Vim
A good text editor is one of the main tools of a system administrator, since in many situations it is necessary to make changes to configuration files and it is important to do this very quickly. The Vim editor recently turned 25 years old and is still very much in development.
It compares favorably with all other editors in that it allows you to edit text and move around it very quickly, without taking your fingers off the main keyboard. To do this, the editor has two modes - command mode, with which you can navigate through the text using letter keys, as well as execute various commands. The second mode is editing, in which the program turns into a regular editor.
In November, the eighth version of Vim was released, in which the program received many improvements. For example, GTK3 support and asynchronous I/O for plugins. This editor can work not only on Linux, but also on Windows and MacOS.
Htop
Monitoring the load on the operating system is also a very important task that system administrators face quite often. For example, if you urgently need to find out which program is overloading the processor or taking up all available RAM. The htop utility shows a real-time list of all running processes with the ability to sort by the desired parameter, processor usage, and memory.
In addition, using the utility you can see the number of threads of the processor core on which the program is running and much more. This is one of the most important utilities in the list of system administrator programs. The program only works on Linux systems.
SSH client
The first place in the list of system administrator programs is occupied by the ssh client. It is in ssh that I spend most of my working time. I work with Linux much more than with Windows. During my work, I tried everything that came across the ssh client topic. Like most people, I started with putty , then used kitty . This option is suitable for those who need to occasionally connect somewhere via ssh. Also for those who have 5-10 servers in their care with one password or certificate for all servers.
As soon as the number of servers grows, the question arises of finding a more convenient program for ssh connections. I end up using two programs, which I’ll tell you about in more detail.
mRemoteNG
I became familiar with this program a long time ago, even before it was forked and NG was added at the end. It combines all the popular methods of remotely connecting to servers. Specifically I used the following:
- ssh
- rdp
- vnc
It is very convenient to connect to different servers from one place. All connections are located in one program window in separate tabs. I was satisfied with almost everything in this program, except for one annoying bug that has not yet been fixed. If you connect via ssh, then switching using alt+tab does not work correctly. If you switch from mRemoteNG to another window using alt-tab, and then return back using the same combination, you will end up not in mRemoteNG, but in another program.
This behavior is due to the fact that putty is used for ssh connection; the program itself is written in .net. This combination somehow does not work correctly in terms of switching windows. I read reviews about this bug on the developers' website, all the details are there. They write that until they move away from putty, it is impossible to fix this bug. It’s a pity, since I’m 100% satisfied with the program, but the eternal problems with alt+tab still forced me to look for a replacement for ssh. And I found it, and I use mRemoteNG for rdp and vnc connections.
This program has a ported version and is easily synchronized via cloud file storage, which adds to its advantages. One of the downsides is the use of putty, in which I personally really don’t like the fact that it uses its own private key format. You have to use puttygen to convert keys.
This program became indispensable for me when the number of managed servers exceeded 30-40. With its help, you can build a tree structure of attachments for connections and save credentials. And all this in one place for all protocols. mRemoteNG is an excellent program for a system administrator. I have never seen better functionality. Maybe someday the shortcomings will be corrected.
The downside, as I already said, is incorrect alt+tab switching when working with ssh and the lack of a startup password. This is important, since all your passwords are stored in the program, and it is also ported. As a result, I removed all ssh connections from it and started using another program.
Xshell 5
This ssh client for Windows suits me perfectly. It has a lot of settings, after installation I spent a long time figuring them out to make everything beautiful and convenient. Here's an example of why I love this client.
You can arrange windows, for example, like this and debug something. If you have multiple monitors, like I do, you can place different instances of the program with different connections on different monitors. For example, I like to test the load on a web server this way. On one monitor I open ssh windows with the necessary metrics, on the other I open graphs from zabbix. I give the load and see in real time what is happening on the server.
Xshell 5 gets rid of all the shortcomings of the previous program:
- Switches correctly using alt+tab.
- Has a password to start the program.
- Uses a standard private key format, unlike putty.
The interface is well customizable. I removed everything unnecessary from the program window. I remember the hotkeys and only use them to create connections, change, etc. Ssh connections can organize a tree structure and have a lot of settings. You can change the colors in the console, the colors of window titles, etc. This way you can conveniently mark the most important servers with a separate color, or test ones. I do this for some servers. You can separate servers from different organizations with different colors.
