Review of Outpost Security Suite - a comprehensive solution for protecting your computer
What is the essence of protection that any computer should have? Figuratively speaking, it should be similar to the security service in a closed club. One employee works as a doorman, knows regular customers and only lets them in and out. And when new people appear before entering or exiting, he quickly informs the senior manager and acts on the instructions of this manager. At the same time, for this doorman there should be no “thieves” or relatives, and passes and releases due to a bribe should be unacceptable for him. Another employee must monitor the internal order in a closed club, so that, God forbid, some dirty trick that has started in the premises does not persuade respectable and ignorant trusted members to take something out of the club in their pockets, and especially not damage the furniture in the club herself. The analogy may not be entirely complete, but this is how Internet Security class products should work, one of the representatives of which has recently become the well-known Outpost from the Agnitum company. It has added antivirus and antispam and has now become Outpost Security Suite.
New modules
One of the innovations in the Security Suite is the built-in anti-spam module Agnitum Spam Terrier - the company’s own development. This module is a complete analogue of the free Spam Terrier, which we have already talked about.
Another innovation is the appearance of an antivirus. It cannot be said that before the advent of the antivirus in the Security Suite, the popular Outpost was completely helpless in the face of any infection. It had built-in anti-spyware protection as a separate module. But this protection provided protection only against one, narrow class of malware and was not fully anti-virus protection. The choice of an anti-virus partner, the Hungarian company VirusBuster, was determined by the need to combine anti-virus and anti-spyware protection without conflict. This antivirus engine is not as famous as Kaspersky Anti-Virus or Panda, but this does not mean that it is worse. Over the fifteen years of its existence, VirusBuster has successfully passed all tests and received such certificates as Virus Bulletin 100%, ICSA Desktop/Server Anti-Virus, West Coast Labs and Checkmark Anti-Virus Level Two.
But, despite the emergence of anti-virus protection, the main thing in the work of Outpost Security Suite remains proactive protection, which consists of two areas:
- actual protection against threats to your computer;
- Outpost internal protection against shutdown.
External threats
Potentially dangerous actions are those actions of programs that can create conditions for bypassing firewall protection. Among the threats that can help your computer either become a bot or transfer confidential information to a third party are the following:
- gaining control of other, legitimate applications by malicious code;
- launching a browser with command line parameters;
- use of the address space of legitimate applications by other processes to execute third-party code;
- use of Active Desktop, which may contain code that can transmit sensitive data on behalf of Windows Explorer;
- simulating user keystrokes in other windows and performing unauthorized data exchange between these windows;
- attempts to change critical registry values;
- unauthorized DNS queries;
- low-level network access.
The program interface has not changed
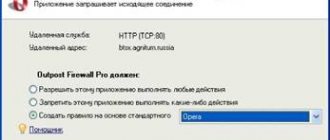
As you can see, ill-wishers have enough methods to gain unauthorized access, and protecting a personal computer from intrusions requires not only the availability of appropriate software, but also the desire and ability to work with it. In terms of protecting a computer for a non-network security specialist, Outpost Security Suite is very convenient. If the now popular free Comodo is too complicated for such a user, then Outpost quite reliably protects the computer even if used incompetently. (If, of course, you respond to notification windows that appear, and not sit in the “Allow” mode.)
To users who are inexperienced in security matters, which are the vast majority of ordinary Internet users, organizing protection against the listed threats may seem quite complicated. But that's not true. Organization of proactive protection on a personal computer is facilitated by three tools: a detailed user manual, the presence of a hint mechanism built into Outpost, and the principles of the firewall itself.
The hint can be received directly from the Agnitum server
The User's Guide can be considered as a beginner's guide to network security in general. If you want to be protected, then you cannot do without reading it. The built-in support mechanism is, in addition to the help file, a small “Helper” button available in each pop-up window of the program. Thanks to it, the user can receive information on how to react to the situation that has arisen.
The program's own principles of proactive protection are designed in such a way that, by monitoring network activity, the firewall identifies potentially dangerous actions and, like the doorman, either prohibits them or informs the owner about these actions to make a decision.
