There is no perfect protection - there are only different degrees of reliability. This also applies to iPhones.
We recently explained how important it is to have an alphanumeric lock password rather than the standard 6-digit one in iOS. But this is just the tip of the iceberg, and underneath is real hardcore.
We'll tell you how to bypass iPhone blocking methods and whether you can protect yourself from this.
Disclaimer: This article is not intended to help unlock stolen iPhones. You can test all the methods described below at your own risk.
How the password protection system works in iOS, briefly
If you enter the wrong password 10 times, the device will be locked. After the first 5 attempts you will have to wait 1 minute, then the time until the next entry attempt will increase.
If you realize that you can no longer remember the password, Apple suggests erasing all data from the device. This is quite OK if you have a backup. Read about three simple ways to save data here.
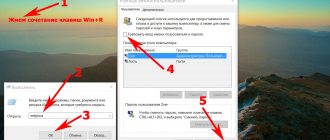
You can only remove a password from an iPhone or iPad using a computer. Instructions on the Apple website. If you don’t have a PC, you can contact an authorized service center or retail store, they will provide it.
How to unlock a found iPhone with a blocked Apple Id function
While restoring an iPhone that is protected by a code is quite simple, the Apple ID feature is much more complicated. This password cannot be hacked if the user does not have an email account to which the account is linked.
This blocking occurs on the Apple server itself. The device is marked as locked, and its further use is possible only after entering the appropriate data.
There are several options for solving this problem, but all of them are suitable only under certain conditions. Thus, the user will be able to restore a fourth iPhone that has operating system version 7.0 or lower. To do this, you need to reset your phone to factory settings and use the following sequence of actions:
- Start the device and follow the instructions displayed on the screen.
- Go to the window that requests data from your Apple ID.
- Go to emergency calls and dial 112. After the call, press the lock button once.
- After unlocking, go to contacts and create a new empty contact.
- Press the “Home” button three times.
- Go to contacts and block the created contact. After that, unlock it and block it again.
After this, you can use your smartphone. However, not all of its functions will be available. In addition, this sequence of actions does not guarantee a 100% result.
More details about this method can be seen in the video.
iOS password protection works worse in DFU mode
DFU (device firmware update) is a special mode that gives access to the engineering menu, allows you to restore the firmware, etc. The trick is that DFU has no restrictions on the number of password attempts.
Thus, if you set a goal, you can pick up the code and unlock your smartphone. If you are too lazy to enter numbers manually, you can buy a gadget for auto-search for $500 (already cheaper). But there are also more professional systems, they are much more expensive.
Let's see how the professionals do it. For educational purposes, of course.
“Find iPhone” option
So, the gadget was found. How to unlock your phone? The iPhone 6, like other Apple products, is almost useless in the wrong hands. This is due to the fact that the manufacturer has taken care of various means of protecting its products.
Once a person has found an iPhone, he needs to check whether the “Find iPhone” mode is activated on the smartphone. If such an option exists, you don’t even have to think about unlocking it yourself. Even resetting the settings to factory settings will not help you gain access to the device system.
How to bypass Face ID
When Face ID first arrived on the iPhone X, it was full of holes. Apple claimed that even twins could not bypass the facial recognition system.
But something went wrong. Face ID sometimes mistook children for their parents. And one customer returned her smartphone to the store twice - he persistently confused her with a colleague. In general, the system was inconvenient and unsafe.
Vietnamese company Bkav spent only $150 to create a decoy mask for Face ID. The base was printed on a 3D printer, the nose was made of silicone, the eyes and mouth were printed and glued onto the model.
Face ID mistook the mask for the owner:
This was soon fixed. But in August 2020, they found an even more fun way to unlock it. Tencent researchers have shown how to fool Face ID using regular glasses and duct tape .
When attention detection is enabled on your iPhone, your iPhone regularly checks to see if you're looking at the screen. But if you are wearing glasses, Face ID will not read 3D information in the eye area. The system believes that there are black areas with white dots.
So, if you are sleeping or unconscious, then your smartphone will be easy to unlock. The specialists simply pasted squares of electrical tape with dots-slits in the middle onto the glasses and put them on the “sleeping” colleague. And his iPhone was successfully unlocked.
The hole has already been closed. But the sediment remained.
FAQ
Vyacheslav
For several years he worked in mobile phone stores of two large operators. I understand tariffs well and see all the pitfalls. I love gadgets, especially Android ones.
Ask a Question
Question to the expert
What does activation lock mean?
A function that is activated automatically when the search mode for the missing iPhone is turned on.
What are the consequences of blocking activation for the device owner?
It becomes impossible to use the device
What unlocking methods are there?
Using built-in tools, third-party services, technical support. In some situations, you can even use jailbreak tools.
4.7 / 5 ( 28 votes)
How are fingerprints faked?
