Of course, everyone knows that the 21st century is the heyday of cybercrime, but not everyone understands that illegal actions in the virtual space are much more difficult to prevent and track. No matter how much you want, you cannot be sure that third parties will not receive your personal information in the near future.
If you are potentially not attractive to an attacker (having millions in bank accounts, access to a large customer database, etc.), then to protect personal information it is enough to have special software. It should be used on absolutely all devices that, one way or another, have access to the network. Smartphones are especially vulnerable, because very often you have to connect to unfamiliar WiFi points.
If your device is an Apple brand, then you should not worry about the safety of your privacy, because the iOS operating system already provides for everything. But when the device has Android on board, you should not neglect various antiviruses, VPN services and cleaners.
Unfortunately, by 2020, the Play Market has grown to unprecedented sizes, which makes it much more difficult to find one or another proven application. The material below will help solve this problem, because we have specially selected the 3 best applications of each type. If you want to learn how to pick up and, not to mention instructions and other essential materials for Android, welcome to the link above.
Although the main vulnerability is the user himself, antivirus applications will help increase the overall security of your system by about 30%. Periodic security checks and restrictions on downloading suspicious software will significantly complicate the penetration of malware into the memory of an Android device.
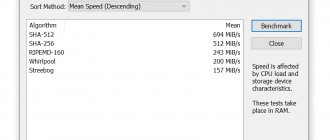
Top 3 best antiviruses for Android:
Kaspersky Internet Security is the undisputed leader of this list
Advantages:
- The best level of system protection compared to competitors.
- High speed.
- Availability of site checking functionality.
- Blocking unwanted content.
Flaws:
- Very high cost of the program.
- On weak devices, high system load may occur.
- The trial version cannot be used all the time; after the trial period, the Kaspersky Internet Security antivirus will stop working (after you try to turn it on, a window will simply appear asking you to pay for the tariff plan).
ESET Mobile Security & Antivirus – antivirus for everyone
Pros:
- Fast operating speed even on weak smartphones.
- Moderate cost of the annual tariff.
- Availability of USB control and built-in antispam.
- You can use the trial version as much as you like, and it’s really okay.
Flaws:
- The quality of threat recognition leaves much to be desired.
AVG Protection is a very good antivirus for the average user
Advantages:
- Quite large anti-virus databases.
- The ability to catch rootkits (a set of programs for collecting information and remotely controlling a device).
- High quality smartphone verification.
- Ability to check mail traffic.
Flaws:
- Crooked translation of the program into Russian.
- Noticeable system slowdown.
- Very inconvenient application interface.
The second most important application that every self-respecting user should have. Using a proven VPN service increases the overall security of the device by another 30%, because traffic encryption and protection against phishing sites seriously makes it difficult for attackers to obtain any information. Below we will look at just some of the different VPNs, but the average user will not find a better place to start.
Safety precautions when working with a computer
A computer is a complex device that operates under voltage, so it is also subject to electrical safety regulations. Applicable to your computer, follow these basic rules:
- Do not operate the computer if there is external damage to the case or the insulation of the power cables. In this case, it is necessary to replace the cables or contact a service center.
- Do not place or store various objects on the system unit case, especially heavy ones, because... Doing so may cause vibration, which may cause the computer to malfunction.
- It is not recommended to plug your computer into sockets without grounding. Sockets and plugs must be intact and without damage.
- Do not turn on your computer in a room with high humidity.
- Do not leave a running PC unattended for a long time.
- Computer wires and power cables should be positioned so that they cannot be stepped on or something heavy can be placed on them.
- You cannot work with a computer with the system unit case open.
By following safety precautions and recommendations, you will eliminate the risk of damage to your health and property.
Share.
More on the topic:
- How to properly format a flash drive on Windows and Mac If the flash drive starts to work unstable and some devices stop “seeing” it, it may be enough to format it to solve the problem. But it is important to understand that all the data […]
- The best programs for cleaning your computer and optimizing Windows Sometimes there comes a time when a brand new and flying Windows turns into a slow tractor that dulls over the simplest tasks and forces the user to […]
- How to install Windows on a computer An assembled desktop computer or laptop is not yet a full-fledged system with which you can work. For each such device, which has all the hardware components, it is necessary [...]
- How to install a driver on a computer A driver is software that allows components to interact correctly with a PC. It can be installed from a specialized disk, which usually comes […]
- How to enable WI-FI on a laptop A laptop is a mobile (or otherwise wearable) computer in which the ability to connect to a wireless WI-FI access point is a mandatory option, otherwise the whole point of mobility […]
Top 3 proven cleaners for Android
CCleaner is a reliable, time-tested utility, because downloads on the Play Market have exceeded 500 million.
Advantages:
- Improved overall performance.
- Analysis of installed applications.
- Removing unnecessary files and application cache.
- Scheduled cleaning and priority in technical support (but only in the PRO version of CCleaner).
Flaws:
- The cost of the PRO version is quite high.