Enable blocking mode after setting up the program
Thus, by paying a little attention to the program during the initial setup, you can subsequently use proactive protection to monitor all unauthorized network activity on your computer. It should be noted that vulnerabilities that allow unauthorized access, although discovered much less frequently than new viruses appear, still surface. Therefore, you should not neglect updating the firewall mechanism itself.
Internal protection
Provided the user is attentive to the program signals, it is technically quite difficult to break through the protection. Therefore, methods may be used to disable the firewall itself. This is why the program needs internal protection to avoid this threat. The mechanism of this protection is similar to the external protection mechanism: all actions that lead to changes in files and libraries that the firewall works with are monitored, and a message is displayed to the user.
Conflict with eTrust antivirus
One of the features of internal protection is the potential for a conflict between third-party antivirus programs and this very protection system. You can avoid this conflict by including the antivirus engine you use as one of the trusted programs that can modify files and libraries. But when using the Outpost Security Suite anti-virus module, you will not have any such problems, because the anti-virus mechanism was selected taking into account all possible conflicts. But we must remember that two antiviruses cannot simultaneously work in real-time monitor mode. And one of them - your own or built into Outpost Security Suite - you will have to disable.
Summary
Means of attack on someone else’s computer are always one step ahead of the means of defense - this is a reality of life. Any security can be hacked, the question is the cost of this hacking. When the cost of hacking exceeds the benefit received, the attack ceases to be economically effective. Modern security measures have reached such a level that at this stage, to gain unauthorized access, it is more profitable for ill-wishers to use social engineering tools (phishing, pharming) than a direct attack on a computer. The experience of support services suggests that in the vast majority of cases, the user gets an infection and other problems only due to his own stupidity and carelessness. That is, technically ensuring the appropriate level of security with the same Outpost Security Suite is not at all difficult, you just need to be attentive to your guards - the firewall and antivirus and not be lazy to familiarize yourself with the basics of network security.
View the cost and terms of purchase
Functionality
To ensure security, Outpost Security Suite Pro 7.5 uses the following main modules and additional tools:
1. The Antivirus + Antispyware module provides protection against viruses and other malware. This module includes several components:
- antivirus monitor. Performs file and system scans in real time;
- antivirus scanner. Performs on-demand file and system scans;
- mail antivirus. Checks email and news feeds;
- web antivirus. Checks web pages for viruses and malicious scripts;
- USB device protection. Allows you to configure different modes for blocking startup of various external devices when they are connected;
- advanced heuristic analyzer. Checks whether software modules may be malicious;
- Rootkit protection allows you to detect hidden programs that may be installed on the system.
2. A two-way firewall protects network connections by controlling connections to and from your computer and preventing unauthorized local and remote access attempts. The firewall's intrusion detector detects local and external attacks, and IP blocking prevents access to websites that the user has designated as "unwanted." One of the new firewall features is traffic filtering for mobile broadband devices (for example, 3G modems). The firewall can also prevent attacks on TCP and UDP ports, ICMP attacks, ICMP flood and ARP flood, IP address and MAC address spoofing, etc. A detailed description of the types of attacks that Outpost Security Suite Pro 7.5 protects against can be found here.
3. Proactive protection allows you to proactively block unknown threats. Proactive defense includes several components:
- “Leak protection” (Anti-Leak). Prevents interception of user input from the keyboard, protects data on the clipboard and protects against attempts to programmatically take screenshots;
- "Application protection" Protects user data (passwords, browsing history, bookmarks, cookies, etc.) that he uses when surfing the Internet from access by malicious programs;
- "system protection" Ensures the integrity of system files and system settings;
- "protect files and folders." Prevents unauthorized access by third parties and malicious programs to protected files and folders on the computer;
- self-defense. Ensures the integrity of all components and prevents unauthorized shutdown of Outpost Security Suite Pro 7.5.
4. Web control. Designed to ensure safe operation on the Internet. Web control consists of the following components:
- "black list" of sites. Prevents visiting dangerous websites;
- ad blocking. Allows you to work with web pages without advertising banners and pop-up advertising windows;
- blocking active content. Allows you to limit the launch of potentially dangerous interactive elements (scripts, media content, flash, gif animation, ActiveX objects) on web pages, as well as in emails written using HTML markup;
- blocking by keywords. Allows you not to display web pages with specified words;
- protection of personal data. Blocks external transfer of personal data.
