectorDecryptor (RakhniDecryptor) utility. Let us note right away: this will not help. And in the case of the Breaking_Bad virus, it can only do harm. And that's why.
The fact is that people who create such viruses are trying to protect themselves and provide guidance to others. When using decryption utilities, the virus can react in such a way that the entire system crashes, with the complete destruction of all data stored on hard drives or logical partitions. This, so to speak, is an indicative lesson for the edification of all those who do not want to pay. We can only rely on official antivirus laboratories.
Cardinal methods
However, if things are really bad, you will have to sacrifice information. To completely get rid of the threat, you need to format the entire hard drive, including virtual partitions, and then install the operating system again.
Unfortunately, there is no other way out. Even rolling back the system to a specific saved restore point will not help. The virus may disappear, but the files will remain encrypted.
Instead of an afterword
In conclusion, it is worth noting that the situation is this: a ransomware virus penetrates the system, does its dirty work and is not cured by any known means. Anti-virus protection tools were not ready for this type of threat. It goes without saying that it is possible to detect a virus after exposure or remove it. But the encrypted information will remain unsightly. So I would like to hope that the best minds of antivirus software development companies will still find a solution, although, judging by the encryption algorithms, it will be very difficult to do. Just remember the Enigma encryption machine that the German Navy had during World War II. The best cryptographers could not solve the problem of an algorithm for decrypting messages until they got their hands on the device. This is how things are here too.