Super AntiSpyware
One of the most effective solutions that eliminates not only Spyware, but also Trojans and worms.
- Using heuristic analysis, even potential threats that are not yet included in the database are detected.
- The application itself is updated several times a year, and virus signature definitions will have to be updated manually 2-3 times a month.
- You can scan both the entire system and its components: RAM, disks, system folders.
- The software is characterized by minimal resource consumption and fast verification, which is suitable for a computer with weak hardware.
Download
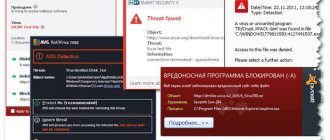
What malicious actions do Trojan programs perform?
Trojans are network monsters. Infection occurs using a flash drive or other computer device. The main malicious actions of Trojan programs are penetration into the owner’s PC, downloading his personal data to his computer, copying files, stealing valuable information, monitoring actions on an open resource. The information obtained is not used in favor of the victim. The most dangerous type of action is complete control over someone else’s computer system with the function of administering an infected PC. Fraudsters quietly carry out certain operations on behalf of the victim.
- Yeast dough for pies in the oven: recipes
- Prevention of osteochondrosis - office exercises for the back, video
- Reducing the size of the mammary glands through surgery, diet and visually
Antispyware Spyware Terminator
One of the first programs of its kind, which was an impeccable leader in the fight against spyware until competitors appeared.
- This is a comprehensive solution that is a full-fledged antivirus;
- A “Deep Scan” mode is available, which finds all known threats;
- Works in real time to provide the maximum level of protection. But for less resource consumption, you can disable online monitoring in the settings;
- The presence of the HIPS component allows you to close all security holes in the system so that potential threats cannot penetrate through them.
- Can detect not only spy scripts, but also ad viruses, Trojans, and keyboard scanners;
- Monitoring network traffic to detect suspicious activity of processes that may turn out to be disguised “enemies”;
- Warning when trying to access malicious sites;
- Extensive database of viruses in the integrated Clam AntiVirus utility.
Download
What is a Trojan horse
As is known from ancient Greek mythology, warriors hid in a wooden horse, which was given as a gift to the inhabitants of Troy. They opened the city gates at night and let their comrades in. After this the city fell. The malicious utility was named after the wooden horse that destroyed Troy. What is a Trojan virus? A program with this term was created by people to modify and destroy information located on a computer, as well as to use other people's resources for the purposes of an attacker.
Unlike other worms, which spread on their own, it is introduced by people. At its core, a Trojan horse is not a virus. Its action may not be harmful. A hacker often wants to break into someone else's computer just to obtain the necessary information. Trojans have earned a bad reputation due to their use in software installations to gain reintroduction into the system.
- Dopamine - what is it, the hormone of happiness. How to Increase Dopamine Levels
- Treatment of joints with the best non-steroidal anti-inflammatory drugs
- Caesar salad dressing recipe
Features of Trojan programs
A Trojan horse virus is a type of spyware. The main feature of Trojan programs is the disguised collection of confidential information and transfer to a third party. This includes bank card details, passwords for payment systems, passport data and other information. The Trojan virus does not spread over the network, does not destroy data, and does not cause fatal equipment failure. The algorithm of this virus utility is not like the actions of a street hooligan who destroys everything in his path. A Trojan is a saboteur sitting in ambush, waiting in the wings.
Windows Defender
My review of anti-spyware programs continues with a built-in utility from Microsoft. In new versions of Windows, it is enabled by default, but it clearly does not make itself felt until a danger is detected.
- Quickly finds malicious scripts that slow down the system;
- Fights ad viruses in browsers;
- Backs up all changes made so that you can rollback them later;
- There is a task scheduler that will help automate the scanning process;
- Works in the background without attracting the user's attention;
- The databases are updated almost daily.
How to protect yourself from Trojans getting onto your computer
Trojans can mainly get onto a computer via the Internet. In rare cases, this happens through external storage media. Most often, it is the user himself who is to blame for infecting the PC with viruses. It may even lead to a complete reinstallation of the system with the loss of important documents.
Setting a password on a flash drive
To avoid such problems, you need to follow simple rules:
- Do not open suspicious sites/emails that talk about winning something valuable. Letters demanding payment for something.
- Use antiviruses from Russian companies, for example, such as: Kaspersky and Doctor Web (but they will work in full force only if a license is purchased , then the antivirus will be able to fully protect the computer). Since Western companies do not deal with Trojans that do not appear on their territory. Most often, when a PC is infected with a new virus or Trojan, defenders simply mistake the virus for a regular, non-malicious file, because it is not in the database.
- Make backup copies to removable media. Configure periodic creation checkpoints . Thanks to this, it will be possible to roll back the system to a point when the computer is not yet infected. And you can restore files even after reinstalling the OS.
Anti-Trojan Emsisoft Anti-Malware
The software is free for home use, but you will have to pay for a business license.
- In addition to the typical anti-spyware capabilities, the utility can analyze the behavior of suspicious processes and block them if necessary;
- Excellent fight against key loggers that record all keystrokes to calculate logins and passwords;
- Detects and quarantines Trojans and worms. That is, it works as a full-fledged antivirus;
- It is possible to control startup (disabling dangerous processes and services that load along with the system).
You can find out what other useful advantages this software has after downloading and installing.
Download
Ad-Aware
Can do everything that was listed in the description of previous applications. But there are also unique features that make the software one of the best in the world. This is a powerful solution that is completely free. It guarantees comprehensive security for the entire system and important user information.