The Touch ID system hashes digital fingerprint scans and stores the hashes in a secure Secure Enclave area that is separate from the main storage.
When you try to lock your iPhone with your fingerprint, Touch ID checks the new code against data from Secure Enclave. And the fingerprint decoding is stored in RAM and only immediately after scanning.
Of course, this is much cooler than scanned pictures in certain folders (some Chinese devices were guilty of this). But... the first generation Touch ID could be deceived using a sheet of paper with a fingerprint printed at 2400 dpi. If you have an iPhone 5s, try it, it might work.
Moreover: the fingerprint can be taken directly from the screen. And not only unlock an iPhone with an old scanner, but also prohibit the current owner from erasing data from it.
It's more difficult with newer models. You need a 3D printer and a material that a smartphone will mistake for human skin. And a fairly accurate 3D finger model. And a limited number of attempts.
Biometric identification expert Anil Jain and his colleagues at Michigan State University have developed a technology for producing these “fake fingers” from electrically conductive silicone and pigments. The fakes had the same mechanical, optical and electrical properties as real people's fingers.
Formally, the technology was supposed to improve the reliability of scanners. But it all depends on in whose hands it would end up.
Other researchers, having only a good photo of the finger of German Defense Minister Ursula von der Leyen, made a 3D model of it. They didn’t take the finger separately—the fingerprint was cropped from a high-resolution photograph.
The minister agreed to participate in the experiment. The result is that she herself proved that the method really works.
How to gain access through a single message
Cyber experts Natalie Silvanovich and Samuel Gross from Google Project Zero showed how the CVE-2019-8641 provides access to passwords, messages and e-mail. It also allows you to turn on the camera and microphone on your iPhone.
Project Zero searches for vulnerabilities in the products of Google and its competitors. Experts said that if you know the victim's Apple ID, it is enough to send the victim a message configured in a special way.
iOS has built-in ASLR technology, which makes it more difficult to exploit some vulnerabilities. It changes the location of important data structures in the system address space: for example, the stack, heap, loadable libraries, executable file images.
Silvanovich and Gross found a way to bypass ASLR. Using this and five other vulnerabilities found, experts achieved arbitrary code execution on the iPhone. On the black market, information about these bugs would cost about $10 million.
Good news: the main and most complex vulnerability CVE-2019-8641 was fixed in iOS 12.4.2 in September 2020. The bad news: no one knows how many more similar holes there will be. But the statistics are not encouraging.
Special services to help you remove the blocking
The Activation Lock feature on iPhone allows you to track your lost or stolen phone and lock it from anywhere in the world. At the same time, the function itself has a high degree of protection, which few have been able to bypass.
However, there are special services that specialize in disabling iCloud activation lock for iPhone, iPad, iPod. Below are a number of the most effective programs.
- UkeySoft Unlocker. Allows you to remove Apple ID from any activated device, locked screen passwords, even when the smartphone is disabled, locked or broken.
- iCloudin. The free utility helps you bypass activation lock on Apple devices starting with iPhone 4 and higher.
- iCloudDnsBypass. The completely free program is useful if the user bought a used phone or forgot the ID identifiers. Works on all iPhone models and versions.
- DoulCi iCloud. The application is used to bypass the lock without a password, and allows you to create and run your own iCloud bypass server.
- OpenMyICloud. A well-known unlocking service that has a simple and intuitive interface, wide functionality, but is supported by certain models and versions of iPhone.
- GadgetWide. Identical to the last two applications. Able to easily bypass iCloud activation lock.
How to bypass blocking using voice commands
If you still haven't updated to iOS 12, we have bad news. Siri will “help” unlock your iPhone.
Just call the voice assistant from the lock screen and ask it to activate the VoiceOver . After this, the scammer will be able to call your iPhone, at the time of the call, select a response with a message on its screen and press the “+” key.
The next stage is sending a special message to the victim’s smartphone. When VoiceOver is active, it triggers a system error and gives access to the messaging interface and a list of recently dialed contacts, including their full details.
To protect against this, prevent Siri from being called from the locked screen: this is done in the “Settings” menu - “Touch ID and passcode” - “Access with screen lock”.
Is it possible to unlock a found iPhone?
Apple's security system prevents any attempts to take over someone else's device and the data stored on it.
There may be several unlocking options, depending on the current state of the smartphone.
So, if the user has not configured the “Find iPhone” function, then the gadget will not be in a locked state. But it may also have a lock code that you need to bypass.
First of all, it is worth noting that you should not enter any combinations, since after several unsuccessful attempts, the device will be blocked. It is recommended to use other methods.
You can unlock your device without knowing the password. To do this, you need to completely restore it or reset it to factory settings. The iTunes application, which must be installed on your computer, will help with this.
Factory reset and unlocking
iTunes should only be downloaded from the official website.