Regarding the Xshell ssh client, my verdict is this: I have never seen a better program for a system administrator. I use it all the time and recommend it to you. Moreover, it is free for home use. If you have any examples of more convenient and functional programs for organizing remote connections, please share them in the comments.
Git
Version control is very important not only in programming. For various scripts, configuration and plain text files, it can also be very useful to restore the previous version.
Git was originally developed by Linus Torvaldst to manage the development of the Linux kernel. But today it is a full-fledged platform, which is used by a very large number of open source projects. But it can also be useful in saving old versions of your configuration files.
The latest version at the moment is 2.10, which has many useful features. For example, using the git diff command you can find out exactly which lines and in which files were changed; the deleted lines will be crossed out. The program can be used on Windows and Linux.
Remote access programs
System administrators often need to connect to remote workstations. There are many programs to implement this functionality. The most popular and well-known is teamviewer. But it is paid, and the free version has limitations that often prevent its use. We have to look for compromises.
There is a good analogue - LiteManager . The free version has a limit of 30 seats. If you have fewer of them or you use the program to access some technical machines where rdp is not suitable for some reason (access control server, video surveillance client, etc.), then perhaps this program will be enough for you.
If you have more than 30 workstations and need remote access to all machines, then the solution is a vnc server. I prefer TightVNC . The solution is suitable only for a local network, or for a channel of at least 30-50 megabits. VNC has a very slow protocol and it is simply impossible to use it at low channel speeds.
If you need remote access via vnc to a local network, then you can use vpn, or a simpler option is to connect somewhere to the local network via rdp, and then via vnc. With modern Internet speeds, it turns out to be a completely working option. I use it in some situations. For security, I simply restrict access via rdp at the ip level. I have the ability to connect from several static IP addresses.
SystemRescueCD
Computers don't always work as they should and tend to break down. A great practice for system administrators is to have a CD or USB drive with a set of tools that will help restore the system or at least data from problem computers.
SystemRescueCD is an actively developing set of utilities for system administrators for all occasions. It is a bootable Linux distribution based on Gentoo that contains various tools for hardware testing, disk partitioning, data recovery, computer virus scanning, network configuration and much more.
Versions 2.8 and 2.9 were released in 2020. In these versions, the image received updates to various components, including the addition of support for tools for working with btrfs.
Clonezilla
Sometimes it is better not to restore the system from scratch, but to have a backup of the entire machine so that you can bring the system back to life in a few minutes. Clonezilla is the de facto standard for backing up and deploying system images to disk. You can create backups for individual partitions or for the entire disk.
The program can be used from the current system or as a boot image with a pseudo-graphical interface - Clonezilla Live. Once you have a copy ready, you can very easily recover from a failed configuration or update.
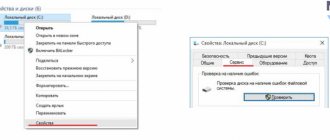
The latest version adds support for detecting volumes encrypted with Windows BitLocker, improves EFI support, and updates all software to the latest versions of Debian.
Docker
Containers are isolated environments that allow you to run multiple systems on a single Linux kernel. All systems are isolated from one another, as well as from the main system. The Docker container configuration tool has greatly contributed to the development of containers in 2020.
Docker is an open platform that allows you to literally deploy containers with the necessary Linux distributions and run the necessary software in them in just a few commands. With Docker, you can package a single application with all its dependencies, and then run it on any distribution that supports Docker.
You can create your own programs and share them with other users. Docker allows companies to choose the system on which the software will run, without limiting developers to tools and programming languages.
The latest versions of Docker have added the ability to check the state of the container and automatically recover in case of problems, and now Docker containers can run not only on Linux, but also on Windows.
Wireshark
Wireshark is a tool for analyzing traffic passing through a computer and saving network packets. This task may arise when analyzing the performance of a network, network services or web applications. The program supports a huge number of protocols and can even decrypt HTTPS traffic if a key is provided. You can filter all traffic according to the parameters you need, sort packets, view their contents and full information, and much more.
