Many users install this or that software from third-party sources, which can, in theory, harm the computer. Unfortunately, modern antivirus programs cannot immediately identify some malware.
But you shouldn’t risk running potentially dangerous software on your computer without any protection. In this case, Sandboxie provides the ability to launch programs in a special environment where you can monitor how the launched program will behave.
You may be interested in: How to use Unlocker How to use BlueStacks
Setting up Sandboxie
To configure the program, right-click on the sandbox name. After that, in the context menu, click on the “Sandbox Settings” item.
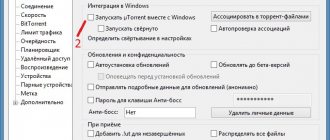
In the sandbox settings window - “DefaultBox”, in the “Behavior” section, you can check the box next to “Do not show the Sandboxie indicator in the window title” if you do not want the windows of programs open in the sandbox to be marked with a special icon. You can do this at your own discretion.
When you click on the yellow field in the “Color” window that opens, you can select a color to display a thin border around the window of the program running in the sandbox. After these settings, if you changed anything in the program settings, click on the “Apply” button.
In the "Recovery" section, in the "Quick Recovery" subsection, you can select folders for quick recovery if you want to change the program's default settings.
In the Immediate Recovery subsection, you can exclude files, folders, or file extension types from immediate recovery if these files are saved by a program running in the sandbox.
In the “Delete” section, in the “Deletion Suggestion” subsection, you can check the box “Never delete this sandbox or clear its contents” in order not to lose the data stored in the sandbox.
In the “Restrictions” section, in the “Internet Access” subsection, you can add programs to the list or remove programs from the list of programs that can access the Internet. You can allow or block programs from accessing the Internet when they are in a secure environment. If you click on the Block all programs button, then all programs running in the sandbox will be blocked from accessing the Internet.
In the "Applications" section, you can select rules of conduct for various programs running in the Sandboxie program.
In the “Sandbox” menu section, by clicking on the “Set storage folder” item, you can change the drive on which the sandboxes will be stored if you have little space on the “C” drive.
After clicking on the “Create a new sandbox” item, you can create an unlimited number of sandboxes, each with its own settings, to run programs with different behavior settings from your sandbox.
This mode of launching several sandboxes simultaneously, works only in the paid version of the program, after completing the trial period of working with the program.
Each virtual space operates separately, sandboxes are isolated from the system and from each other. By default, the application offers one isolated Sandbox DefaultBox space.
Windows Sandbox Settings
Once launched, Windows Sandbox is a clean system, without access to your files on the main system (which may be necessary), but with access to the network (which is a potential danger). If necessary, you can customize the behavior of Windows Sandbox using special configuration files, which are a regular XML text file with a .wsb extension. There may be several such files: depending on what parameters you need to start the sandbox with, launch the required file.
The contents of the file must start with and end with .
Among the available parameters that are specified inside these tags may be the following:
Disabling network access:
Disable
Disabling access to the virtual graphics adapter (the image will not disappear, but the graphics acceleration features will disappear):
Disable
Forwarding folders from the main system to the Windows sandbox (the ReadOnly parameter specifies read-only access; if False is specified, writing will also be possible):
Path_to_folder_in_system
True
The connected folders will be displayed on the desktop (it can also be accessed via the path C:\Users\WDAGUtilityAccount\Desktop\FolderName inside the sandbox).
Run the command when opening the sandbox:
any_command
All these parameters can be combined within a single .wsb configuration file, which can be created using any text editor, even the built-in Notepad (when using it, in the save dialog, in the File type field, select “All files” and when saving, specify the extension .wsb).
The screenshot below is an example of such a configuration file.
In this file, access to the network and GPU is disabled, two folders are connected from the main machine, and Explorer is launched upon login.
Additional nuances that may be useful:
- There is a clipboard running between the main system and the Windows sandbox, with which you can easily “pass” files to Sandbox without creating wsb configuration files.
- Each time you close the sandbox, all its contents are cleared. If you need to save your work, use shared folders.
- As noted above, the inability to enable the Windows sandbox (inactive in components) is due to virtualization being disabled or the processor not supporting it.
- Error 0x80070002 “The specified file cannot be found” when starting the sandbox can indicate various problems. First of all, at the final release this was encountered by owners of an OS in a language other than English, and Microsoft promises to fix it. Update: The bug has been fixed in update KB4512941. Self-fix (no longer relevant): install the English OS, and only then install the Russian language pack on it.
