When connecting to a global computer network, which at one time was called the Internet, special access protocols are used. One of the newest is IPv6. Not everyone knows what it is and how it all works. Therefore, it is worthwhile to dwell separately on the technology used and on the activation of protocol settings, taking into account the fact that the material will be presented in the simplest possible terms, aimed not at professionals, but at ordinary users.
IPv6: what is it?
Despite the fact that today there are quite a lot of protocols for using an Internet connection in the form of the most commonly used IPv4 or access to mail servers like POP3 or SMTP, we will focus on the sixth version of IP.
The actual procedure for accessing the World Wide Web is to identify each connected computer. Moreover, any computer or mobile device must have its own completely unique identifier, called an address. In other words, the essence of using any protocol is to ensure that there is not a single duplicate value in the world.
Why is this necessary? Yes, only so that the response from the requested server or the download of data is carried out exactly on the specified device, and not on another system. The IPv6 protocol itself is responsible for generating and assigning such identifiers. Roughly speaking, when it is activated, a unique combination is created that corresponds to each device. At the same time, it is he who generates an almost unlimited number of such identifiers, which, given the development of mobile technology, is becoming especially relevant these days.
IP addresses in IPv6
There are several types of v.6 addresses:
- unicast (Unicast);
- group (Anycast);
- multicast (Multicast).
Each has its own characteristics. A packet sent to unicast always reaches exactly the interface to which it was sent. Anycast is indistinguishable from Unicast in its syntax. But unlike the first one, they are sent not to a specific interface, but to an entire group of them. Typically, a packet sent to a specific device is sent on the first interface according to the metric. Anycast is recognized by routers.
Multicast is addressed to a whole group of interfaces. Moreover, the data packet always reaches each interface present in the list. When writing, the character code is displayed as eight 4-digit hexadecimal numbers, all separated by a colon. Each group contains four symbols.
In the memory of a PC and other equipment, the address looks like this:
2001:0db8:11a3:09d8:1f36:8a2e:07a8:765d.
If you have a group consisting of only zeros, you can simply replace it with a colon.
IP v.6 has reserved groups:
- fc00:: - replaces Site-Local;
- fec0::feff – range marked as obsolete;
- fe80:febf – analogue of 169.254.0.0/16 in the old standard;
- 2001:db8:: - used as examples for documentation.
History of the creation and implementation of IP protocols
Information sources claim that the development of such techniques began in the 70s of the last century. Then one of the technologies was called the Internet Protocol, or, in the English version, Internet Protocol, which is where the abbreviation actually comes from.
The fourth version, which was once the most current, was considered the height of perfection, since it could generate 32-bit addresses distributed through DHCP servers in the amount of about four billion identifiers. With a population of five billion on our planet and a fairly limited number of users of the Global Wide Web, this was considered the height of perfection. But at the end of the 20th and beginning of the 21st century, with the increase in the number of computers and mobile devices, the fourth version of the protocol could no longer cope with the tasks assigned to it. That is why the idea of creating a new IPv6 protocol arose. What it is?
The technology was based on increasing the bit size of the assigned address, but it was preceded by the appearance of an intermediate fifth modification, which received the abbreviation ST/ST2. Under the conditions of that time, it looked exclusively like an attempt to create something new, but in practice it was practically not used in computer systems (except that it remained a kind of testing version).
Advantages and features of the IPv6 protocol
POP3 vs IMAP: which protocol allows you to receive email on any device
The main advantage of the IPv6 protocol is not only the solution to the problem of the shortage of IPv4 addresses, but also of all subsequent protocols. Thanks to the IPv6 protocol, the need to change network addresses - NAT, which previously solved the problem of the shortcomings of IPv4 addresses, has been reduced.
IPv6 uses multicast routing and simplified headers, which greatly increases routing efficiency.
IPv6 provides built-in authentication, privacy protection, and flexible options with support for extensions.
How does the sixth version of IP differ from the fourth?
If you look at the difference between the fourth and sixth versions, it is quite obvious that in the case of using IPv4, the full length of the address is 32 bits. The IPv6 address has a dimension of 128 bits, which allows you to generate a number of probable identifiers that is millions of times greater than the capabilities of the fourth version. For comparison, it’s worth at least looking at the numbers presented below.
Some experts argue that such an indicator has no restrictions, although the final number can be calculated. But from a practical point of view, even if the world’s population doubles, which will entail an increase in devices connected to the Internet, this will not affect the addresses in any way.
