PGP Desktop is a program that allows you to encrypt documents and data of special confidentiality. The software will securely encrypt information using modern algorithms. PGP Desktop is suitable for users who are afraid of losing important documents. The program will take care of the security of your data and save it on your computer or laptop.
With the software, you protect documents and data with extreme precision. You will protect not only folders and special files located on your hard drive, but also email communications.
Functional
PGP Desktop for regular users is designed with the fewest features and lacks most features.
For the software to fully work for personal purposes, the user will have to use the purchased version. Remember that the trial version does not have all the elements that allow you to protect all the data on your computer. Complete information protection is only available with all encryption algorithms that hide folders and files from prying eyes.
The professional version of the program protects your computer from hacking and the entry of other users by providing encryption of folders, files, and mail. Using this software, you will generate “protected” disks in virtual mode. If necessary, you can use a special trash bin that allows you to delete files without recovery. Don't forget that the core PGP tools are very extensive. The creators have made a help that shows all the data on the issue you are interested in.
PGP encryption
PGP uses “public key cryptography,” which means that you need two keys—a public and a private—to encrypt and decrypt messages. The public key is used to encrypt data, and the private key is used to decrypt it.
Imagine someone putting their message in a box before sending it to you. This 'encryption' box has two locks, and the sender must use the public key to 'lock' this box. You can share your public key with an individual user or upload it to key sharing servers. The public key then encrypts the message so that no one, not even the sender, can decrypt it.
Your public and private keys are linked in such a way that now only the combination of these two keys can unlock the box (decrypt the message). You are the sole owner of the private key, so only you can decrypt the message. And you should also never share your private key with anyone.
Is PGP encryption secure?
PGP encryption uses 128-bit keys, which makes it quite difficult to crack. In other words, there are 2^128 possible combinations that someone could try before they break the encryption and read your message.
For the attack to be successful, the hacker would need a computer capable of running a billion keys every second. Even if such a supercomputer existed, it would still take more than 10,000,000,000,000 years to test all the possibilities. Thus, PGP users can feel quite secure using this encryption standard.
Why use PGP?
1. To encrypt email messages
PGP is widely used to encrypt mail messages. There are several plugins that you can install on your Gmail account to encrypt your messages. Some will encrypt your messages automatically, while others will require manual configuration. However, these plugins do not encrypt your attachments or other sensitive information such as the subject line or email address.
Instead, you can choose a reliable email service provider with built-in PGP encryption. This means that your email will be encrypted automatically. Some even offer additional features such as anonymous registration, anonymous payment, or even “email address rewriting.”
2. Use of digital signatures
Your key can also be used to digitally sign documents you send over the Internet to prove they are truly yours.
For example, imagine sending a book to your best friend. You encrypt the document with their public key and sign it with your private key. As soon as he receives the book, he will know that it came from you and no one else. If for some reason someone intercepted the document and changed something - even just one letter or number - your friend will see an invalid digital signature.
Bitcoin wallets can also be signed with the developer's private key. The digital signature ensures that these pre-compiled wallets do not hide any malicious code that could steal your cryptocurrency or other sensitive information.
Legal aspects of use in Russia
To date, there are no direct legislative prohibitions on the use of PGP in Russia. The use of cryptography is limited by law only in state and municipal institutions. The FSB orders all government agencies to use only certified cryptography tools. Individuals and companies themselves determine what information is a trade secret for them, methods of storing and transmitting such information[9] The information resource Helpdesk24 in the article “Legality of using cryptographic means of information security” provides excerpts from federal laws explaining this issue.[1] Also, the authors of the “openPGP in Russia” project claim that there are no laws prohibiting the use of PGP[10]. An electronic signature generated using PGP and its uncertified analogues has legal force in the Russian Federation, since, according to paragraph 3 of Article 5 of 63-FZ “On Electronic Signatures”[11], it falls under the definition of an enhanced unqualified electronic signature.[12] According to paragraph 2 of Article 6 of this Federal Law, recognition of such electronic signature requires an agreement between the participants in electronic interaction.
How PGP works
PGP encryption is carried out sequentially by hashing, data compression, symmetric key encryption, and finally public key encryption, each step can be carried out by one of several supported algorithms. Symmetric encryption is performed using one of seven symmetric algorithms (AES, CAST5, 3DES, IDEA, Twofish, Blowfish, Camellia) on the session key. The session key is generated using a cryptographically secure pseudo-random number generator. The session key is encrypted with the recipient's public key using RSA or Elgamal algorithms (depending on the recipient's key type). Each public key corresponds to a username or email address. The first version of the system was called the Web of Trust and was opposed to the X.509 system, which used a hierarchical CA-based approach added later to PGP. Modern versions of PGP include both methods.
