20.07.2019
While using cellular services, subscribers are faced with the problem of damaged or lost mobile numbers. Some clients then contact the office for a new one, but the easiest way in this case is to make a duplicate MTS SIM card. This procedure will allow you to save money, as well as all the information that was saved on the old number.
Indeed, it is possible to make several copies of a product if the need arises. Thus, the company allows you to use several gadgets at the same time, but without constantly rearranging the card. Thus, funds, as well as traffic packages, SMS or minutes, will be spent simultaneously. That is, manufacturing the same SIM card does not increase the volume of options and services provided.
Why duplicate a SIM card?
Each client has his own reason and why he needs to produce the same SIM. Among the most common ones are:
- Losing a cell phone. In this case, the lost plastic is blocked, and a new one is made for the client, with the same data and account status.
- Damage to the plastic itself.
- The need to use several electronic devices at the same time.
Often, two SIM cards for one MTS number are prepared for travel in order to save money in roaming and enjoy the old prices for the services and options used outside the region where the plastic was purchased. Some subscribers prefer to store it specifically in case of unforeseen circumstances.
The procedure does not always bring only benefits to the user. In some cases, usage becomes more expensive, especially when trying to purchase new tariff plans.
How clones work and why make them
Clones are copies of original applications, functioning, as a rule, without slowdowns, freezes or glitches. You simply get two identical versions that you can work with separately.
The simplest example is an account on VKontakte. For example, you created one page for an online business, and use the second for entertainment purposes, to communicate with friends, etc.
We do the same with games. Does your family love to play the same game, but everyone wants their own account? No problem. Duplicates are also useful in a number of other cases, for each user individually.
How to order a duplicate MTS SIM card
Today, several methods of making a clone are practiced. Before the procedure, it is necessary to block the old SIM so that in the future it cannot be used for personal gain. Both blocking and plastic production will be carried out at the operator’s office upon presentation of the user’s passport.
When visiting a sales office, you must pass user identification. To do this you will need:
- Provide the details of the document for which the SIM was registered to a specialist.
- Answer a special question out of three proposed. The questions relate directly to the old number.
- Provide PUK code. As a rule, it is indicated in the plastic documentation. This procedure will simplify the entire duplication process.
If there is no starter package, a specialist may ask questions during registration:
- about the old APN access point;
- last used contacts;
- recent transactions with account and number;
- the size of the last replenishment;
- the amount of funds in the account.
The operation is performed free of charge. As a result, the subscriber receives exactly the same product with the same options connected, as well as contacts (if they are stored on the chip) and balance. You can check all this upon activation and the first connection.
It is possible to make a block in advance yourself using an online directory. But many users are interested in how to make a duplicate MTS SIM card at home and whether it is even possible to carry out this procedure without the help of the company. Such a procedure is indeed possible. As a rule, a special tool is used for this - the so-called duplicator. With its help, it is possible to obtain a clone of plastic onto a regular template or multicard. The cost of a clone in this case will be from 600 to 900 rubles. It should be understood that it is prohibited to carry out such procedures within the framework of the law, using clones without blocking the old product is also illegal and resorting to this operation is not recommended.
Why do you need a cloned SIM card?
At this stage, it’s worth thinking about why a cloned SIM card might be needed at all?
There are two standard approaches. Firstly, the subscriber himself often needs to connect several SIM cards into one, called a multi-SIM card. Such a combined card, when the phone is turned on or when a special combination of characters is entered from the keyboard, selects the required pair from the IMSI and Ki values in its memory. After which it works on behalf of another SIM card. Today on the market you can find solutions that allow you to combine data from sixteen regular SIM cards into one multi-SIM card.
Secondly, cloned SIM cards are used by criminals to speak at someone else's expense. Although in this case, there is a problem with receiving incoming calls, so such illegal duplicates are usually used for a short time and only for outgoing calls.
How to clone a mobile phone remotely?
If you are waiting for your phone device to be cloned or want to monitor someone's mobile phone using Android remote monitoring
Then you have to follow some basic steps of phone cloning app to get all the data of your old phone and download it to your new phone. Let's discuss all the steps you need to follow to clone a mobile phone from an Android phone.