A new version of Wireshark 2.0 was released in 2020, and since then it has been actively developed in this thread. Its interface has been rewritten in Qt5 and made more intuitive.
Where should admins keep a to-do list?
I am absolutely convinced that any system administrator needs a program for maintaining to-do lists, of which he always has a huge number. In extreme cases, the program can be replaced by a text notepad. This is exactly how it was for me for a long time, until I met and tried the Todoist . Since then I have been doing all my business there.
It is important not to forget anything when working with customers. Everything that was discussed and planned with you, you write down and complete on time. If these are personal conversations, then I make notes in a notebook and then make sure to check if I have forgotten anything. If I don’t write it down, I’ll most likely forget. During the day there is a constant incoming flow of information that needs to be organized. Commitment and punctuality create a good impression and allow you to find and maintain long-term relationships with good customers.
How do you conduct your business?
TightVNC
TightVNC allows you to access a GUI on a remote computer. With this program you can control your computer remotely without actually being in front of it. Typically, administrators manage Linux servers via ssh, however, some users prefer to use a GUI to handle such tasks.
The program has the ability to encrypt VNC traffic, thus making it secure, just like ssh. TightVNC can run on both Linux and Windows. You can then access your device from anywhere there is internet.
My system administration programs
Batch files– Basic concepts about command files and examples of their use - creating files and generations of data archives organized by time, stopping and starting system services from the command line, using environment variables, executing commands on a schedule, etc.
Pstools package utilities
– Command line utilities from the PStools package from Sysinternals work in Windows NT, Windows 2000, Windows XP, Windows Server 2003 and do not require installation.
They allow you to not only manage a local computer, but also remote administration without installing any software on the remote computer.
Allows you to run applications on a remote system, manage services, reboot, shutdown or stop a local or remote computer, and much more.
Working with the Windows Registry
– information on the registry from many sources and personal experience is collected here. General information about the Windows registry, registry files and their locations, a brief description of registry keys and their purpose.
Much attention is paid to restoring system functionality, saving and restoring registry data. A separate section is devoted to tracking access to the registry using the RegMon utility. Issues with automatic startup of applications and services.
Brief description of the AutoRuns utility. Examples for restricting user access to system resources and ways to combat access restrictions. Some useful Windows settings through the registry.
Problems loading Windows 2000/XP.
– Information about the boot mechanism of Windows 2000/XP using the NTLDR loader is presented in a compressed form. The reasons why the system may not boot and ways to eliminate them are discussed.
A brief description of working with the Windows recovery console and Winternals ERD Commander.
BOOTMGR – Windows Vista/7 boot manager
– Description of the mechanism for loading Windows operating systems using the
BOOTMGR
, which replaced the outdated NTLDR boot loader in Windows Vista and later operating systems.
Description of the BCD (Boot Configyration Data) boot configuration store, its structure, objects and configuration elements. Examples of using the BCDEDIT editor and third-party boot configuration editing programs (EasyBCD).
Examples of violations of the operating system boot process and methods for restoring it.
Win2k control panel.
– What to do if the Windows Control Panel does not open. How to remove unnecessary Control Panel items.
Hidden Windows devices.
– how to get a list of hidden Windows devices and, if necessary, remove unnecessary ones.
File manager FAR
– A very functional and convenient program for a system administrator. In addition to the standard capabilities of a file manager, it can be used as an FTP client that can work through a proxy and firewall.
Allows you to view your network environment and network folders (including hidden ones). It has a built-in editor with the ability to view files in both text and HEX format. Moreover, in text format it is easy to change DOS encoding to Windows and vice versa.
The capabilities of the built-in editor make it easy to perform even such “exotic” operations as transferring the text selected in a rectangular window from a text file to another file, etc.
There is a program manager that allows you to view a list of processes, information about each of them, its source and the system resources used. And kill ANY process, which the standard Task Manager does not allow you to do.
Omniquad Instant Remote Control
– a program for remote administration of systems running Win2K/XP/Win2003, which does not require installation of the server component on the administered computer. Just run it, enter the IP address (computer name), username, password and the desktop of the remote system in front of you.