How to use Sandboxie
First way:
In order to run the program in safe mode, right-click on the name of the “sandbox” and in the context menu click on the “Run in sandbox” item. In the list of launch items, you can select the appropriate item to launch the program.
You can launch your browser, your default email client, and any program from here or from the Start menu. You can also launch Explorer in a safe environment if you click on “Launch Windows Explorer.”
After this, Explorer will be launched in a secure environment. To shut down Explorer, in the “Manage Sandboxie” window, right-click on the program folder and select “End Program” in the context menu, or simply close Explorer in the usual way for programs by clicking on the red button.
Second way:
It’s even easier to launch a program in Sandboxie by simply clicking on the program’s folder or shortcut, and then selecting “Run in Sandbox” from the context menu.
If you have created several sandboxes, Sandboxie will prompt you to select the desired sandbox to run the program. Select an isolated environment, and then click on the “OK” button.
After this, the program runs in an isolated environment. When you hover your mouse over a program running in a sandbox, a thin colored border will be visible around the program window.
Practical use
Let's try our tool on a real threat. So that no one would accuse me of fraud, I did a simple thing: I went to www.malwaredomainlist.com and downloaded the latest thing that appeared there at the time of writing. It turned out to be a nice pp.exe file from some infected site. The name alone inspires great hope, in addition, my antivirus immediately screamed at this file. By the way, it is better to carry out all our manipulations with the antivirus disabled, otherwise we risk blocking/deleting something from what we are researching. How to study the behavior of a binary? Simply right-click on this file and select Run BSA from the drop-down menu. The Buster Sandbox Analyzer window will open. Look carefully at the line Sandbox folder to check. All parameters must match those that we specified when setting up Sandboxie, that is, if the sandbox was named BSA, and the path to the folder was set to FileRootPath=C:\Sandbox\%SANDBOX%, then everything should be as in screenshot. If you know a lot about perversions and named the sandbox differently or configured the FileRootPath parameter to a different drive or folder, you need to change it accordingly. Otherwise, Buster Sandbox Analyzer will not know where to look for new files and changes in the registry.
Download a malware sample for analysis
BSA includes a lot of settings for analyzing and studying the process of binary execution, up to intercepting network packets. Feel free to click the Start Analysis button. The window will switch to analysis mode. If the sandbox selected for analysis for some reason contains the results of a previous study, the utility will offer to clear it first. Everything is ready to run the file under investigation.
Ready? Then right-click on the file you are studying and in the menu that opens, select “Run in sandbox”, then select the “sandbox” to which we attached the BSA.
Immediately after this, API calls will run in the analyzer window, which will be recorded in log files. Please note that Buster Sandbox Analyzer itself does not know when the analysis of the process will be completed; in fact, the signal for the end is your click on the Finish Analysis button. How do you know that the time has already come? There may be two options here.
- The Sandboxie window does not show any running processes. This means that the program has clearly terminated.
- For a long time, nothing new appears in the list of API calls or, conversely, the same thing is displayed in a cyclic sequence. At the same time, something else is running in the Sandboxie window. This happens if the program is configured for resident execution or is simply frozen. In this case, it must first be terminated manually by right-clicking on the corresponding sandbox in the Sandboxie window and selecting “End Programs.” By the way, when analyzing my pp.exe, exactly this situation occurred.
After this, you can safely select Finish Analysis in the Buster Sandbox Analyzer window.
Checklist for suspicious application behavior
Recovering files in Sandboxie
Sandboxie does not allow files from programs running in the sandbox to enter the operating system without your permission. All files created by the program or downloaded from the Internet will be deleted by default after the sandbox is closed.
Working in the Sandboxie program, you can create and save files in regular folders on your computer. These files will not be visible until you give Sandboxie permission to move the data from the sandboxed environment to the regular environment.
After you have downloaded some files from the Internet using a browser running in an isolated environment, these files will be located in the place where downloads are saved on your computer.
But, you will not see these files while they are in the sandbox. You will need to move these files from the sandboxed environment to the regular environment.
Sandboxie calls this "recovery" of files. There are three file recovery modes: Immediate Recovery, Quick Recovery and Manual Recovery.