Install TOS app on your Android phone secretly
Initially, if you really want to clone a specific phone with the clone phone app to get all the data or you want to track someone's phone activities like text messages, incoming and outgoing calls, shared media files, passwords and more. Once you install the Android phone cloning app on the target phone, you will be able to track all the activities of the mobile phone and even transfer the data of the old mobile phone to the new one without facing any problems. Once you have installed it will be your headache, either you want to clone the phone for your personal reasons, or you are looking into someone's phone.
Always back up using a data backup app
backup date
is very necessary because at any point of time, your mobile phone may suffer from a catastrophic condition and you may lose all the data on your phone within neon seconds.
Thus, it is very necessary for a person who is looking forward to cloning or tracking someone's device or transferring data from an older device to a new one. Everything should have data backup on your Android gadgets. So I would prefer a tool that is best for creating a data backup for Android mobile phone data and at the same time will behave like a clone of Android phone
or spy on any other phone like uplink to their data too in your device and keep track of the ones you love the most.
TheOneSpy android spy software is that tool which helps you to clone Android phone in any way or monitor the activities of the target phone. Once you have installed the data backup software, all the installed data on your older Android phone will be synced with yours which can be saved on your new Android mobile device.
Electronic calendar and contacts
If you want to get all the calendar and contacts data, you need to use cell phone spy app
,The user will be able to retrieve phone book data, calendar ,events and task logs.
On the other hand, one can also monitor the email content and get the email data using the best Android monitoring app and the user will become familiar with the Gmail email content
.
Media files
Sometimes people store music files and photos and more on their Android phone and don't want to delete or lose entire files. User can get data using multimedia files spy mobile app
and get all the media data and transfer it to the new phone. On the other hand, if someone controls someone, then the user can target the phone.
Password and bookmarks
using keylogger app to spy on android
and grab all the keystrokes applied to the target phone.
Finally, you will have all types of keystrokes such as SMS keystrokes and email keystrokes. The user can also view the bookmarks and visited websites of the target cell phone browser using the browsing history of Spy Cell Phone TOS
.
SMS and MMS messages
When it comes to receiving your data SMS, MMS messages, you just need to use text message spy on Android phone
,The user will have the content of SMS, Messages, MMS, BBM Chat Messages and Ticker Notifications.
IM conversations on social networks
There are many users who want to save the entire conversation for various reasons, such as social networking applications Facebook, Tinder, Line, Vine and others. Someone accidentally deleted a conversation or forgot their password and ID. They can use IM from mobile phone tracking software and recover password and email ID using keyloggers and online control panel.
Clone an Android phone
Once you take all these mentioned steps
one by one at the end you will know that you have all the data of your old android phone or you have the data of your target android phone. Now you can deliver all your old phone data to the new one and using all these you can find out all the activities of your target person to the fullest.
Conclusion:
TheOneSpy Encyclopedia is the one and only tool of its kind that is best for cell phone cloning
and also track the activities of the target phone.
Bring the best cell phone spy app
and use it for a variety of tasks like cloning your phone and backing up your data.
Recently, cases of fraud related to the theft of mobile phones or the issuance of a duplicate SIM card by a cellular operator to unauthorized persons have increased sharply. Attackers thus have the opportunity to gain access to your mailboxes, electronic wallets, card accounts, social networking accounts and other services, which have in common the fact that they are all tied to your phone number (usually one).
Increasing the level of security on your accounts by linking a cell number to them, and this is recommended by all well-known online services, can result in even greater problems for the account owner. Fraudsters can not only steal your money using “your” SIM card, but also use your personal data in the future. Now you really need to be extremely careful and follow the safety measures that will be discussed in the article.
In this review, we will talk about methods of SIM card fraud, how to prevent them, and what to do if you find yourself in a problematic situation.
In-app cloning
Optimizing Android applications when turned on - how to remove
Unfortunately, the standard cloning function is not built into all shells. If the operating system version does not allow you to create a clone program for Android using standard tools, you can use specialized utilities. Among the advantages of this option is the ability to protect duplicates with a graphic key or fingerprint.
APP Cloner
This is a popular universal tool, the principle of cloning is to create a copy of the desired program with a modified package name and signature. Previously, the utility was available in the Play Market, but such software is often removed from the service, so at the moment it can be safely downloaded from trashbox.ru.