Automation using nncron Lite
– Setting up and using the nncron Lite task scheduler. Brief description of installation and configuration. Format of entries in the nncron.tab file. A simple example of creating a job to run an application periodically.
Examples for scheduled remote turning on of computers using Wake On Lan (WOL) technology, remote launch of applications using the psexec utility, and shutting down the computer at a specified time.
Free computer programs
– a brief description and links to sites for downloading free software for computers running Windows OS. Here is information about software products that I myself have personally used, and, as a rule, continue to use to this day.
The programs are grouped into categories - “System software”, “Internet and network”, “Security”, “Equipment monitoring and testing” and “Other”. The free programs section will be constantly updated.
Working in the Linux console
– Linux console for beginners. Basic knowledge of the command shell. How to shut down/restart your computer, view the list of processes and remove frozen ones, create a file or directory, install or remove an application, etc.
Remote work with a Linux graphical terminal
– how to connect from Windows to the Linux graphics subsystem using the free Xming package. Options using XDMCP and X11 Forwarding.
Free Oracle on free Linux
– installation of Oracle Database XE Server on Linux Mandriva 2007 Free.
Building a VPN based on Mandriva Linux 2007 and PoPToP.
An option for organizing the connection of remote Windows clients via the Internet to the enterprise local network using a VPN server based on Linux Mandriva 2007.
Unexplained problems with the computer.
– brief techniques for identifying and troubleshooting problems with computer equipment. What to do if the computer does not turn on, turns on spontaneously, freezes or reboots. Links to programs for collecting information about equipment and testing.
Zenmap
Zenmap is a graphical interface for the popular network scanner nmap. With this tool, you can very quickly find all nodes connected to the network, check the network topology, and also view a list of running services on each computer.
Also, using the program, you can find potentially dangerous places in server configuration; many administrators use it to check the availability of nodes or even measure uptime.
Filezilla
Our list of utilities for system administrators is coming to an end. When administering servers, you often have to transfer files. Typically this task is performed using FTP. Filezilla is one of the best and most popular clients for transferring and downloading files via FTP. The program interface is divided into two panels, in one of which you see the local computer, and in the other the remote file system of the FTP server.
The program's interface is intuitive and can be used on Windows, Linux and MacOS.
System administrator's first aid kit. A minimum set of utilities for the most effective problem solving
Every system administrator sometimes has to service the computers of friends or make home visits. A proven set of utilities helps him in this matter. Our review will only talk about free ones that do not require installation and have become the de facto standard.
Autoruns
This program became the calling card of Mark Russinovich and the company Winternals Software (better known by its website name - Sysinternals.com), long ago absorbed by Microsoft.
Now it is still developed by the author, but legally belongs to the technical department of Microsoft. The current version 13.3 was written in April 2020. With v.13.0, the program has not only become more convenient, it has received a number of new functions, in particular advanced filtering tools, integration with other system utilities and online services. Autoruns displays the most complete and most detailed list of autorun components, regardless of their type. The utility shows how to load all drivers, programs (including system ones) and their modules by registry key. It even lists all Windows Explorer extensions, toolbars, startup services, and many other items that other similar programs usually miss.
Color-coding helps you quickly identify, from a list of hundreds of entries, standard components that are digitally signed by Microsoft, suspicious files, and erroneous strings that reference non-existent files. To disable the ability to autorun any component, simply uncheck the box next to it on the left.
Ghosts of autorun objects in Autoruns are highlighted in yellow
Some components are automatically loaded only when you log in with a specific account. In Autoruns, you can select the entries that correspond to each account and view them separately.
The command line mode also deserves attention. It is extremely convenient for exporting a list of startup items to a text file, creating advanced reports and selective anti-virus scanning of all suspicious objects. You can read the full help on the website; here I will give an example of a typical command:
autorunsc -a blt -vrs -vt > C:\Autor.log Here `autorunsc` is a program module launched in command line mode. The `-a` switch specifies that the objects to be checked are listed after it. In the example there are three of them: b - boot execute (that is, everything that is loaded after the system starts and before the user logs in); l - logon, user-specific startup components and t - scheduled jobs. If instead of enumerating blt you specify asterisk (*), then all startup objects will be checked.