Checking work
So, IPv6 has been enabled and configured. Now all that remains is to make sure that the protocol is actually enabled and works without problems.
To check the connection we use the same ipconfig command. After all correctly performed procedures and settings, the protocol should be displayed on the screen. If you set out to view the address, you can simply click on the network connection icon in the system tray and select the status menu. The same can be done from the “Control Panel”, where you select the appropriate section of network connections and then go to the active connection.
IPv6 without network access: how to determine if the protocol is supported?
Now let's move on to practical actions. Configuring IPv6 should begin with checking whether the protocol is supported in the computer system itself. You should immediately pay attention to the fact that if the provider providing Internet connection services does not support a DHCP server of the sixth version, no matter how much you try to configure the use of the sixth version of the protocol, nothing will work - it will still remain inactive.
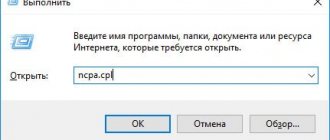
In the simplest case, to obtain information, you should use the command line, called from the Run menu by entering the cmd abbreviation. To the console itself you need to enter the standard ipconfig command for a single terminal or ipconfig /all for all computers connected to a local network. If the screen does not show active IPv6 access, you will have to configure it. And this absolutely does not mean that the protocol is not supported - it is simply not used (or the provider does not have DHCPv6).
By calling the protocol settings with the ncpa.cpl command through the Run menu, you can see that it is in the system parameters, but the checkbox is not checked (or installed, but the protocol is not configured). By the way, all latest generations of Windows operating systems support the sixth version of the protocol.
IPv6 Penetration Tester Toolkit
Before moving on to vulnerabilities and attacks, it’s a good idea to consider what tools a pentester has in his arsenal. Until recently, there was only one set of utilities for carrying out attacks on the IPv6 and ICMPv6 protocols. It was THC-IPV6 from the well-known Mark van Houser, the same author of the THC-hydra brute forcer and a host of other irreplaceable tools. It was he who became seriously interested in this topic in 2005 and began closely researching the IPv6 protocol. Until recently, he remained a pioneer, but in the last year the situation began to change. More and more researchers are turning their attention to IPv6, and, accordingly, new utilities and new scanners have begun to appear. But today THC-IPV6 is still the best set of utilities for pentesters. Its kit already includes more than 60 tools, divided into various categories - from scanning and mitts to flooding and fuzzing. But let’s not forget the scapy tool, a utility that allows you to manually create any packages with any headers, even if such variations are not provided for in any RFC.
How to determine your own IP address?
You can determine whether an IPv6 address is involved quite simply by using the Network and Sharing Center section in the Control Panel, where you select the properties of the current connection and click the details button in the window that appears.
A value must be specified next to the local IPv6 address. If it is missing, the protocol is simply not used. Please note that both versions of the protocol are used simultaneously - this is how it should be.
What are other news
Naturally, the changes do not end with just addresses. The title was also significantly simplified (see Fig. 2).
Rice. 2. Comparison of IPv6 and IPv4 headers
Now everything that is not mandatory for routing a packet from point A to point B has become optional. And since it’s optional, it means it moves to the extension header, which lies between the IPv6 header and TCP/UDP data. Fragmentation, IPsec, source routing and many other functionalities already live in this extension header.
They have dramatically simplified the task for routers, because they no longer need to recalculate checksums, and as a result, IPv6 is processed faster than IPv4. Checksums have been removed altogether. Firstly, the frame at the L2 level has a CRC, and secondly, higher-lying protocols (TCP) will also ensure delivery integrity. As a result, unnecessary fields were removed from the header, it became simpler, faster and more reliable.
Automatically obtain addresses
Now comes the most important part. In the case where the user has IPv6 without a network, you can use the automatic settings offered by the system itself and most Internet providers.
After clicking the settings button in the above section in the parameters window, you should use automatic acquisition of the IP address, DNS settings, gateway, subnet mask, etc. In this case, the machine will immediately receive a dynamic address, which will later be used to identify it on the network connection and when using the Internet.
Address presentation
IP consists of two main components:
- network numbers;
- node numbers.
The recording format depends on the network it is used on. If the network space is isolated from the global Internet, then the administrator selects an IP from a specially reserved range (10.0.0.0/8 or 192.168.0.0/16). In the case where the local network is part of the Internet, the protocol is determined by the current provider and is presented in a different format.
A node number is assigned to a specific piece of equipment regardless of the local location of the node. Since the router simultaneously enters several network spaces. Each port is assigned its own character code.
IP recording can take two forms:
- decimal;
- binary.