Creating and setting up a copy in APP Cloner
Duplicating Android applications using App Cloner can be done using the following algorithm:
- Install the program and run it.
- Provide access to some smartphone data by clicking on the “I Accept” or “Allow” button in the system window that opens.
- From the main screen of the utility, select the application for cloning. If the program you need is not in the proposed list, you can click on the “+” icon and select it in the list that opens.
- Click on the “Add to App Cloner” button.
- In the window that appears, set certain settings and distinctive features for the program, for example, rotate or reflect the icon, change its color, or overlay text on top of it.
- Finish the setup by clicking the checkbox or the word “OK”.
- Within a few minutes, the program will create a copy and notify you about it with a system message.
- Click on the “Install” button. After this, a clone of the Android application will appear on the smartphone’s desktop.
- If a shortcut is not created on the main screen, you need to go to App Cloner and run the program from there.
Attention! Cloning instant messengers and social networks is only possible for an additional fee.
The application allows you to create clones of downloaded but not installed APK files, and also automatically tracks updates for the originals and notifies you when their copies can be upgraded. At the same time, duplicates created in App Cloner become completely independent objects and continue to work even after the utility is removed.
Parallel Space
The program offers an alternative approach to cloning and creates a virtual box within which copies of applications are launched. This provides better compatibility, but does not allow duplicates to be used after the utility is uninstalled. It also does not provide for creating multiple copies of one file.
How to make a clone on an Android phone in the Parallel Space program:
- Download Parallel Space from the built-in app store.
- Provide all permissions necessary for correct operation.
- Click on the “Add Application” tab.
- From the list of programs, select the ones needed for cloning.
- To create a shortcut for a specific clone on the main screen of your phone, you need to hold it and move it to the “Create Shortcut” tab.
Cases of fraud
At the beginning of 2020, news spread all over the Internet about how scammers managed to rob a high-ranking official of a large sum of money. Moreover, to do this, they just had to get a duplicate of his SIM card using a “false power of attorney.” It is worth noting once again that the victim had a ban on re-issuing a SIM card in all offices of the mobile operator, except one, which was located in his hometown. Also, re-issue was possible upon presentation of a passport, and not a power of attorney.
During the day, the attackers were able to make several copies of the victim’s SIM card at once, and this was done in different cities of the country. This incident caused a storm of indignation from users. Ultimately, this situation was resolved by providing the victim with compensation in the amount of 2,000 rubles from the operator to a bonus account. At the same time, no one was held responsible for the leak of confidential information.
In the same year of 2020, there was another high-profile case that was widely discussed on the Internet. One citizen of the Russian Federation had her Beeline SIM card reissued literally several times a day, and this was done in different cities and with a short period of time between each instance of a duplicate being issued (almost simultaneously!). Her email accounts were opened and money was stolen from Yandex.Wallet. And what’s interesting is that hacking attempts were repeated with enviable persistence even after the next visit to the mobile operator’s office.
It is obvious that there was a conspiracy between the operator’s employees and the scammers, and Beeline admitted this. At the same time, it was revealed that cellular operators are unprepared for this kind of fraud - this applies to all cellular companies. And judging by reviews on the Internet, there have already been a fair number of cases of such fraud. And unfortunately, things are still the same – mobile operators cannot really protect their customers from such problems, which is why such frauds flourish.
In this case, we, ordinary people, need to become smarter and not allow such disgrace. As they say, saving drowning people is the work of the drowning people themselves. To begin with, we offer you a short excursion into the methods of fraud so that you can imagine how they can steal your money by taking possession of your SIM card.
Benefits and Features
The main advantages of the platform are demonstrated upon first opening:
- the service is suitable for all types of operating systems;
- the utilities are easy to use;
- connect the devices to each other and move them;
- the program is free;
- the widget quickly sends data, amounting to 1 gigabyte.
In addition, the application is safe. It is customized for users and stores valuable information without the risk of loss. Analog programs do not meet all reliability rules. More often they contain viruses created for illegal activities by scammers.
The main feature is compatibility with various devices, including tablets. Each user will be able to download the widget and install it on their phone. The functionality of the option does not depend on the brand of the gadget. The software has the same functions for both iPhone and Huawei. It is easy to use and will be useful to everyone.