The `-vrs` and `-vt` switches indicate the mode of operation with the VirusTotal online service. The first set specifies sending only those files that do not have a Microsoft digital signature and that have not previously been verified. If at least one antivirus out of fifty considers the file to be malicious, a detailed report will open in a separate browser tab. The second set of keys is needed so that each time you do not open a tab with the user agreement for using the VirusTotal service and do not have to confirm your agreement with it.
An Autorunsc report is typically tens or hundreds of kilobytes in size. It is inconvenient to read it on the screen, so in the example the output is redirected to a log file. This is a plain text format in UCS-2 Little Endian encoding. Here is an example of a recording from it with one false positive:
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run Adobe ARM “C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe” Adobe Reader and Acrobat Manager Adobe Systems Incorporated 1.801.10.4720 c :\program files (x86)\common files\adobe\arm\1.0\adobearm.exe 11/20/2014 21:03 VT detection: 1/56 VT permalink: (link to VirusTotal report).
Two unsigned drivers turned out to be clean, and one signed driver had a VT reaction
You can download Autoruns on this page.
Process Explorer
The GUI version of Autoruns can work together with another utility from the same author, Process Explorer (PE).
If you first launch PE and then Autoruns, then in the latter’s menu additional items appear about viewing the properties of each active process from the autorun menu. In the PE settings, you can specify the desired way to display all active processes: a simple list sorted by name or CPU load, or a tree list with dependencies. An option is also set there that allows you to check unknown files (detected by hash) in VirusTotal. If you turn it on, after a while the test result will appear on the right. All objects that are attacked by at least one antivirus will be highlighted in red.
When clicked, the window is divided horizontally, and the lower part displays complete information about the selected process and its actions in the system. Clicking will bring up an additional window with indicators of CPU, GPU, RAM load, I/O intensity, storage and network usage. For each component, the total load and the most resource-intensive process are displayed. For GPUs, it even shows the percentage of occupied video memory and the load on each chip, if there are several of them. This is especially true now, since many (malware) programs actively use video cards for non-graphical computing. This behavior is especially typical for Trojan cryptocurrency miners.
The test Trojan does not look suspicious yet, and four antiviruses are already complaining about µTorrent
By right-clicking on any process from the PE list, a context menu appears. It duplicates all the functions of the built-in task manager and adds several new ones. In particular, with one click you can send a file corresponding to a suspicious process for analysis to VirusTotal, search for its description on the Internet, make a dump or suspend execution. A paused process stops responding to any commands (including internal ones), and it becomes easier to analyze. After you have dealt with it, you can send the “resume” command through Process Explorer. Of course, unless absolutely necessary, you shouldn’t do this with system processes and utilities that perform low-level operations. It is better not to interrupt BIOS/UEFI flashing, changing disk layout, partition alignment and other similar operations.
Usually the title of each window indicates the name of the application that generated it, but it happens that they remain nameless. This is especially true for Trojans that imitate well-known programs or small dialog boxes with error codes. Process Explorer has a handy “find process by window” feature. Just click this button on the top panel and, holding down the left mouse button, move the cursor to the area of the strange window. The corresponding process will be automatically highlighted in the PE table.
Test Trojan suspended via Process Explorer
To take advantage of all the features of Process Explorer, you will need to run it with administrator rights and (in some cases) install Debugging Tools for Windows. They can either be downloaded as part of the Windows Driver Kit. The latest version of Process Explorer can be downloaded from the Microsoft website.
Unlocker
Without a doubt, Mark Russinovich is a real guru among the authors of system utilities for Windows, but his programs were created as universal tools. Sometimes it is worth using more highly specialized tools. Such as the creation of the French programmer Cedric Collomb. Its tiny Unlocker utility can do only one thing: unlock a file system object occupied by some process in order to regain control over it. Although the latest version was released in 2013, the program still performs its functions better than all analogues. For example, it allows you to unload dynamic libraries from memory, delete the index.dat file, work with file names that are prohibited in Windows, and perform most actions without rebooting.