Keys
Main article: Public key cryptosystem
The PGP user creates a key pair: a public and private key. When generating keys, their owner (name and email address), key type, key length and validity period are specified. The public key is used to encrypt and verify the digital signature. Private key - for decoding and creating a digital signature.
PGP supports three types of keys: RSA v4, RSA legacy (v3) and Diffie-Hellman/DSS (Elgamal in GnuPG terminology).
For RSA legacy keys, the key length can be from 1024 to 2048 bits, and for Diffie-Hellman/DSS and RSA - from 1024 to 4096. RSA legacy keys contain one key pair, and Diffie-Hellman/DSS and RSA keys can contain one master key and additional keys for encryption. In this case, the electronic signature key in Diffie-Hellman/DSS keys always has a size of 1024. The validity period for each type of key can be defined as unlimited or until a specific date. A secret phrase is used to protect the key container.
Digital signature
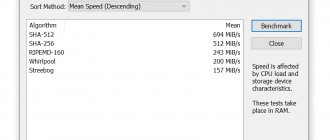
PGP supports authentication and integrity checking through a digital signature. By default it is used in conjunction with encryption, but can also be applied to plaintext. The sender uses PGP to create a signature using the RSA or DSA algorithm. This first creates a plaintext hash (also known as a digest), then digitally signs the hash using the sender's private key. The algorithms MD5, SHA-1, RIPEMD-160, SHA-256, SHA-384, SHA-512 can be used to generate a hash. Newer versions of PGP support MD5 to maintain compatibility with earlier versions. The RSA or DSA algorithms are used for signing (depending on the key type).
Data compression
To reduce the size of messages and files and possibly make cryptanalysis more difficult, PGP compresses data before encryption. Compression is performed using one of the ZIP, ZLIB, BZIP2 algorithms. Compressed, short, and weakly compressible files are not compressed.
Network of trust
Main article: Web of trust
Both when encrypting messages and when verifying a digital signature, it is necessary that the public key accepted by the recipient actually belongs to the sender. By simply downloading a public key, it can be replaced. Since the first versions, PGP has supported public key certificates, with the help of which substitutions (or accidental transmission errors) are easily recognized. However, it is not enough to simply create a certificate that is protected from modification, since this only guarantees the integrity of the certificate after it is created. Users must also have some way to verify that the public key in the certificate actually belongs to the sender. Since the first versions, PGP products have included an internal certificate verification scheme called the web of trust. A given username-public key pair can be signed by a third party that verifies that the key matches the owner. Such signatures may have multiple nested levels of trust. Although many programs read and write this information, very few take this certificate level into account when deciding whether to accept or reject a certificate.
The Web of Trust protocol was first described by Zimmermann in 1992 in the PGP version 2.0 manual: “Over time, you will accumulate the keys of other people, whom you can call trusted recommenders. Anyone else can choose their trusted recommenders. And everyone will gradually accumulate and distribute with their keys a set of other people's verified signatures, with the expectation that any recipient trusts at least one or two signatures. This allows us to create a decentralized, fault-tolerant network of all public keys.”
The web of trust mechanism has advantages over centralized public key management infrastructures such as those used in S/MIME, but is not widely adopted. Users wanted to check the validity of certificates manually or not check at all.
Certificates
In the latest OpenPGP specifications, trusted signatures can be used to support the creation of certificate authorities. Certificate trust means that the key actually belongs to the specified owner and can be used to sign certificates one level below. A Level 0 certificate means a normal signature. Level 1 means that a signed key can be used to create Level 0 certificates. A Level 2 certificate can be used to create Level 1 certificates. Level 2 is almost identical to the degree of trust with which users rely on trust lists built into browsers.
All versions of PGP include a method for revoking a certificate. This is necessary if you want to maintain the security of communications if the private key is lost or compromised. Certificate revocation is similar to certificate revocation lists in a centralized public key infrastructure. Modern versions of PGP also support certificate expiration dates.
The problem of correctly determining whether a public key belongs to the owner is typical for all cryptographic systems with asymmetric encryption. She doesn't have good enough solutions. The original PGP scheme allows the user to decide whether to use a certificate verification scheme, while most other public key infrastructures require verification of each certificate.
Cryptographic Applications PGP Corporation
PGP was originally developed for client-side email encryption, but since 2002 it also includes encryption of laptop hard drives, files and directories, instant messaging program sessions, batch file transfers, protection of files and directories in network storage, and in modern versions - It also encrypts HTTP requests and responses on the server side (mod openpgp) and client side (Enigform).
Client programs are combined into the PGP Desktop family (including PGP Desktop EMail, PGP Whole Disk Encryption and PGP NetShare).
PGP Universal Server allows you to centrally administer PGP Desktop-based clients from the command line.
In 2010, the rights to the application were acquired by Symantec for $300 million.[8]