In addition, the utilities connect to two mobile phones without using Internet traffic. Thus, users do not have to worry about spending money on Internet communications. When performing actions, available megabytes are not written off. Failures during the process are also excluded. They are due to the lack of a mobile network. However, in this case the error will not occur.
What is Hivoice on Huawei and Honor, how to disable it?
Methods of fraud with SIM cards
A fraudster has only two options to take possession of your SIM card: steal your phone or make a duplicate of your SIM card in the office. To obtain a duplicate, a whole chain of scammers is usually involved, including current or former employees of the operator’s company. A notary is also “involved” here, who in another city draws up a power of attorney without the consent and presence of the owner of the SIM card. But sometimes a duplicate is made without any powers of attorney - an obvious criminal conspiracy. After receiving a duplicate, your card is usually blocked by the operator. Let's consider the possible actions of scammers after receiving a duplicate SIM card or stealing a mobile phone.
Withdrawing funds from a SIM card
If your account does not have enough funds, then nothing will prevent another person who has taken possession of your number from withdrawing them from there (cash out). Here are just a few ways to do this:
- Mobile transfer from your account to the account of another number of the same mobile operator. The sent amount can be cashed out in various available ways.
- Payment for services/goods on the Internet. If you pay attention, often when paying for goods in an online store, you may be asked to debit money from your mobile account, albeit with a large commission, but this does not matter to the fraudster.
- Withdrawal of money to a card/electronic wallet using third-party online services, for example, MOBI.Money (https://www.mobi-money.ru/).
Withdrawing funds from a bank card via mobile banking (SMS banking)
If you are the holder of any Sberbank card (debit or credit), and you have it connected (i.e., the card is linked to a cell phone number), then it will not be difficult for an attacker to transfer money from your card account to any cell phone or to any Sberbank card. It is enough to dial a simple SMS command and send it to number 900 from the cardholder’s phone (which is no longer yours or is only temporarily not yours). This undoubtedly convenient service is called, which in the wrong hands can play a bad role - the fraudster does not even need to find out your card number in order to transfer money from it. Fortunately, the transfer amount is limited by a limit.
Access to email and e-wallets
It is not difficult to find out the victim’s email (login) - they are all freely available. This is enough to recover the password by sending the mail service an SMS message to the phone number that is linked to the account as the main number. After the attacker has entered the mail, he has access to your electronic wallets, because they are all tied to your email address, like Yandex.Money to Yandex mail, like Money@Mail.ru to Mail.ru mail, and so on. All that remains is to withdraw all the money from the wallet, unless the system suspects something is wrong. In the same way, they gain access to WebMoney or QIWI electronic wallets.
Access to a bank card
This is a more serious situation, because knowing the details of your card, even with standard transfer limits, you can withdraw serious amounts from it. How to get the details (card number, expiration date, first and last name of the holder and authenticity code CVV2/CVC2)? They are simply photographed when paying with a card at a point of sale or more technically complex methods are used (phishing or skimming). Having this data in hand, the fraudster can link it to a mobile phone account or to an electronic wallet and your money is gone (see cash withdrawal methods above)
We cannot 100% protect our SIM cards and accounts from such fraud, but we can still take some measures.
Part 1: How to clone a phone number using secret menu?
If you can clone a mobile phone number, you can use the same number on multiple devices at the same time. This is possible by accessing the secret menu on the device by entering save septic codes for each phone and its model type. The secret menu will basically unlock the phone/SIM. To follow this methodology, the simple steps are listed below:
Step 1. There are several sites like cellphonehacks.com where you can find a hack code for your device. Simply feed in the model details of your smartphone and gain access to its hacking code.
Step 2. The secret code that you received must be applied to a phone that has an active cellular network and whose number must be cloned.
Step 3: You will be redirected to a secret menu where the electronic serial number will be displayed in front of you. Note this code down and move on by exiting the menu.