How to decide when to run different Android application components in a separate process
Let's look at an example of Google Chrome browser that made the best use of the android:process attribute. Before that, let's understand why the architecture of multiprocessor systems was considered.
Remember those old days when we used a collaborative multitasking operating system. There was one process and applications used to run in that single process alternately. The problem with this architecture was that if one application was poorly managed, one process would languish, bringing the entire system down.
Now in modern days operating system, run applications in their own processes. If one application malfunctions, its startup process dies and does not affect the rest of the system.
The same applies to the browser. If one web page malfunctions, it will bring down the entire browser if web pages open in other tabs are not accessible. Consequently, a multi-process architecture was built.
Separate processes are used for browser tabs to protect the browser application from errors in the rendering engine. Each rendering process runs as an android service in a separate process. This is done using the android:process element tag. Another important flag used for the engine processing process is android: isolateProcess. This flag ensures that the rendering process does not have access to system resources such as the network, display, and file system, ensuring that the browser application is highly protected.
Here is a snippet of the chrome manifest file:
Here is the adb shell output:
USER PID PPID VSIZE RSS WCHAN PC NAME u0_a14 12926 317 694380 102828 ffffffff 00000000 S com.android.chrome u0_i16 26875 317 590860 59012 ffffffff 00000000 S com.android.chrome:s andboxed_process5 u0_i17 27004 317 577460 47644 ffffffff 00000000 S com.android.chrome: sandboxed_process6
The element in the manifest file also supports the android:process attribute to set a default value that applies to all components
By default, the application process name will be the package name specified in . This can be overridden by specifying the name in the android:process attribute of the tag. One use case: if multiple applications want to run in the same process, as long as those applications are signed by the same certificate and share a user ID.
If the name starts with : it becomes private to that application, as in the case of the chrome rendering engine ( com.android.chrome:sandboxed_process5 ). This implies applications, except that com.android.chrome cannot communicate with this rendering engine.
If the name begins with a lowercase character, it becomes a global process. From the docs:
This allows components in different applications to share the process, reducing resource usage.
Summary of benefits:
- Improve overall app stability (crashes/freezes). One service process crash does not crash all applications.
- Security by preventing access to the rest of the system.
- Reduce resource usage by running a component in-process and sharing it between different applications.
Basically you should be able to separate the issues and decide whether a multiprocessor architecture makes sense.
Update 1 : Adding comment from @Budius
Each process only has a certain amount of memory. In the application I'm working on, we perform computationally intensive processing on large arrays of memory. We always run these computes in a separate process to make sure we have enough memory for whatever happens and don't crash with OutOfMemory.
Immediate recovery in Sandboxie
This is the best recovery method as it can automatically call the recovery function as soon as the files are created. By default, the program pays especially close attention to the Downloads, Documents, Favorites, and Desktop folders.
You can add other folders to these folders at your discretion in the program settings (right-click on the sandbox folder => “Sandbox settings” => “Recovery”).
Once the file is saved to your computer, Sandboxie will immediately display the "Instant Recovery" window. You can click on the “Restore” button, and if you click on the “Restart” button, then “Restore and Explore” or “Restore and Run”.
Fast recovery in Sandboxie
With fast recovery, files are transferred from a sandboxed environment in a quick, manual process. You can configure the program to recover files saved in the sandbox when accessing this mode.
You may also be interested in:
- Toolwiz Time Freeze - freezing the system on your computer
- Windows 10 Sandbox: A secure, isolated environment
Manual recovery in Sandboxie
If you want to clear the sandbox, right-click on the sandbox name and select the “Delete Contents” context menu item. After this, the “Delete sandbox” window appears.
In this window, you can “Restore to the same folder”, “Recover to any folder” or “Add folder” for files located in the isolated environment. If you click on the “Delete sandbox” button, all processes in it are terminated and all its contents are deleted.
Using Sandboxie allows you to be more secure when using your computer. You can safely run some programs in an isolated environment, surf the Internet safely.
Some antivirus programs, such as 360 Total Security, also have sandboxing capabilities.
How to install on a computer
- Run the installation file SandboxieInstall64-533-3.exe .
2. Choose a language; there are a lot of them, there is even Ukrainian.
3. We accept the license.
4. Select the installation folder.
5. Next you will need to install an auxiliary driver.
6. The program is installed. Happy using!