It should be noted that the databases of dangerous sites and advertising sources are constantly updated automatically.
5. Antispam. Automatically detects and filters unwanted emails.
6. Event log. Allows you to view all events recorded by Outpost Security Suite Pro 7.5.
7. SmartDecision technology for signature-free detection of potentially malicious programs with a multi-level risk measurement system. Analyzes executable files according to a number of criteria in order to determine their potential danger. As a result of the analysis, the user is provided with a visual hint for further actions with the window color corresponding to the situation - red, yellow or green.
8. SmartScan technology. Allows you to reduce the time of re-checking by saving statistics from previous checks and excluding previously verified and unchanged files.
Table 1. Comparison of features of various Outpost PRO products version 7.5
| Possibilities | Outpost Antivirus Pro | Outpost Firewall Pro | Outpost Security Suite Pro |
| Antivirus | + | + | |
| Anti-spy | + | + | + |
| Proactive Defense | + | + | + |
| Self-defense | + | + | + |
| Protecting removable devices | + | + | + |
| SmartDecision Technology | + | + | + |
| Firewall | + | + | |
| Web control | + | + | |
| Attack detector | + | + | |
| Blocking sites | + | + | |
| Application and system activity monitoring tools | + | + | |
| Antispam | + |
Agnitum company focuses on four types of problems solved by Outpost Security Suite Pro 7.5.
Figure 1. Tasks solved by Outpost Security Suite Pro 7.5
Working with Outpost Security Suite Pro 7.5
To launch Outpost Security Suite Pro 7.5, you need to click on the “Outpost Security Suite Pro” shortcut located on the “Desktop” or on the program icon in the tray.
The main program window consists of four zones:
- toolbar (top of the window). This panel is located at the top of the window. It contains buttons for running a system check, calling up program settings, updating the program and calling help;
- control panel (left side of the window). Using this panel we can navigate between the tools of Outpost Security Suite Pro 7.5;
- information panel (left side of the window). This panel contains controls and information about the operation of the tool selected in the control panel;
- status bar (bottom of the window). Displays the current security of the computer.
Please note that the description of functionality will be carried out in the advanced mode of the program.
When downloading Outpost Security Suite Pro 7.5, we find ourselves in the first tab “My Security”, which contains information about the operation of the main tools, the date of signature updates, and the license expiration date. Also in this window we can read news from Agnitum and go to the support page.
Figure 12. Main window of Outpost Security Suite Pro 7.5
A special feature of Outpost Security Suite Pro 7.5 is that the main window is mainly used to view information about protection tools and the results of their work. All functionality (all the “brains”) is concentrated in the settings of Outpost Security Suite Pro 7.5.
Introduction
The task of protecting home computers from malware and network attacks is becoming more acute every year. New types of threats, new objects to protect and, accordingly, new protection technologies are emerging.
Agnitum products have accumulated their own audience, which has trusted them for many years. The product itself is also evolving – both its interface and the technologies implemented within this comprehensive security solution. Recently, the Agnitum company bought the VirusBuster anti-virus kernel, which now bears the company’s name, and is itself engaged in the further development of the technologies implemented in it.
The complexity of the Outpost Security Suite approach can be assessed by the number and functional content of the modules:
- antivirus module;
- two-way firewall (a traditional strength of Agnitum products);
- proactive defense;
- SmartDecision technology (helping the user make decisions related to computer protection);
- web control with content filter;
- mail traffic protection;
- protecting the system and applications from changes;
- a self-defense module that prevents malicious programs from modifying or removing software modules of the complex;
- SmartScan scanning optimization technology;
- USB device startup protection;
- monitoring applications to track file activity and access to the registry;
- game mode for active gamers.
Conventionally, Outpost Security Suite protection can be divided into four levels:
- contact prevention;
- prevention of infection;
- resident protection;
- preventing data leakage.
Looking at Figure 1, you can clearly see the distribution of the numerous protection components available by their levels.
Figure 1. Outpost Security Suite protection levels
The automatic learning mode implemented in Outpost Security Suite will make it easier for novice users to work with the product.
Experienced users have the opportunity to fine-tune many different protection parameters using an extensive settings interface.