How to prevent such cases
Duplicates of SIM cards are issued daily, however, the owner of the number is not always the recipient. To prevent such cases of SIM card fraud, you should:
- use only numbers that are registered to you personally. This makes it possible to contact the operator as soon as possible to solve the problem. It is better not to resort to using anonymous SIM cards;
- try not to link all your accounts or bank cards to one number;
- have a separate SIM card for working with Internet banking and mobile banking. If possible, it is recommended to obtain a foreign registered number (as experts advise on forums), which will almost completely protect you from cases of a duplicate. It is better not to “share” this number with anyone - not even to tell your close friends;
- use a separate SIM card for online banking on a separate phone (preferably the simplest push-button one). On the simplest phone, you physically cannot “catch” a virus that intercepts SMS messages and can itself send commands to transfer money when the SMS banking service is active. That is why it is categorically not recommended to access online banking on a smartphone whose number is linked to the card via a browser or even a mobile application (although working with the latter is much safer);
- if you use a smartphone, make sure that there are no unnecessary applications installed on it. Be sure to install an antivirus. All applications must be installed only using links from trusted sources (the application repository, for example, on GooglePlay, contains many infected programs that may have links from unscrupulous sources). In addition, using email or a browser can also lead to negative consequences (the same phishing), which are described above. It is better to disable geolocation and other services on it;
- do not give your phone or SIM card to other people for use;
- Ask bank employees about alternative payment confirmation methods. This could be an e-token smart card that generates one-time passwords, crypto calculators and other methods;
- Ask your mobile operator about the possibility of prohibiting actions with your SIM card by proxy. This service is offered by several Russian operators, including Megafon, Tele2, Beeline;
- do not set simple passwords on your accounts and change them at least once a year. And in order not to write them down in your phone’s address book (so as not to forget), use special programs like KeePass, which store passwords in encrypted form.
Part 3: How to intercept a mobile phone using Spyzie?
Spyzie is the most reliable smartphone spy tool to intercept iPhone/Android easily. It can monitor all activities on other people's Android/iPhone remotely and you don't even have to root/jailbreak the device to download/use Spy tool on it.
Spyzie has a three-step procedure, which includes creating an account > Activating Spyzie on the target device > Run device capture.
Spyzie can monitor call logs, SMS, Facebook, WhatsApp, Instagram, browser activity, GPS location, and other social media activities on a smartphone. Its keylogger feature can also save keystrokes on the target device to intercept its passwords/secret codes etc.
To enable Spyzie without letting the target Android/iPhone user know about it, follow the simple steps given below:
Let's start by making a recording with Spyzie by visiting the official website at https://www.spyzie.com/ and clicking on the "Register" button.
Next, you will have to feed in the basic data about the target Android/iPhone, which must be intercepted and tracked. As you can see in the screenshot below, installing Spyzie is easy. Once you're done, the Spyzie server will send you an email with instructions on how to use your Dashboard.
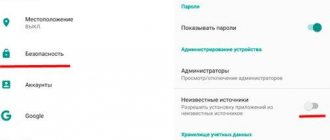
If the target device is Android, visit its Settings>Lock Screen & Security>Unknown Sources>Ok on the target Android device so that Spyzie App can be downloaded on it easily.
How to duplicate
There are several options that allow you to clone your SIM card. And here it is worth noting that some operators actively use this technology, which makes it possible to provide subscribers with SIM card duplication as an additional service. Several types of services are provided for users, both for using an additional SIM card for the Internet and for receiving all services.
However, Russian operators do not provide this opportunity to subscribers, despite world practice. And here it’s not even a question of price, since MegaFon, MTS, and Beeline don’t even offer to buy a duplicate SIM card. Therefore, the subscriber performs all actions related to cloning a SIM card at his own peril and risk.
Please note that not every SIM card can be duplicated. The simplest thing is to get a duplicate from an old SIM card that was released several years ago. It is worth considering here that such SIMs do not support the latest communication standards and do not allow the use of them.
To obtain a duplicate SIM card, you will need to extract information about the number (IMSI) and the encryption key from it. Not all SIM cards can provide this information. However, if you do not have the newest SIM card, then you can safely try to clone it.
Making a duplicate SIM card does not imply liability to the operator, since the subscriber pays for all communication services even from a clone. However, they can disable the copied SIM card if it is misused.
Here you need to pay attention to why, for example, you need an MTS duplicate SIM card? You can duplicate an MTS SIM card either on a separate SIM or on a multi-SIM. The latter allows you to record data about several numbers on it
In any case, you will need a SIM card duplicator, which is also called a programmer or reader. It comes complete with software that is required to install on your computer
When buying a SIM card duplicator, you should pay attention to what operating systems its software supports.