- The device is heavily loaded.
Nox Cleaner is an interesting analogue of CCleaner.
Pros:
- Clear cache and temporary files.
- Relatively small application sizes.
- Search for duplicates and low-quality photos for subsequent removal.
- Doesn't boot the system.
Minuses:
- High cost of the tariff plan.
Android Assistant Pro is a powerful, multifunctional tool for optimizing and analyzing your Android device.
Advantages:
- Minimum application size.
- Very affordable price for the PRO tariff.
- Convenient battery status analysis.
- Friendly application interface.
Flaws:
- Very mediocre cache clearing.
As you can understand from the text above, antivirus and VPN are mandatory attributes of any security system, but they make up only 60% of it. The remaining 40% is the user’s awareness and attentiveness, because according to the author of the book “The Art of Deception,” Kevin Mitnick, 99% of cybercriminals (hackers), one way or another, use social engineering. Cleaners and assistants are like command centers for managing your system. You can do without them, because they do not protect the device specifically, but if comfort is important to you, then installation is also necessary.
Alex Leftin
Blogger, cybersecurity, technical reviews
Thanks for reading! Subscribe to my channel on Telegram and Yandex.Zen . Only there are the latest blog updates and news from the world of information technology.
Also, read me on social networks: Facebook , Twitter , VK , OK .
Launching main functions
Let's take a closer look at the main options in the Security program on Xiaomi. Advanced functionality will allow you to clean and secure the operating system as much as possible without resorting to the help of third-party applications.
Cleaning
Click on the “Cleaning” . The search for unnecessary data that takes up space on the phone will immediately begin. The size of the garbage and its type (data files, packages, memory, remaining data, cache) will be displayed. To remove this from your smartphone, click on the orange “Clear” . In Settings, you can enable a cleaning reminder that will run on a schedule.
Antivirus
Android devices are less susceptible to viruses than Windows, but they still need to be checked regularly. To do this, click on the “Antivirus” and wait for the application to scan payment security, general security and the presence of viruses. Optionally, you can select a signature, allow applications to be scanned before installation, and automatic antivirus updates.
Power and Performance
This section allows you to diagnose the battery life of your smartphone. To find out which parameters affect the battery, click “Optimize”. After checking, the application will show current problems and offer to fix them. For example, you can turn off haptic feedback, lock your smartphone after 15 seconds of inactivity, not activate the display when receiving notifications, etc.
If you want to increase operating time by disabling some functions, move the slider to the enabled mode opposite “Battery saver”.
Another useful feature is the power timer . You can configure your smartphone to automatically turn off and on according to a schedule. We activate the options and set the time, as well as the repetition: once, daily, on weekdays or on certain days.
Acceleration
Here you can speed up your phone by clearing the RAM. MIUI Security detects running applications (pinned, third-party and system), and closes them if necessary. Thus, the smartphone begins to function faster.
Applications
The section is intended for managing applications . You can delete some or clone them, and also check the permissions. By clicking on a specific application, you will see its size, traffic and battery consumption.
Deep cleaning
The tab displays all the materials stored on the phone: photos, applications, videos, installation packages and large files. You can carefully review the data and delete unnecessary data. The tool tells you what to remove. For example, duplicate photos, applications that have not been used for a long time, screenshots.
Respect for the post! Thanks for the work!
Want more posts? Find out technology news? Read reviews of gadgets? For all this, as well as for promoting the site, purchasing a new design and paying for hosting, I need help from you, loyal and grateful readers. Read more about donations on the special page .
It is possible to become a patron to support the blog with a monthly donation, or use Yandex.Money , WebMoney , QIWI or PayPal :
Thank you in advance! All funds raised will be used for the development of the site. Project support is a gift to the site owner.
Security App Guide: Part 1 - Permissions
We think there is no need to explain to anyone why it is so important to monitor the security of your smartphone and the cleanliness of its operating system. If you do not do this, then after a while the smartphone will slow down or even fail due to malware. Users of other OSes often install a lot of “cleaning” programs and antiviruses, but this is not necessary in MIUI. MIUI has its own feature-rich app that helps keep your OS clean and secure.
To configure and prevent threats, go to the “Security” application and study it.
Permissions
Click on the “Permissions” button on the main screen of the application and a menu will open. In it, select “Autorun”.
In the Autorun menu, check the box for applications with priority launch. Some applications may not work correctly in the background without autorun. You can add the necessary applications manually to the startup list. Just check the boxes next to the applications you need. This helps, for example, when notifications from VKontakte do not arrive.
Next, go to “Permissions”.
All apps ask for permission to access your data and features. You can manually select what type of data the application has access to. Scroll to the app you want and select the type of data you want to change access to.
To avoid manually setting up location access for each app, for example, you can swipe to the right and see a list of data types. In our case, only four applications request access to the location. Then, as in the first case, click on each application and choose to allow it access to data, block it, or force it to ask.
