Download and install Comodo Firewall
Installing Comodo Firewall is not fraught with any particular difficulties, but there are still some nuances that are worth considering. We will talk about them in the first part of this article.
You can download this miracle of programming thought from the developer’s website using this link by clicking on the appropriate button:
After downloading, run the previously downloaded file to begin the installation process, which, however, will begin with unpacking the files necessary for the installer:
After this, Comodo Firewall will prompt you to select the installation language. Choose the one that is closest to you (in our case Russian):
Next, you will need to uncheck the boxes “I want to use cloud analysis of application behavior by transferring unidentified programs to COMODO”, as well as “Anonymously send application usage data to COMODO to make changes that improve the operation of the program”, because there is no need for them, as and in email subscriptions.
However, if you think that you need them, then you can leave them. Next, it would be useful to click on the “Customize installation” button, rather than immediately clicking on the “Forward” button. This very button will allow us to configure the elements for installing (more precisely, the components) of the Firewall:
Each element has its own description by which you can make a choice yourself, but we recommend unchecking “Install COMODO GeekBuddy”, which allows you to receive some remote support and other tails and install only the part with the firewall.
Comodo Firewall - what kind of beast is it?
05/23/2016 First, let’s figure out why the Comodo Firewall is needed at all and what kind of beast it is?
Firewalls monitor your system's communications between your computer and the Internet to detect and prevent outside attacks. Finding a suitable Firewall that meets all the needs of a modern user is not an easy task. A good firewall should: protect the user by providing a close to ideal level of system security, be invisible in operation, have a simple set of settings and an intuitive interface.
Firewalls come in two forms - as software and as hardware. A hardware firewall is a special component of a computer system to ensure the security of the entire network. Software-based firewalls are installed on a computer and ensure the security of a specific system, including from intrusion within the local network - this type of firewall is installed on 90% of systems around the world. To avoid potential conflicts, it is recommended to keep only one firewall of each type installed. The combination of a hardware firewall and a software firewall provides the best security results, but the price is not affordable for many.
Simple firewalls (for example, the default Windows Firewall) limit access to your system and personal information, but they are no longer able to counter threats that deliberately harm your computer. Some types of malware are best detected by their behavior, so an active firewall (firewall or / combo HIPS) provides reliable protection along with your antivirus program. However, it is important to use proactive protection for active protection and safe practices in order to minimize the risk of malware on your computer.
Comodo Firewall is a full-featured security suite , making it an excellent choice for users looking for a free product with a high level of security. Comodo Firewall is suitable for both experienced users and users who are faced with installing a firewall protection. HIPS or application monitoring feature, also called "Defense+" provides a varying number of controls and settings. Comodo Firewall includes a "memory firewall" that protects against buffer overflow attacks, as well as a lightweight "sandbox" component that monitors unknown applications, new software installations and their impact on your computer. Comodo Firewall constantly checks a list of known safe applications and if an unknown application attempts to take advantage of the user's trust by running malicious code, Comodo Firewall will notify the user and stop the application.
During installation, Comodo Firewall offers three installation options to choose from: firewall only, firewall with optimal or maximum proactive protection. After installation, Comodo Firewall automatically selects “Safe Mode” to work with the user to create the most rational security policy: from loyal to paranoid.
Installation configuration
Next, regarding the tab with configuration options:
If you are not very knowledgeable about working with firewalls, then this checkbox may be worth leaving. This will allow you to avoid unnecessary configuration and notifications, but at the same time Comodo Firewall will make some decisions for you based on statistics (for example, allowing connections for known normal applications, such as browsers, and blocking known malicious or suspicious ones).
Well, the last tab allows you to select the location of the firewall installation files. You can, traditionally, leave the default, or specify your own. Next, click on the “Back” button and return to the previous step, where we unchecked the first checkboxes and clicked on the “Configure installation” button, where, in turn, we click “Forward”.
Next, we will continue to struggle with the checkboxes, because we will be asked to install Yandex elements, make Yandex the main one, and generally everything else. Traditionally, we uncheck all the boxes, unless of course you don’t need Yandex, and press the “I Agree” button. Install".
After this, the process of obtaining a free license and installing COMODO Firewall will begin.
In fact, all you have to do is wait for the end of the process, after which the firewall will start up and start screaming urgently and demanding attention, rebooting and other things, and doing this in several windows at once:
Well, you’ll have to make concessions and allow a reboot (after closing everything you need and saving the work process), otherwise the firewall won’t work normally, and, in general, it won’t let you.