- Capable of blocking location tracking systems that may be automatically activated when visiting sites;
- Blocks aggressive advertising by thoroughly scanning the registry and disabling harmful browser add-ons;
- Self-updating of databases, which does not require any action from you;
- Connecting plugins to modernize functionality. You can add extensions at your discretion. But remember that each of them will consume additional system resources;
- Antivirus running on the effective Bitdefender engine;
- A scanner for malicious sites that will prevent you from visiting dangerous resources;
- Built-in game optimizer;
- Download manager with preliminary checking of downloaded files.
The software base is updated daily automatically. You don't need to do anything, the application will do all the work for you.
Malicious scripts will not get onto your computer thanks to online scanning and heuristic analysis. As soon as the software notices suspicious behavior, it will immediately block the dangerous process.
Download
Trojan removal programs
Antivirus programs cope with all types of malicious threats. But if you only need to remove the Trojan, you can use a special utility designed specifically for these purposes.
Removal using Trojan Remover
This utility is designed to remove and protect your PC from Trojan threats that a regular antivirus cannot recognize. It has an expanded database of viruses from the trojan category. The “treatment” procedure is as follows:
- Install and run Trojan Remover.
- Click on the “ Update ” button.
- Select the item “ Full Database update ”.
- Click on the “ Update ” button.
- We are waiting to be updated .
- the update was successful appears .
- Then close the window .
- Click " Scan ". The program will check the system for Trojans and deactivate them.
- We close the window.
- Go to “ File ”, then “ Scan a Drive/Directory ”.
- Select the required drive or folder to scan and check the boxes.
- In the “ Action ” line, select the name “ Automatically rename malware files ”.
- Click “ Start Scan ”.
If malicious Trojans are detected, you will be prompted to remove them.
What to do if the browser itself opens with advertising
SUPERAntiSpyware
A program for searching, protecting and removing unwanted software. To get rid of a Trojan on your computer, you should follow these instructions:
- Install and run SUPERAntiSpyware.
- Click “ Scan this computer ”.
- Select “ Complete Scan ”.
- We wait while the program scans the computer .
- After scanning is complete, click “ Continue ”.
- Click “ Continue ”.
- If a browser is open on the computer at this moment, the program will ask you to close it .
- Click “ Continue ”.
- Click “ Continue ” again.
Spyware Terminator!
A free utility that helps find and protect against Trojans and viruses. We adhere to the following algorithm:
- Install and launch Spyware Terminator.
- Go to the “ Scanning ” section - select “ Full Scan ”.
- We wait until the scanning finishes .
- If the program finds malware, then click “ Delete ”.
- the browser is open at this moment , then it must be closed.
Kaspersky TDSSKiller
A small free utility from Kaspersky Lab, designed to search for and combat malware such as TDSS, Rootkit. SST. “Treatment” proceeds as follows:
- Download and install antivirus software. Once the installation is complete, TDSSKiller will automatically open.
- Click the “ Start scan ” button.
- If Trojans or third-party malware are detected, click “ Delete ”.
Malwarebytes Anti-Malware FREE
A program for searching and eliminating malicious files. After updating to the third version of the utility, it was renamed from Malwarebytes Anti-Malware FREE to Malwarebytes 3. The procedure is as follows:
- Launch Malwarebytes.
- Go to the “ Verification ” section.
- Select “ Full scan ”, click “ Start scan ”.
- When the program finishes scanning, click “ Quarantine selected objects .”
- If you want to delete files from quarantine, then go to “ Quarantine ”, select the files that you want to restore or delete, and click the appropriate buttons.
RKill to stop processes
The program stops processes launched by the Trojan and makes it possible to open the antivirus to “cure” the PC:
- Let's launch RKill.
- When the program finishes stopping the malware processes, a window will pop up where you need to click “ OK ”.
- A text document will open with the results of stopping the processes.
- Check your computer with an antivirus for malicious threats.
Unlocking your phone's pattern key
Note ! The utility does not remove viruses, but only stops malicious processes. After rebooting the PC they will be launched again.
HitmanPro
An effective program for fighting and removing Trojans from a Windows 7, 8, 10 computer. It uses Emsisoft, G Data and Dr.Web databases. For treatment you need to adhere to the following algorithm:
- Open HitmanPro.
- Click “ Next ”.
- We choose what to do with the malicious files (delete or quarantine) and click “ Next ”.
- Next, click “ Exit ”.
RogueKiller for cleaning the registry
After running this utility, malicious processes stop their activity. This allows you to effectively remove them from the system:
- Let's launch RogueKiller.
- Go to “ Scan ” and select “ Standard Scan ”.
- Click “ Results ”.
- We repeat the action.
- Select “ Removal ”.
- Next is “ Results ”.
- Click “ Finish ”.
- And we repeat the action.
AVZ
Very serious software that not all beginners can handle. In fact, the 2020 versions are much simpler than earlier releases of this software. I remember a couple of years ago I had to deal with AVZ to eliminate a Trojan. It immediately seemed that the utility was extremely complicated. But then I figured it out and used it several times. Cool stuff.
Very often people leave reviews on antivirus forms and ask to post scan logs made by this program. And then they offer a solution in the form of a script that should be executed in AVZ. That is, in order to solve a specific problem, find and remove a dangerous virus that other “defenders” cannot cope with, it is enough to find the necessary code on the Internet and paste it into the execution window.
- Detects all known Dialer Trojans;
- Copes with email and Internet worms without any problems;
- Finds and eliminates the following types of viruses: Trojan Spy, Trojan Dropper, Trojan Downloader;
- Consists of several routines that perform analysis of the registry area, file system and memory;
- Contains more than 10,000 trusted system elements in the database that will not be affected during the scan;
- High-quality detector of key loggers that collect data from the keyboard;
- Cleaning boot records from malicious scripts (Boot Cleaner utility);
- Thorough analysis of all running processes and services.
Download
Each option has its own advantages. I told you about the best anti-spyware programs for Windows in 2020, and the choice is yours!