ATTENTION! Do not under any circumstances open any shortcuts or files on a flash drive - you can launch a virus on your PC.
Hi all! Today I encountered the following problem: I open a flash drive, and instead of files there are shortcuts on it. The question immediately arose: how can this be cured, and is there any chance of recovering damaged data? At first I was even a little scared, since the flash drive contained very important documents and photographs with videos. But in the end I managed to restore them, and now I’ll tell you how I did it.
As I guessed, if all the files or folders on the flash drive become shortcuts, it means a virus has worked there, and this can only be the reason. Some folders may disappear, and the volume of the flash drive itself and the occupied memory does not change and remains at the same level. Also, some may have other files and folders with the “lnk” extension.
Treating a flash drive with one BAT file
If you are too lazy to do all of the above, you can create a file that will do all this for you. For this:
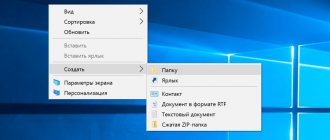
- On your desktop or any other area of your computer, right-click and create a text file.
- You can call it whatever you want - it doesn't matter. Now go inside and write 4 lines:
attrib -s -h /s /d rd RECYCLER /s /q del autorun.* /q del *.lnk /q
- Click "File" and "Save."
- Now close it, right-click and select “Rename” from the list.
- Instead of "txt" enter "bat". There must be a period before this. Confirm the change by clicking "Yes".
Now it has turned into a launchable “BAT” file. To activate it, double-click. After that, through the console, he will do all the same actions that you did a little earlier: make the folders visible, delete the folder with the virus and shortcuts.
NOTE! If this method does not help, then most likely the virus’s folder is called something else, so you need to use manual removal.
Getting missing folders back
The next step is to return the folders that have become shortcuts on the USB drive. This is where the fun begins. The fact is that depending on the modification, the method by which the virus hid the directories may be different. In the simplest case, just go to the flash drive. There you will see hidden folders (we included their display above). You just need to right-click on each of them, open its properties and uncheck “Hidden”.
But if a more advanced malware has worked, then most likely this checkbox will be unavailable and you will not be able to easily remove the “hidden” attribute from the folder after the virus.
In this case, right in the root of the flash drive, create a text file in which you need to copy this line:
attrib -h -r -s -a /D /S
Close the text editor and change its extension from *.TXT to *.BAT. Right-click on the file and select “Run as Administrator” from the context menu.
After this, the folders should become visible. If something is not clear, watch the video instructions:
Automated option
For those who do not like to do everything manually, preferring to rely on scripts, there is also a great way. It consists in the fact that you need to again create a BAT file on a removable drive, open it with Notepad and copy the following code there:
:lable cls set /p disk_flash=”Input USB Drive Name: » cd /D %disk_flash%: if %errorlevel%==1 goto lable cls cd /D %disk_flash%: del *.lnk /q /f attrib -s -h -r autorun.* del autorun.* /F attrib -h -r -s -a /D /S rd RECYCLER /q /s explorer.exe %disk_flash%:
Close the text editor and save the changes. We launch the script for execution. At the beginning, he will ask you to indicate the letter under which the flash drive is displayed in Explorer. After that, it will delete the RECYCLER folder, the autorun file autorun.inf and return the attributes to the folders that have become shortcuts. This option works great in most cases with a bang. But if you suddenly come across a more cunning modification of such a virus, then you still have to roll up your sleeves and work with your hands.
Checking the system for virus autorun commands
In some cases, viruses register themselves in the system startup. Manually check the following registry branches (regedit.exe) for suspicious entries:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
– these programs run when the computer boots - HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Run
– programs that automatically start when the current user logs in
Delete all suspicious entries and unfamiliar programs (you won’t do anything bad, and even if you disable the startup of some necessary program, you can always launch it manually after logging in).
Other ways to autostart programs on the system are described in the article.
Removing the virus
The shortcuts launch the same file. Right-click on any shortcut and click properties. In properties, click on the shortcut tab and look at the object item.
The object item is quite long, but it is easy to find the path to the virus in it, most often it is something like 456325.exe in the Recycle folder on the flash drive itself. We delete it along with the folder and now clicking on the shortcut is not dangerous.
Cleaning a flash drive from a virus
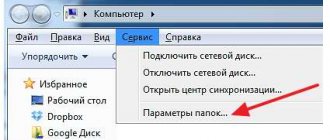
First you need to enable the display of hidden files and folders on the flash drive. To do this, go to the explorer properties in the view tab. If you have Windows 10, of course. For older versions, this is done in the control panel: personalization tab - settings - view.
We went into properties, now let’s take a couple of simple steps:
- Uncheck the “hide protected files” box.
- Check the “show hidden” box.
Done, now you need to finally clean the flash drive from the virus. In order not to format the entire flash drive, which may still not work, you can look at what these shortcuts launch. According to the standard, they all open this virus. Just go to the shortcut properties and see for yourself by detecting double launch. The first opens a folder, the second a file with a virus.
This is shown in the "Object" line. There you will see the name of the folder with the virus, where the name of the virus itself will end in “.exe”. Now you need to find among the shortcuts the name of the folder that was registered in the “Object” line. There is a virus file there. We send this folder to Hades along with the virus (Delete button).