After the reboot, we will begin using and further configuration.
Which firewall is the best?
The question is very, very controversial. As they say: how many people have so many opinions. And I have my own opinion on this matter. For more than ten years of my active activity on the Internet, I have tried and tested almost all firewall-type programs and made an unexpected conclusion: they are all almost equally “leaky.” And this does not depend on whether the firewall is paid or free).
Based on the above, I will not recommend paid versions of the firewall. Why pay money for an obviously “leaky” product. Therefore, I will focus on free options. And the best one in my opinion is:
Windows firewall
I can already see your surprised face: “Where is the promised Comodo Firewall? Wait! Let's go in order.
Windows Firewall is truly one of the best firewalls out there. And these are not just my fantasies. This information is confirmed by the results of numerous and long-term tests of programs such as Firewall. According to the results, the Windows Firewall has consistently occupied and continues to occupy a leading position.
The main advantage of the Windows Firewall is that it is already installed in the Windows OS by default. Absolutely free, always updated on time and reliably protects the PC system from unauthorized access from the external Internet. But…
This is provided that you have licensed Windows. In the absence of a license, the Windows Firewall turns into an absolutely useless and even dangerous product that, due to the lack of updates, will almost instantly kill your computer system.
Now think about how many people in the vast expanses of our country use licensed Windows? That's it.
Therefore, first place is rightfully awarded to the absolutely free firewall from the Comodo antivirus.
Installing and configuring Comodo Firewall
In order to download Comodo firewall from the official website, go to.
Next, watch this video:
If there is something in this video that is not clear to you, then below I give similar instructions in pictures.
- Download the Comodo Firewall installation file in Russian from the official website. Attention! This is the link that is mentioned in this article and described in the video above. That is, there you can download Comodo Firewall for free, but complete with an antivirus. But after the publication of this article and video on YouTube, I still found a page where you can download Comodo Firewall from the official website without an antivirus.
2. Run the Comodo Firewall installation file.
3. Go to the “Options” section.
4. Uncheck: “Import Google settings...” and go to the “Components” section.
5. Uncheck all the boxes except “Comodo Firewall”.
6. The firewall installation process begins.
7. Uncheck all the boxes.
8. The Comodo antivirus update has started automatically. Turn it off without waiting for the computer scan to finish.
9. In the “Antivirus” section, set the “Disabled” option.
10. In the pop-up window that appears, select the “Permanent” option and click “OK”.
11. That's all Comodo Firewall Settings.
Initial launch and setup
After installation, most likely, you will immediately see a small (side) window of the program, a notification about how Comodo protects you, and the developer’s website that will automatically open. If everything went well, then everything will look something like this:
You can check the box “Do not show this window again” right away, since there is no need for it, other than self-education:
Also, most likely, you will immediately receive a notification about the network you are on with a set of items, the choice of one of which will determine a certain level of security and internal settings:
The choice should be made wisely, or more precisely, to be honest about where you are. Or, if you have some concerns and are concerned about the level of confidentiality, then choose the third point, i.e. “I am in a public place,” as the most powerful in terms of protection.
Installing Comodo Firewall
Over time, program producers change the interface of their creations, improve them in every possible way, add new functions and remove unused ones... They have the right to do this. In any case, their logic, purpose and spirit always remain the same - based on this review, you can understand any form of software.
I recommend
Here they are - unnecessary additions. Uncheck them and move on...
I have already described to you how to find the fastest DNS servers, and so - COMODO DNS servers are not only slow, but also completely scared.
If you leave the top checkbox you will get yourself a headache - half of the sites will be blocked. I recommend leaving the second checkbox.
Be sure to go to the “Customize installation” item...
I unchecked the bottom checkbox - I don’t need advertising, even verified ones...
Here it is, our dear one - what would it be without Yandex!!!
Of course, we remove all the boxes...
We look around and find out where we are. If you don’t have your own home local network, I recommend clicking “I’m in a public... place.”
Congratulations! You have installed Comodo Firewall - the best free firewall for Windows.
Let's tweak it a little now...
Handling Comodo Firewall requests
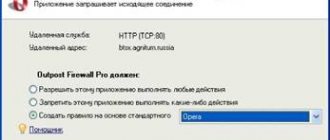
The second type of notifications will be about attempts by various types of programs to connect with something or someone, as well as about doing something for some reason. It looks something like this:
The logic for processing such requests is simple: if you know what kind of program (for example, a browser) is trying to connect to something or perform something, then you allow the action to be performed, but if you are not at all aware of what kind of nonsense is happening (even after how they used an Internet search, etc.), that is, it makes sense to block or process according to one of the application rules.