You can view the results of Outpost Security Suite operation, as well as events occurring in the system, using the reporting module - it is possible to view reports both in the corresponding section of the graphical interface, and in more detail in the corresponding text log files.
Outpost brand products have repeatedly received certificates from various well-known testing laboratories, such as VirusBulletin, Matousec, Anti-Malware.ru.
Products manufactured under the Outpost brand quickly support new versions of operating systems. In particular, already in the previous version 7.6, a new OS was supported - Windows 8, in 32-bit and 64-bit versions.
Note. For this review, Outpost Security Suite 8.0 was installed and tested on a 64-bit edition of Windows 8.
We list other advantages of the 8th version of Outpost Security Suite.
Content
- Installing Outpost Security Suite 9
- Free version
- Appearance
- PC Scan tab
- Settings tab
- Tools Tab
- Network activity
- Access to files and registry
- Event Viewer
- Settings
- General tab
- What is SmartScan?
- How to set Oupost with a password?
- How to disable automatic updates?
- What is ImproveNet?
- Application Rules tab
- How to create a rule in Outpost? (manually)
- Firewall tab
- How to disable PROTO41 persistent windows? (IPv6)
- How to block an IP address?
- Antivirus+Antispyware tab
- How to disable flash drive scanning?
- Proactive Defense tab
- How to lock a folder? (or file)
- How to completely block flash drives?
- Web Control tab
- How to block flash, scripts, Java?
- How to block ads using Outpost?
- How to block websites using Outpost?
As the developers of the antivirus and firewall (firewall) in one bottle say, it does not slow down, does not freeze and is suitable for both beginners and advanced users. I’m not sure about their antivirus, since it always seemed to me that the main direction is still a firewall, and the antivirus is in the form of an application.
I want to warn you right away that the article will be large, so you can use the menu for easier navigation, but after reading you will have a good understanding of Outpost Security Suite 9
.
Outpost Security Suite includes a firewall, which in my opinion is one of the best (if not the best). Using it, you can safely monitor the network activity of all programs that are installed on your computer (including system processes).
Fine tuning
Component settings are concentrated in the Settings window (Figure 21).
On the left side of this window there is a tree of components. By selecting one of the elements in this tree, you can set its settings on the right side. At the same time, for some components you can call up additional dialog boxes with settings. This creates a fairly extensive system of dialog boxes with settings, which, nevertheless, has a common logic, and it will be difficult for an experienced user to get lost in the settings. Beginner users do not need to change such settings at all, since the main protection settings are placed in the main window of the Outpost Security Suite 8.0 interface.
Figure 21. Outpost Security Suite 8.0 settings window
“General” settings section contains the main settings responsible for the following functionality of Outpost Security Suite 8.0:
- graphical interface;
- Outpost Security Suite startup mode;
- detecting when the application goes into full screen mode;
- SmartScan scanning optimization technology;
- self-defense;
- license management;
- Password protection of access to Outpost Security Suite settings;
- general security configuration;
- update;
- ImproveNet service , with the help of which Agnitum collects telemetry information from protected computers (cloud service);
- user notifications.
“Application Rules” settings section contains settings that are responsible for the protection rules applied to applications installed on the system.
“Firewall” section is dedicated to personal firewall settings. In the subsections of this section you can configure:
- rules for protecting the network;
- parameters of protected networks;
- settings related to repelling network attacks;
- configure a blacklist of IP addresses.
“Antivirus + Antispyware” settings section is dedicated to the antivirus component of system protection. The settings of this component are divided accordingly into components:
- real-time protection;
- on-demand scanner;
- scanning mail traffic.
“Proactive Protection” section is devoted to the HIPS component of protection. The settings are divided into the following components, according to the modules of this protection layer:
- Anti - Leak module – blocks dangerous actions of programs;
- system and application protection module;
- module for blocking access to files and folders;
- protection of removable media.
“Web Control” section includes settings related to monitoring web traffic. This security module includes several submodules:
- ID Block – a module for preventing the sending of private user data to untrusted Internet resources;
- module for protection against malicious sites, as well as ad blocking.
Finally, the “Logs” of the Outpost Security Suite 8.0 settings refers to fine-tuning the reporting of the operation of this security product. Also from this settings section you can open the folder where Outpost Security Suite text logs are stored.