The decimal representation is used only to simplify the presentation on the computer screen for the convenience of the user. The binary representation method reflects the immediate appearance in the computer's RAM. On average, the length of an IP is 4 bytes. Therefore, if you present it in binary form, it will look like a 32-bit number - 0 and 1 placed in sequence.
The IP address 213.128.193.154, when converted to binary form, will look like this: 11010101 1000000 11000001 10011010. Using this representation format, you can easily determine the class.
It is characterized by the first digits in a binary number located at the beginning of the record:
- class "A" - 0;
- class "B" - 10;
- class “C” - 110;
- class “D” - 1110;
- class “E” - 11110.
Setting parameters manually
If problems with IPv6 are observed with such settings, the Internet or network can be connected by setting the parameters manually.
In this case, we are talking about settings provided by the provider or network administrator. In other words, you will have to enter all the above values yourself. Here it is worth noting that in most cases, in the additional settings, you must check the box next to the item that prohibits the use of a proxy server for local addresses. In any case, you need to enter the data very carefully, since even one incorrectly entered number can nullify all attempts to establish a connection.
Automatic setup
Now let's look at the IPv6 configuration. The Internet connection will only benefit from this (again, the setting is only relevant if the provider supports this protocol).
In most cases, to correctly configure the IPv6 address received by the computer terminal, you do not need to manually enter it. This is due to the fact that almost all large provider companies have an active DHCPv6 server in their own network, from which, in fact, IP is assigned, that is, the server itself issues an IPv6 address to a specific machine.
Thus, for the simplest setup, you should use the fields for automatically obtaining the IP address and DNS server address. If automatic configuration is not possible, but IPv6 is supported, the IP address can be obtained automatically, but the values for the preferred DNS server will have to be entered manually. And there are some snags here.
Alternative DNS Settings
The automatic default DNS server settings (preferred and alternate) may not work. Sometimes even manually setting the values provided by the provider may not have an effect. Therefore, many companies, in particular Yandex and Google, provide their own addresses that will be used in such settings.
For Google, combinations of four eights, two fours and two eights are used, or vice versa, and for Yandex services - two sevens, two eights and another eight for four address fields. However, when it comes to setting up TV smart panels, Yandex suggests entering combinations of numbers and letters, which looks very inconvenient.
But the main problem with using such settings compared to automatic ones or those offered by the provider is that the user will receive a connection speed limit, for example, at 50 Mbit/s, although the provider has declared support, say, 100-150 Mbit/s. You understand that there is no need to talk about any downloading of music or video content. Even when using torrent clients, the speed will be even more limited. So, for example, with a connection speed of 100-150 Mbit/s in a torrent, if there is a maximum number of distributions, you can get a download speed of 3-4 Mbit/s, with a value of 50 Mbit/s - several times less.
So think about whether to use these services. The use of such parameters is justified only if other settings do not work and the connection is not established.
What is ipv6, and why aren't we using it yet?
IPv6 has been in development since 1998 to address the shortage of IP addresses available under IPv4, but despite its efficiency and security benefits, adoption has been very slow. For the most part, the dire warnings about Internet address shortages have stopped because, slowly but surely, the transition from Internet Protocol Version 4 (IPv4) to IPv6 has begun. But before we see where we're going with IPv6, let's go back to the origins of Internet addressing.
What is IPv6 and why is it important?
IPv6 is the latest version of the Internet protocol that identifies devices on the Internet. Every device that uses the Internet is identified through its own IP address to surf the Internet. In this regard, it's like the streets, addresses and zip codes you need to know to send a letter.
The previous version, IPv4, used a 32-bit addressing scheme to support 4.3 billion devices, which was considered sufficient. However, the growth of the Internet, the number of personal computers, and smartphones proves that the world needs more addresses.
Fortunately, the Internet Engineering Task Force (IETF) recognized this 20 years ago. In 1998, he created IPv6, which instead uses 128-bit addressing to support approximately 340 undecellions of addresses (or powers of 2 to 128, if you prefer). Instead of an IPv4 address type consisting of four sets of one- or three-digit numbers, IPv6 uses eight groups of four hexadecimal digits separated by colons.
What are the benefits of IPv6?
The IETF has included improvements to IPv6 over IPv4 in its work. IPv6 can process packets more efficiently, improve performance, and improve security. This allows ISPs to reduce the size of their routing tables by making them more hierarchical.