To begin, the user should launch the iTunes application on the computer and connect the smartphone using a cable. After this, follow the instructions:
- Go to recovery mode. On iPhone 6S and earlier models, the user must simultaneously hold down the Home and Lock screen buttons. On the seventh version of the smartphone there are lock and volume down buttons. On new models, you need to alternately press the volume up and then volume down buttons, then hold down the lock button. Once the device is rebooted, the screen will display recovery mode.
- A window will appear on the computer screen in which the user will be asked to restore the device. Here you should click on the appropriate button.
- After confirming all actions, the recovery process will begin. The user will need to accept the license agreement.
The recovery process will be displayed on the smartphone screen. It may take a long time. After rebooting, the device will be configured as new. This method not only allows you to remove the set password, but also erases all data stored on the phone. This must be taken into account before starting the process.
Once all data is erased, the user can create a new Apple ID and customize the phone for themselves. Despite the fact that these instructions are quite simple, they can only be used if the device has not been protected in a reliable way.
For more information on how to restore an iPhone via iTunes, watch this video
How smartphones are hacked using ultrasound
Experts from Washington University in St. Louis, the University of Michigan and the Chinese Academy of Sciences have proven that assistants can be activated even with ultrasound.
The scientists used a piezoelectric transducer that transmitted voice commands using ultrasonic waves. The signal was sent through hard surfaces - for example, through a table on which a smartphone was lying.
The human ear cannot hear ultrasound, but a smartphone reacts to such frequencies. A hard case is not a hindrance: on the contrary, the thicker and denser it is, the better it transmits the signal.
Using ultrasound, scientists were able to send SMS, make calls and access basic functions. The method worked not only for the iPhone - Xiaomi, Samsung, and Huawei models were also attacked.
But if you put the smartphone on something soft, the method will not work. And it does not provide full unlocking. In addition, Siri and other assistants can be forced to identify the owner so that they do not react to other people's voices.
Removing Activation Lock
The “Find iPhone” option has been equipped with a new feature since the seventh software – iCloud Activation Lock. It is automatically turned on when setting the first option and significantly complicates life for users who purchased an unlocked smartphone. Each time you activate this option, the smartphone will request your Apple ID and password.
Basically, the problem of removing Activation Lock affects users who purchased a mobile gadget from Apple secondhand. It is known that resetting settings, activating through other programs or resetting settings will not help in this case. And bypassing the blocking is necessary to activate iCloud and start using your device normally.
Of course, you should never save money by buying such an expensive gadget not officially, as you can run into fakes. It can be noted that when buying an iPhone in person, in order not to have to worry about unlocking it, you need to check the full complex of the device.
This is the smartphone itself, a headset, a cable for connecting to a computer, a charger, a box with a sticker (later it will become clear why it is so important), on which you can see the serial number that matches the data on the phone. It wouldn't hurt to ask for a sales receipt.
In order to remove the binding of an iPhone to the Apple ID of the previous owner, if, after all, the phone was purchased unlocked, you need to follow certain recommendations that are associated with contacting support:
- The first step is to write an official letter to contact company employees who will help solve the problem. There is no clear template for this, so you can briefly describe the situation and your request. You must attach a photo of the iPhone and the stickers that were on the box to the letter. You can also attach a sales receipt;
- The smartphone box is really important. There are stickers with numbers and identification data on it. If there is no box, you can scan stickers from identical gadget models and make your own layout by entering the IMEI and serial number. The last one is especially important;
- If you don’t have a receipt, you can also make one yourself. Of course, if you are not afraid of the liability that you may face for falsifying a document. Advice: first it is better to try to write a letter without a receipt, explaining to the employees that they have not saved it. It often happens that users are met halfway - after all, the company values its customers;
- All this is collected in order to prove to Apple employees that the phone is not stolen or misappropriated, but actually purchased. There's just no way to unlock it. All components must be photographed in one photo. Many people advise against using too good quality footage if the receipt and box are not genuine. Employees are unlikely to take a closer look;
- When the photo is taken, you can write a letter to one of the official support service email addresses indicating the serial number. You can find out the request number (which you will then have to indicate in the letter) on the website that deals with troubleshooting, and select your problem there. Then you just need to schedule a call using, again, the serial number. This is also done on the website in a special form;
- After 5-10 days, an Apple employee will respond to the letter. It will indicate that the issue has been assigned a specific number and a company representative will contact the user as soon as possible to resolve the issue. Usually the process takes quite a long time, but it has a good result - the company needs time to check the data.
How to use Cellebrite technology
Motherboard journalists collected materials on 516 orders for obtaining data from iPhones in 2020. In 295 cases, information was retrieved.
The point here is less about technical difficulties, and more about budgets for hacking and the seriousness of the situation. Those who have access to Cellebrite and GrayKey are much closer to success.