Products that may interest you:
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-13%
Fitness bracelet Xiaomi Mi Band 4 (black) (XMSH07HM)
2190 1,890 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-3%
DVR 70mai Dash Cam Pro EU (1944p, black) (MidriveD02)
5390 5 190 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-8%
Xiaomi Mijia Sweeping Robot 1S (white) (SDJQR03RR)
22290 20 290 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-9%
Xiaomi Mijia 1C Robot Vacuum Cleaner Sweeping Vacuum Cleaner (white) (STYTJ01ZHM)
18690 16,990 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-6%
New!
Fitness bracelet Xiaomi Mi Band 5 (black)
2890 2,690 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-18%
Xiaomi JIMMY Handheld Wireless Powerful Vacuum Cleaner (JV51)
12990 10 590 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-12%
Xiaomi Mi Air Purifier 2S (AC-M4-AA) (white)
11890 10 390 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-15%
Smartphone Xiaomi Redmi Note 8 Pro 6/128 Gb (Global, black/Mineral Grey) (M1906G7G)
22490 18,990 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-23%
Xiaomi Mi Robot Vacuum robot vacuum cleaner (white) (SDJQR01RR)
22990 17 490 rub.
Item in cart
Global Version
Global Version means that the product is released for the global market and meets international quality standards.
Rostest is a certification mark that guarantees that the device complies with all Russian norms and standards for environmental protection and user health. This sign does not imply any additional differences or advantages over other devices.
-15%
Smartphone Xiaomi Redmi Note 8 Pro 6/128 Gb (Global, green/Forest Green) (M1906G7G)
22490 18,990 rub.
Item in cart
Or are they not completely protected?
In January 2020, the Bitdefender company (specializing in the fight against viruses and other malicious code, known for its program of the same name) discovered 17 applications on Google Play that downloaded advertisements from the Internet. All of these applications behaved completely predictably immediately after installation - they performed their stated functions. Games, wallpapers, file managers, QR code readers, clocks. The cunning application behaved for about two days without arousing suspicion, and then it began downloading from the Internet and showing advertisements to smartphone owners - not only pictures, but also videos.
The applications confused the tracks and made it difficult to “catch” them. For example, a program could remove its icon and make the gaps between advertising banners random. It became difficult for the owner of a smartphone to see some kind of system in this and connect the outrages with the recent installation of “this cute game.” The total number of downloads of such applications was about 550 thousand. Experts reported the “find” to Google, and the company removed the applications from Google Play. (See also Daily Mail article about this incident.)
The CyberNews team, in turn, became interested in applications that allow users to “improve” their selfies: take a regular photo, and the application adds volume to your hair, whitens your teeth and gives the amazing blue tint to your eyes that you have always dreamed of. According to CyberNews, even the leaders in this class are not above collecting user data and sending it back to China for sale.
In October 2020, the online publication The Bell published an interesting study: only 11 of the 100 most popular applications on Russian Google Play do not share collected user data with anyone. Others send this data through numerous channels, including unencrypted ones (read: in clear text). The apps are loaded with trackers that monitor user activity (such as location) and require a fair amount of permissions. The Bell's publication illustrates the appetites of Android applications, which can lead to an invasion of user privacy.
It's hard to imagine a simpler and less demanding application than a flashlight. Avast, a well-known antivirus manufacturer, analyzed 937 (!) flashlight applications that were published on Google Play at different times. It turned out that 262 such applications required more than 50 permissions. In particular, for some reason 180 flashlights needed access to the contact list on a smartphone, and 77 flashlights wanted to record sound.
Does a flashlight really need access to contacts, location and files on a smartphone? Screenshot from Google Play.
Finally, the Android device and its owner can become victims of malicious code outside of Google Play. This story can be found in Group-IB’s material about the Android Trojan Fanta. This malware targets customers of the popular Russian online store Avito. The application steals money using social engineering techniques and phishing pages. In fact, the user himself gives Fanta access to his device.
So, sharing user data or asking for permissions is evil? Not necessary. Information may be transferred in anonymized form, and permissions may be necessary for the operation of the application. Each case should be considered individually.
Is it true that the lion's share of attacks come from holes in authentication mechanisms?
According to Positive Technologies statistics, the most common web application vulnerabilities in 2020 are related to incorrect security settings. But sites with weak authentication are at highest risk. This problem was found in 45% of the web applications studied:
Almost a third of these vulnerabilities are caused by an unlimited number of attempts to log into an account. Password-only authentication is the factor that contributes to the greatest number of brute-force attacks using login/password combinations. Password age and complexity requirements, which used to be the gold standard, now undermine security. According to NIST recommendations, organizations should switch to multi-factor authentication if they have not already done so.
A critical element of service security is the user registration and authentication system. In most cases, you're better off not doing it from scratch, much less using a password as an authentication factor. It’s better to entrust this entire function to a third-party service, for example a popular social network or digital ecosystem.
Taras Ivashchenko, Head of Ozon Product Safety Group
3