Network Address Translation (NAT) and IPv6
The adoption of IPv6 was delayed in part because of Network Address Translation (NAT), which takes private IP addresses and turns them into public IP addresses. Thus, a corporate machine with a private IP address can send and receive packets from machines located outside the private network that have public IP addresses.
Without NAT, large corporations with thousands or tens of thousands of computers will gobble up huge numbers of public IPv4 addresses if they want to communicate with the outside world. But these IPv4 addresses are limited and almost exhausted to the point that they will have to be limited.
NAT helps alleviate the problem. With NAT, thousands of computers with private addresses can be exposed to the public Internet using a NAT machine such as a firewall or router.
Complexity, cost and time required to complete are all reasons for this delay in implementation. Additionally, some projects were delayed due to software compatibility issues. For example, a January 2020 report said a bug in Windows 10 was "undermining Microsoft's efforts to roll out an IPv6-only network at its Seattle headquarters."
When will the transition to IPv6 happen?
The Internet Society said the price of IPv4 addresses will peak in 2020 and then prices will fall once IPv6 deployment passes the 50% mark. Currently, according to Google, IPv6 has been implemented only by 20% - 22% in the world.
As prices for IPv4 addresses begin to fall, the Internet community encourages businesses to sell off their existing IPv4 addresses to help finance IPv6 deployment. MIT has already done this. The university concluded that its 8 million IPv4 addresses were "surplus" and could be sold without compromising current or future needs, since the university had 20 nonillion IPv6 addresses available. (A nonillion is a number followed by 30 zeros.)
Additionally, as deployments increase, more companies will begin to charge for the use of IPv4 addresses while providing IPv6 services for free. UK ISP Mythic Beasts says that "IPv6 connectivity comes as standard" and "IPv4 connectivity is an optional extra".
When will IPv4 be "turned off"?
Most of the world "ran out" of new IPv4 addresses between 2011 and 2020, but we will not be completely deprived of them as IPv4 addresses are sold and reused (as mentioned earlier). There is no official shutdown date, so people don't have to worry about their internet access suddenly disappearing one day. As more networks move to IPv6, more content sites support the new protocol, and more end users upgrade their equipment to IPv6 capabilities, the world will gradually move away from IPv4.
Functionality check
Finally, after all the settings have been made, the system needs to be checked. In this case, you cannot rely only on the presence of a connection to the network or the Internet, since in most cases both versions of the protocol are used - both the fourth and the sixth.
To obtain updated data, we again use the ipconfig command, as indicated above, and check that the information contains an indication of the sixth version of the IP protocol with the assigned local address. As an alternative, you can use the network properties, where you click the details button. By the way, if you have Wi-Fi-based wireless connections, the desired menu can be called up directly by clicking on the status icon in the system tray.
End Host Threats
And since we’re talking about RA, let’s move on to threats to end hosts, and in particular to those hosts that were not planned to work with IPv6. That is, let’s consider an attack on hosts running in the default IPv6 configuration on a regular IPv4 network. What will happen if any modern OS receives the RA package? Since any system now supports IPv6 and expects such packets, it will immediately turn into a so-called dual stack. This is a situation where both IPv4 and IPv6 are used simultaneously within the same OS. In this case, a whole series of previously inaccessible vectors will immediately open. For example, it will be possible to scan the target, because IPv4 is usually filtered, and IPv6, as we already know, is often not thought about at all.
Additionally, in most operating systems, IPv6 takes precedence over IPv4. If, for example, a DNS request comes, then there is a high probability that IPv6 will work first. This opens up enormous scope for various MITM attacks. To carry out one of the most effective ones, you will need to place your own malicious IPv6 router. Each IPv6 router must join a special multicast group. This is FF02::2. As soon as the router joins such a multicast group, it immediately begins sending messages - RA. Cisco routers send them every 200 seconds by default. Another nuance is that clients do not have to wait 200 seconds, they send an RS message - Router Solicitation - to this multicast address and thus immediately require all the information. This whole mechanism is called SLAAC - Stateless Address Autoconfiguration. And accordingly, an attack on it was developed with the obvious name SLAAC Attack.
The attack is that you need to install your own router (do not take it literally, any Linux or even a virtual machine can act as a router), which will send RA messages, but this is only half the battle. The attacker will also need to run a DHCPv6 server, DNSv6 and a NAT64 translator. As a service capable of sending RA messages, you can use Router Advertisement Daemon (radvd), this is an open source implementation of an IPv6 router. As a result, after the correct configuration of all daemons, the victim will receive RA and turn into a dual stack and all the victim’s traffic will go absolutely unnoticed through IPv6.