Next, it makes sense to go to the main program window. This can be done using a small window (right mouse button - “Open”) or a tray icon (the latter can change to display traffic or the firewall logo):
The main window of the program looks quite clear, moderately concise, and, in fact, contains most of the necessary information. It may be that it makes sense to start with the update process, although if you installed the program from the developer’s website, then the version should be the latest initially:
The buttons are all standard and each is responsible for the corresponding functionality. For example, the “Scan” button will actually allow you to scan your computer for threats and will provide a detailed list-report about what kind of files live in the system and whether they should be trusted:
We have already talked about updates, so we won’t take an extra screenshot, since the update is responsible for the update and there is nothing complicated in it.
Setting up Comodo Firewall
In fact, there are many configurations of this firewall settings - the Internet is littered with them (). You can configure the defender in such a way that you won’t be able to breathe between its notifications, warnings and questions.
Or you can convince him to work quietly and unobtrusively - it’s up to you, I’ll give just a few tips below...
Go to the program settings...
...and check ALL the boxes in the advanced settings (as many people advise online), but if you have problems connecting to the Internet, uncheck the bottom two.
Here you can disable the display of the widget on the desktop if you don’t need it...
I left it, although I categorically do not like all sorts of widgets on the desktop. I edited it slightly by RIGHT-clicking on the firewall icon in the tray...
But here is the most terrible firewall setting, which will turn it into a real reinforced concrete wall...
Instead of safe mode, you can install...
In this mode, get ready for a million questions from the defense attorney on any occasion. But now your Comodo Firewall will pass the reliability test - 100%.
Firewall questions look like this...
You can check the box at the bottom of this window (remember...) and simply allow execution. This is if you know a program that is trying to access the network. You can also “Process as”...
This way we will get rid of repeated questions, for example, about the Nexus program contacting Clover.
After setting up the Comodo Firewall, I strongly recommend scanning your computer - this way you will greatly reduce the number of questions the defender asks you...
That's all I wanted to tell you about Comodo Firewall. If you have any questions, here you go.
Oh yes, regarding the unnecessaryness of such precautions (the opinion of some readers) - there is always a first time...
- when some new virus, not yet recognized by antiviruses, passes through your quiet and calm firewall and kills the system
- when your account on a social network is hacked in an “incomprehensible” way
- when your computer “itself” starts sending spam to half of the Internet...
...remember that Comodo Firewall is the best free firewall for Windows. Until new strong programs.
Isolated environment and more details
A button with a virtual desktop will allow you to launch an isolated environment in which you can walk through dangerous places.
In terms of logic and principle of operation, it resembles a kind of VirtualBox based on Windows functionality, and is also extremely similar to a sandbox (like Sandboxie) in its expanded, moderately adult form. An extremely useful thing, we recommend it for paranoid people.
You can switch between desktops using the appropriate button, quickly and fairly painlessly, which is convenient. By the way, installing all of the above (Silverlight and Comodo Dragon) is not a necessary functionality for full operation, but recommended as such.
The quarantine tab is responsible for quarantine, online support for online support. In general, there is nothing unusual and we will not dwell on them. The button in the upper left corner allows you to see a detailed summary of what is happening:
That is, see the number of incoming and outgoing connections, blocking processes, enable or disable all sorts of Auto-Sandbox, HIPS and Viruscope, and manage what is already blocked, isolated, etc.
Clicking on the corresponding, so to speak, link will allow you to see the information in more detail or open the settings. Here, for example, is what information about connections in the system looks like (reminiscent of TCPView, etc.):
Clicking on a firewall link, for example, will allow us to open a tab with settings and the corresponding subtab, but here we can manage all the settings in general by going to where we need it (for example, “General Settings” - “Interface”). Let's take a quick look at them.
Advanced setup and use
The interface tab is, oddly enough, responsible for the interface. If you wish, you can customize the theme, again, language and other tails. It is recommended to disable the long-suffering sound, greetings, various types of notifications and other annoying functionality here:
The updates tab is responsible for the frequency of updates, and the log for, logically, the size of the log, its re-creation, and so on. It’s all logical, simple and easy to set up, fortunately it’s in Russian, I think you’ll figure it out.
On the configuration tab, you can enable or disable any of the ready-made configurations. This is very, very convenient, and when switching, it allows you to save the existing and changed configuration, i.e. you can change the security level, depending on the circumstances. True, switching requires a reboot, which, in general, is logical.