Some process is blocking Safari from uninstalling
Unloker identifies handles to running processes that are currently blocking work with the desired file or directory. This locking is required to prevent mutual influence of applications in a multitasking environment. When the OS and programs are functioning normally, it prevents accidental deletion of used files, but sometimes errors occur. As a result of one of them, the application may freeze or remain in memory after closing the window. The file system object can then remain locked long after it is no longer needed.
Today, the list of active processes for the average user starts from fifty, so it can take a long time to search for zombies among them. Unlocker helps you immediately determine which process is blocking modification or deletion of a selected file or directory. Even if he cannot figure this out due to Win32 API limitations, he will offer to force the desired action: rename, move or delete the object.
Unlocker did not find the reason for the blocking, but can delete the recalcitrant file
Sometimes several programs can access the same directory at once, so several handles are identified among the processes blocking it. Unlocker has the ability to unblock everyone with one button.
Starting from version 1.9.0, 64-bit versions of Windows are supported. The utility can be integrated into the Explorer context menu or run in graphical mode as a portable application. You can also install Unlocker Assistant. It will hang in the tray and automatically call Unlocker whenever the user tries to manipulate a locked file. Running with the `-h` switch will display help about the command line mode. The utility is available in forty languages, although there is nothing special to translate in it - everything is already intuitive.
AVZ
Looking at the list of capabilities of the AVZ utility, I would like to call it analytical, not anti-virus. Oleg Zaitsev's tiny program has many irreplaceable functions that make the everyday tasks of an administrator and the life of an advanced user easier. It will help you perform a system scan, restore lost settings of built-in OS components to default settings, detect any changes since the last audit, find potential security problems, remove Trojan components from SPI Winsock and restore Internet connectivity, identify strange program behavior and detect level rootkits kernels.
AVZ contains many system analysis tools
Known malware is best removed using other antivirus scanners. AVZ is useful for fighting unknown evil, finding holes through which it can leak, and eliminating the consequences of infection. In most cases, AVZ allows you to do without reinstalling the OS, even after a severe virus attack.
You can use AVZ as a portable application, but the full set of functions of the utility will be revealed only if you install AVZPM, its own kernel mode driver. It controls all modules, drivers and active applications, allowing you to easily identify masquerading processes and any technologies for substituting their identifiers.
AVZGuard is another kernel mode driver that can be activated from the AVZ menu. It restricts access to active processes, suppressing anti-virus activity on the infected computer. This approach allows you to launch any application (including another antivirus) from the AVZ window in protected mode.
One of the clever countermeasures of malware remains the method of blocking its files and recreating elements deleted by the antivirus the next time the OS is loaded. This can be partially done manually using Unlocker, but AVZ has its own technology - Boot Cleaner. This is another kernel mode driver that enhances Windows' built-in lazy uninstall on restart feature. It boots earlier, logs its results, and can delete registry entries as well as files.
The AVZ antivirus scanner itself also has a lot of know-how. It is able to scan alternative NTFS streams and speed up the scan by excluding files identified as safe by the Microsoft catalog or its own database. All threats can be searched by specific types - for example, immediately exclude the HackTool category. There are separate modules for searching for keyboard interceptors, ports opened by Trojan horses, and behavioral analysis. AVZ allows you to copy suspicious and deleted files to separate folders for their subsequent detailed study.
Creation of a detailed research protocol in AVZ
The requirement to send reports to AVZ and its “System Research” module has become standard practice in many virologist forums, where people turn to people for help in solving non-trivial problems.
Of course, an experienced administrator’s first aid kit may contain more than a dozen programs, but these four utilities will be enough to solve most problems. You can easily find the rest in the collections using the links provided in the article.
WWW
Complete archive of system utilities SysInternals - 73 programs live.sysinternals.com/Files/SysinternalsSuite.zip Complete archive of system utilities NirSoft - 56 programs www.nirsoft.net/system_tools.html AVZ developer site z-oleg.com
WARNING!
Using system utilities requires an understanding of the logic of their operation and the structure of the OS itself. Read the help before making changes to the registry or interfering with active processes.
First published in Hacker magazine #197. Author: 84ckf1r3
Subscribe to "Hacker"
- Site materials
- Paper version
- "Hacker" on iOS/iPad
- "Hacker" on Android