You will also need a blank SIM card on which a duplicate SIM card of MTS, Beeline, MegaFon will be written, and you can buy it in Yaroslavl and Moscow without a passport. When choosing, you need to consider the type of card, since they differ in built-in memory. This determines how many numbers can be recorded on it, and how many messages and contacts can be stored in its memory. Also, most pure SIMs have a mini and micro format, but to get a nano it will also have to be trimmed.
An important question is how much does such a duplicate MegaFon or Beeline SIM card cost? And here it all depends on where the programmer is purchased. You can order it on Ali for 150-200 rubles, but here they sell from 600 rubles.
Before you start copying, be sure to disable the PIN code request on the original SIM card. After that, you need to install it in the programmer and connect it to the computer on which its software is installed.
By launching the program, the SIM card is scanned. Her data will be saved in a special file. After the card has been copied, you can begin recording its data onto a blank one. To do this, you need to install a blank card in the reader and start writing the original data to it.
After the data is written to it, you need to install a new card into the device, connect it to the computer, and use the program to complete the cloning process. After rebooting the device, you can use a clone of the SIM card.
How license plates are stolen in Russia
There is no Authorized SIM Porting service in the Russian Federation, but SIM cards are still stolen en masse. Fraudsters draw up “fake” powers of attorney and contact communication shops.
Here's the diagram:
1. Data is found in the public domain or purchased online.
2. Download the power of attorney template on the Internet or on the operator’s website.
3. Enter the data into the template. Such a power of attorney does not need to be certified by a notary - operators draw them up themselves. The document is valid for up to 5 years.
4. Salons issue duplicate SIM cards by proxy or restore allegedly lost SIM cards. This allows you to receive an authorization code when intercepting access to mobile banking, e-mail and other accounts.
Let's face it, quite a lot of people might know your full name, address, birthday, even your mother's maiden name or the name of your first pet. This list includes your classmates and classmates, neighbors, acquaintances, colleagues, just random people who dealt with your documents.
Finding passport details is also easy. Scans of documents are often sent by mail or instant messenger. There are also hackers who work targeted or using purchased databases.
Human error is most often to blame for SIM card theft, or hijacking (and operators regularly admit this). Some people are too lazy to carefully check the power of attorney.
Couriers who bring a duplicate SIM card home want to quickly receive money and go to the next application. It is almost impossible to prove personal responsibility and blame the theft of money from an account on an employee of the operating company .
[edit] Dangers
If you entrust the cloning process to a technician you barely know from the radio market, there is no guarantee that he will not make another copy of the SIM card for himself and then make calls at someone else’s expense. It is best to do such an important task yourself, by purchasing a programmer, or with the help of people you can completely trust.
Sometimes cloning can be considered unauthorized interference with automated systems, computer networks or telecommunications networks and may result in criminal prosecution.
An incident from the life of an American: $100 thousand was stolen through a SIM card.
The theft of a SIM card cost crypto startup engineer Sean Koons $100,000 . The scammers stole his number and took all the money from his account balance on the Coinbase cryptocurrency exchange. Sean called it "the most expensive lesson of my life."
To warn other users, Sean told how it all happened. He had an email account linked to Coinbase and possibly other services.
To restore access to e-mail, he used the number of the SIM card installed in the smartphone. The address was protected by two-factor authentication (2FA) linked to the same smartphone.
In the US, operators provide the Authorized SIM Porting . It allows you to transfer your number to another device: for example, if you bought a new smartphone, changed the network, etc.
Authorized SIM Porting binds a SIM card to a new device. The scammers took advantage of this.
The attackers collected all available information about Sean on the Internet. They used this data when ordering the Authorized SIM Porting service.
The operator decided that there was enough information and linked the SIM card to the new device. Then the scammers initiated recovery of the email password and successfully received the access code on their smartphone. And then they intercepted access to your Coinbase account.
However, this is not the largest amount that was lost due to the theft of a SIM card. Thus, American entrepreneur Michael Turpin had his license plate stolen several times. And even after enabling enhanced security measures and the operator’s VIP status, he lost $23 million !