Next are the key settings, namely, security settings, i.e. “Protection+”, “Firewall” and “File Rating”.
Comodo Firewall
- Official website: comodo.com
- System requirements: Windows XP SP2, Vista, 7, 8, 10, 152 MB RAM, 400 MB disk space
- License: there is a free version and Pro
- Cost: Free or $39.99 for Pro
- Interface language: Russian
This program became widely known back in the era of Windows XP, when Comodo Firewall was perhaps the most widespread free firewall in Russia. It is still popular today. Which, in general, is not surprising: the developers promise us proactive protection with HIPS, firewalling, protection against buffer overflows and unauthorized access, protection of the registry and system files, as well as other tasty goodies.
However, during installation the firewall caused mixed feelings. At first he suggested installing extensions for Yandex Browser.
Shall we install extensions from Yandex?
And then, if you don’t pay attention to the “components” and don’t turn off everything unnecessary, the installer will install his browser on your computer.
Disabling unnecessary components
Forgot to disable an unnecessary component? Receive, sign
We do the first test, and Comodo skips our tool.
First test of Comodo Firewall
We turned on training mode in the settings - and for some reason the firewall did not react in any way to our test program, which successfully connected to the remote computer.
Second Comodo Firewall test
Only after compiling a white list was the tool finally able to be blocked. The conclusion is contradictory: Comodo Firewall is a very well-known firewall, but installing unnecessary software spoils the whole impression. And the test results turned out to be sad: to ensure security, the program requires thorough configuration.
Hips and sandbox in Comodo Firewall
The protection includes the above-mentioned HIPS (a proactive intrusion prevention system), Sandbox (a sandbox that is responsible for virtualization and protection based on it) and VirusScope (a system that allows dynamic analysis of running processes and recording their activity).
For HIPS, it would be nice to include detailed explanations (if you don’t understand), configure the display time of alerts and, optimally, check the box “Adapt operating mode when system resources are low” so that it does not eat up performance so much. In principle, it would be possible to turn on the enhanced protection mode, but it is very paranoid and voracious.
In the Sandbox settings, you can uncheck the first box if you do not need it, and it would also be a good idea to protect your desktop with a password. But what is much more important here is the presence of an automatic Sandbox based on a given policy:
This increases security by an order of magnitude, provided that you understand how Sandbox works in general, and also realize that it chews resources. If not, then it is recommended to read at least this article.
In Viruscope, it makes sense to disable the display of alerts, provided that you trust the automation. In general, the logic of its operation is quite adequate, but it requires periodic monitoring and verification of what is happening if something stops working for you.
On the firewall tab, it would be a good idea to reduce the frequency of alerts, enable IPv6 traffic filtering, protection against ARP spoofing, and create rules for secure applications.
On the sub-tabs, you can set and adjust rules for applications, as well as edit those that you have already created by clicking on the block/allow buttons for the corresponding firewall requests above.
Here you can create sets of rules and even activate a content filter by blocking and or allowing certain sites and categories (created independently). With the right approach, you can create your own kind of parental control.
Well, on the file rating tab (this is the same scan that we launched at the very beginning), it makes sense to enable cloud analysis of unknown files (be careful, traffic!), in order to save system resources.
With this you can finish the setup. As for use, it makes sense to start with the training mode (turned on next to the firewall line in the extended view of the main program window), then switching to the custom set or, if you are too lazy to configure and train, then safe mode.
In a nutshell, perhaps it’s something like this. We will not describe more fine-tuning and use here, because part of any article would not be enough, besides, part of the logic has already been described in the relevant materials on other firewalls (see the beginning of the article), books from the author and training.
So, actually, let's move on to the afterword.
Installing and configuring Comodo Firewall
12/23/2009 2502 Share
Cool
Share
Tweet
Let's start getting acquainted with Comodo Firewall by installing it.
When you run the installation file, a warning window appears warning you about the need to remove other programs of a similar purpose in order to avoid conflict situations
If you already have any firewall installed, remove it; if not, then feel free to continue. Now click on the “YES” button in the warning window. Further installation is standard for most Windows programs. You just need to click “Next”. At the end, the program will offer configuration options: automatic or custom
Leave it on automatic. To complete the installation, all you have to do is restart your computer.
After the reboot, you will immediately be asked questions about the activity of programs that can use the network.