Experts from the Israeli company Cellebrite are ready to crack the iPhone password within 24 hours . But only if they directly receive the smartphone itself. What they will do with it and how they will extract the information, experts do not say.
In addition, they sell UFED (Universal Forensic Extraction Device - a universal device for extracting data by court decision) and other similar products, equipment, software, cloud solutions, cyber kiosks.
The technique only works with a direct connection to the manufacturer’s server. Formally, this is necessary to verify the license and control the legality of using the hacking solution.
Cellebrite devices are sold relatively freely. The price tag for the “hard + soft” set starts from 15 thousand dollars . But on eBay and other auctions you can buy an outdated model for ridiculous money - of course, it won’t cope with new iPhones, and the license may be expired.
For information: in 2020, Cellebrite received $1 million for hacking the iPhone 5c of a shooter from San Bernardino. Back then, iOS didn’t even use encryption, and the smartphone didn’t come with a fingerprint scanner.
And no matter how Apple protects devices, soon after the release of new firmware Cellebrite selects master keys for it. This takes from several days to a couple of months.
Data is merged from the smartphone’s memory, SIM cards, and memory cards.
How does Cellebrite find holes in iPhone security? Company employees, like hackers, are constantly hunting for dev-fused versions - working prototypes of smartphones.
In dev-fused, as a rule, there is no OS installed, there is only the Switchboard engineering menu and individual components. Or manufacturers left various loopholes in the software for testing. This makes it easier to reverse engineer and find day 0 vulnerabilities that developers are unaware of.
It is impossible to remove prototypes from Apple laboratories. It's easier to get them from contract assembly plants like Foxconn.
Employees sell components, often without knowing their actual price. They can be understood - at best, assemblers earn a couple of tens of dollars for irregular working hours.
How GrayKey works
GrayKey is developed by Greyshift from Atlanta, USA. It was founded by a former Apple security engineer.
Greyshift supplies its solutions only to law enforcement agencies in the United States and Canada. Without any exceptions.
The device can pick up the unlock code on the iPhone. With its help, for example, the iPhone 11 Pro Max was hacked in January.
The speed of GrayKey is approximately the same as that of Cellebrite. A 4-digit code can be cracked in 11 minutes, a 6-digit code in 11 hours, a 10-digit code in decades (but who uses it?!).
By the way, at the end of 2020 GrayKey went up in price. The price increase was explained by the emergence of new technologies for protecting iOS from hacking and, accordingly, a new revision of the device - GrayKey RevC.
For a license for the online version of the tool they ask for 18 thousand US dollars for 300 hacks per year, previously it cost 15 thousand. And the offline version still costs 30 thousand dollars , there are no restrictions on the period of use.
How does MagiCube, which was purchased by the Investigative Committee, work?
Two years ago, the BBC wrote about mysterious MagiCube gadgets from China. Experts said: if GrayKey and Cellebrite take a day to hack an iPhone, then Chinese magic will do it in just 9 minutes .
The iDC-8811 Forensic MagiCube “suitcases” were developed by Xiamen Meiya Pico Information in July 2020. It was also reported that MagiCube is “tailored” to receiving data from instant messengers. They say that the most valuable information is there.
For the analysis, we purchased additional software - the iDC-4501 system for analyzing data from mobile devices and IFM-2008 Forensics Master for data from a PC.
5 million rubles on hacking tools . These are two government purchases: for 2 million rubles - for the Military Investigation Department of the RF IC for the Central Federal District, for another 3 million - for the Military Investigative Department for the Eastern Federal District.
Xiamen Meiya Pico Information is not just another no-name. The company is truly one of the leaders in the electronics forensics device segment in China, with more than 20 years in the local market and about 10 years in the international market.
But there are inconsistencies. Firstly, the iDC-8811 Forensic MagiCube is simply a hard drive duplicator that runs Windows 7 . It can copy data and examine it. And only if the media is physically connected to the “cube”. The solution will not be able to get into your smartphone remotely.
At the time of purchase (July 2018), iDC-4501 could only work with iPhones running iOS 10.0–11.1.2. That is, without the latest updates (iOS 11.1.2 was released in November 2017).
And most importantly: this system does not pick up the iPhone password. This means that it will still have to be obtained using the GrayKey or Cellebrite tools.
Actually, I also had to buy UFED 4PC Ultimate from Cellebrite. It includes everything you need, including UFED Physical Analyzer for deep decoding of information from mobile devices.
If all else fails
When none of the methods discussed above helped, you can use special programs to unlock your iPhone. But, you should approach these methods with caution, carefully check the resources, and understand that most of them can further harm the mobile device.
The most popular iPhone unlocking utility is 4uKey. The program helps if the phone owner has forgotten the password. More details in the video:
If you bought a new iPhone and have all the supporting documents, it is better to contact an authorized Apple center or write an email directly to the manufacturer.
3 / 5 ( 3 voices)