Now you need to restore your folders, and the remaining shortcuts can be deleted. All folders on the flash drive are now hidden, you can tell by their transparency. Now you can’t just uncheck the boxes; you need to turn to the greatest intelligence: the command line.
There are two ways to solve the problem. First:
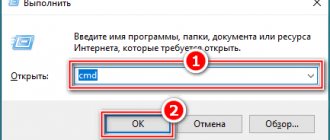
- Open the command line. To do this, press the Win+R key combination and enter cmd in the search, and write the following two commands there
- cd /df:\ (the letter f here is the letter of the removable disk, that is, a flash drive, yours may be different)
- Press Enter and enter the following command
- attrib -s -h /d /s
- Enter again, and now your folders will return to their original form.
The second way is also not difficult, but here instead of the command line, you will need to create a batch file on a flash drive. He does everything the same.
- Create a text file on your flash drive
- Write into it the command you already know attrib -s -h /d /s
- Now save it by adding .bat to the name
- Run the file and wait for the recovery to complete. Ready.
If you have a lot of files on your flash drive, the recovery process may take a little longer, no matter which path you choose. The main thing is don't worry, everything will be fine, just wait.
When the process is finished, change all the values in the Explorer properties. That is, what we did at the very beginning, only in reverse.
After the entire procedure, do not forget to check your flash drive for infected objects with antivirus or Windows Defender, just in case. It's better to scan the entire computer.
Solving problems and other methods of virus removal
The above two methods are the best, in my opinion, for fighting the shortcut virus. However, problems can arise in the form of an "Access Denied" error - often on a drive with the NTFS file system and rarely on FAT and FAT32.
- In Fixfolder, make sure you change the letter to match your drive letter.
- At the command prompt, make sure you type the command correctly, including spaces.
If you do everything correctly, you still see the error:
- Run a CHKDSK check using the command line (see) and try everything again.
I could end the article here, since I think that the methods I indicated above are sufficient. But still, if it didn’t help someone, here are some useful programs that can also fight the “shortcut” virus:
Content:
- How does virus infection occur?
- How to avoid infection?
- What happens when infected with viruses?
- How to get rid of viruses on a flash drive?
- How to get rid of a virus on your system hard drive?
- How to remove a virus from startup
Malware and virus software can have different effects on the operating system.
Some viruses delete data or steal important files from your computer. Others create shortcuts to arbitrary files or shortcuts with dubious advertising and Internet resources.
In addition, recently a high activity of viruses has been noticed, making shortcuts from important files through which it is impossible to open data .
Such viruses can be found on a hard drive or located on removable media , interfering with comfortable use or even replacing any connected device with a useless shortcut.
Recovering files on a flash drive
Now we can safely remove all the shortcuts. But our files are still hidden and system files (they are transparent). You can't just remove these attributes. There are several ways to restore the initial attributes of our files:
First way
Open “Start” - “Run” - Enter the CMD command - press ENTER. A black command line window will open in which you need to enter the following commands:
- cd /df:\ press ENTER, where f:\ is the letter of our flash drive (may differ from the example)
- attrib -s -h /d /s press ENTER - this command will reset the attributes and the folders will become visible.
Second way
1. Create a text file on a flash drive.
2. Write the command
attrib -s -h -r -a /s /d , rename the file to 1.bat and run it.
3. .
Unpack the archive → copy the “1.bat” file to the USB flash drive → run this file. If there are a lot of files on the flash drive, then the process of removing attributes can take up to 15 minutes. To prevent virus infection, we strongly recommend using anti-virus programs. Check your computer for viruses. After connecting the flash drive, check it for viruses. You can check the flash drive with Kaspersky antivirus. You can read how to use Kaspersky legally and for free in this article Journal keys for Kaspersky 2020
Removing virus executable files on a USB flash drive
The first step is to get rid of the virus executable files. This can be done using any antivirus (fortunately, there are a lot of free or portable versions, such as Dr.Web CureIt or Kaspersky Virus Removal Tool), but if it is not there, you can try to find and neutralize the virus manually. How to find the files of a virus that has infected a USB flash drive?
In this example, RECYCLER\e3180321.exe is the same virus. Those. The virus file named e3180321.exe is located in the RECYCLER folder. We delete this file, or maybe the entire folder (I recommend checking the presence of this folder both on the infected flash drive itself and in the system directories C:\windows, C:\windows\system32 and in the profile of the current user (more about them below)).
- on Windows 7, 8 and 10
- C:\users\username\appdata\roaming\ - in Windows XP
- C:\Documents and Settings\username\Local Settings\Application Data\
If these directories contain files with the extension " .exe"
", then most likely this is the executable file of the virus and can be deleted (on an uninfected computer there should be no .exe files in this directory).
In some cases, such viruses are not detected by antiviruses, because they can be created in the form of .bat/.cmd/.vbs script files, which, in principle, do not perform any destructive actions on the computer. We recommend that you manually check the flash drive for files with such permissions (their code can be viewed using any text editor).
Now clicking on a shortcut is not dangerous!