Here you need to understand which program you allow or prohibit activity. When you click the “Allow” or “Deny” button, the firewall will allow or not allow the program to access the Internet once. If the program tries to access the Internet again, the window about its activity will be displayed again. If you are confident in the program that is trying to access the Internet, you can check the “Remember my answer for this application” checkbox and click “Allow”. Comodo Firewall will now understand that you trust this application and allow it to run without interference. In the same way, a ban is set for the program: check the box “Remember my answer for this application” and click “Ban”. Comodo will always block this program.
During testing, the first questions were asked regarding alg.exe and svchost.exe.
These are system programs and must be allowed access. Questions about user programs will be asked as they are launched. If the program is intended to work on the Internet or via the Internet, then it must be allowed. If it is clear that the program is overly zealous in caring about the user and wants to download something from the Internet or transmit it via the Internet, then its access should be denied. Thus, you, interested in your safe stay on the global network, after some time will create rules of conduct for all programs installed on the computer.
Having made an erroneous ban or allowed the program to be active, you can always use the Comodo Firewall settings and correct the situation. Looking at the lower right corner of the screen, where the clock is located, you will see an icon with a shield. This is Comodo. Right-click on the icon and select Open. The main program window will open immediately
The main window clearly shows the basic parameters of the firewall. At the top of the window you can choose between the “Summary”, “Protection”, “Activity” panels.
On the left are icons for switching between the windows of this panel:
Tasks - In this window, you can quickly allow or deny program access to the network, as well as select other options, the capabilities of which are well described under the name of each option. It is better not to touch anything unless necessary.
Application Monitor - designed to view and edit the list of applications that the user trusts. The window is presented in the form of a table, which indicates:
- program name (Application),
- IP address to which the connection is made (Recipient),
- port number on which communication takes place (Port),
- protocol within which information is received and transmitted (Protocol),
- Well, and the column (Permission), which shows whether access to the application is allowed or denied.
Pay attention to the quick action options:
- Enable/disable – you can temporarily disable some of the rules, for example, for testing purposes.
- Add – A fully customizable option to create a new rule.
- Edit – Edit the rule on which the cursor is positioned.
- Delete – permanently removes the rule from the list.
By double-clicking the left mouse button on the program name or clicking “Edit”, you will be taken to the window for fine-tuning (editing) the rule
This window indicates the full path to the program on disk, the path to the program that is the parent of the one being configured. Nothing needs to be changed here.
And by looking at the tabs below you can: - assign a program action to the application activity, specify the protocol and direction of the program activity (whether the program receives information (Incoming), sends (Outgoing) or both receives and sends), - specify one or more IP addresses with with which the application interacts. One or more ports that an application opens when communicating.
Component Monitor - designed to monitor the integrity of important files - sometimes viruses try to change files and Comodo can prevent this.
Network Monitor – Attention! The order of the rules is important here! Comodo Firewall scans rules from top to bottom. This tab allows you to fine-tune the firewall filtering parameters for data transmission by IP addresses and ports. Here you can forcefully close potentially dangerous ports. Here's how to do it: Click the "Add" button and in the window that appears
select the “block” action and specify “one port” on the “Source Port” tab, and also enter the port number, for example, 137. Click the “OK” button. The new rule will appear in the list. Use the “Up” or “Down” arrows to specify the location of the rule in the list. To avoid mistakes, for now you can simply place the rule in the middle.
On the “Advanced” of the “Protection” window, you can further configure the firewall. These features need to be mastered gradually; as you work with the program, you will understand when there is a need for additional settings.
By going to the “Activity” , we will see two tabs: “Connections” and “Log.” “Connections” displays a list of programs that are currently active. Here you can see if there is anything suspicious among the programs you trust. As well as the amount of data transmitted/received.
The Journal contains a chronological record of important events. You can always refer to it when analyzing the actions of one of the programs.
And of course, don’t forget to update the program components. By clicking the “Update” button at the very top, you will launch the wizard for downloading new components. This simple procedure will prevent new emerging malware from carrying out destructive actions on your computer. By default, the settings are set to automatically check for updates.
Easy to use and configure, the Comodo firewall program will protect your Internet browsing and help you learn to understand the processes that occur during the exchange of information over the network.
Share
Cool
Share
Tweet
Afterword
So this heroic epic about the brave struggle of a valiant firewall against an overwhelming army of computer pests has come to an end. With your skillful control, this struggle will always end in victory for the forces of good 
With this I say goodbye to you. Let viruses and other malware bypass you! As always, if you have any questions, additions, thanks, etc., then welcome to comment on this article.
This is especially true for add-ons, because surely those who have been using Comodo Firewall closely and for a long time, in fact, have something smart and to the point to say.