The mail ru mail service is very popular in our country. This was partly due to the fact that it appeared many years ago. Today, the number of owners of this account is still growing, despite the great popularity of Yandex and Google. A login and password are used to log into a mailbox, so one of the most common problems users have is restoring access. This can be done either via phone or in the full version of the site from a computer. Let's take a closer look at both of these options.
Forgotten password recovery
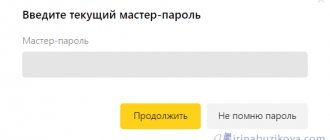
What to do if you forgot your mail ru password? It can and should be restored. It’s very easy to do this: 1. Go to the official website of the mail client https://mail.ru/
2. An authorization window will open in which you must specify the mailbox name and password. Under the form there is a “Forgot your password?” button that you need to click.
3. At the next stage, a page will load in which you need to indicate the mailbox to which you want to return access. We do this and click the “Restore” button.
4. Then a form will open with the secret question that you chose at the registration stage on the site. We give the answer to it and enter the captcha (numbers and letters from the picture). Click “Recover Password”.
Important! Next to the “Recover Password” button there is a “I don’t remember the answer” button. You need to click this if you have forgotten the answer to your security question. In this case, a questionnaire will be downloaded, which will subsequently be sent to the technical support service. If most of the answers are close to the truth, access to mail can be restored.
In the form, you need to fill out the “First and last name” fields, indicate your date of birth, select from the drop-down list approximately when the mail was registered and what the password was during registration. You also need to answer the security question again, enter an additional email address for communication and fill out the captcha cell. Finally, click the “Submit” button.
If the form is filled out correctly, the ability to restore your mail will become available instantly. The user will need to come up with a new password and enter it twice. Re-entry is required to confirm and verify the access code.
At this point, the procedure for restoring access to mail if you have forgotten your password can be considered complete. As you can see, there is nothing complicated. The main thing is that the mail really belongs to you.
Don't like one-time passwords? Then we go to you!
Depending on the developer’s imagination and the specific scope of application, a system using one-time passwords or keys can be called two-factor or two-step authorization, authentication, verification, or even some more tricky word. However, all of them generally come down to the use of two or more methods of user identification to perform a particular operation. Moreover, as a rule, the first step is to use the familiar login-password combination, which, to be honest, can be easily stolen and used remotely without the owner’s knowledge. But the second factor is something that, in theory, should be available exclusively to the user. Methods of forceful grip and something like a gentle request from an uncle with a hot soldering iron are not considered in this case, since it is unlikely that anything will save you from them.
Traditional picture with a hacker to intimidate the average person (Metasploit)
For the second stage of identification, many means can be used: key transfer via SMS/call/Push notification, USB tokens, physical and virtual key generators, biometric sensors, smart cards, “tablets” (as for intercoms), RFID tags ( NFC including), applications for mobile devices, one-time encryption pads and other, more exotic things. The essence of all these technical bells and whistles is the same - to access anything, in addition to the basic identification data (login-password), you also need to enter a one-time code. If an attacker stole the login and password from your account, he will not be able to use them, since he does not have a one-time password. If he managed to peek at a one-time code, then it is still useless to him, because the very name of the code indicates that he will not be able to use it a second time.
Bank cards for paranoids
Moreover, for greater security, one-time passwords often also have an extremely limited validity period, but such that even a very leisurely user will have time to enter it where needed, and the pest will not have time to find out. Of course, this approach does not provide 100% protection, which, as is known, does not exist at all, but it allows one to effectively protect against various types of attacks, and generally increase operational security. Yes, this somewhat reduces the usability of the services, and may even scare off some categories of users. The author personally observed a scene in one of the banks when the manager was actively convincing (mind you, in quite accessible and understandable language) a middle-aged client to sign up for the free service of authorizing payments on the Internet via SMS codes. To which the client muttered: “Too complicated,” and left, leaving the manager at a loss and not understanding how such a simple procedure could cause problems for a seemingly intelligent person. The example with the bank is not accidental, because it was financial organizations that were the first to adopt one-time codes.
Table of codes for the Yandex.Money service
Almost all online services, including social networks, send the same passwords via SMS. If not for logging in, then at least for resetting the main password. Dropbox has recently been offering its two-factor authentication to customers. And tables of one-time codes on or in paper form are now almost forcibly shoved into clients by any self-respecting banks and related organizations. Yandex.Money has long offered not only tables, but also electronic tokens for payment transactions. PayPal has a similar story. There are also more universal solutions like Rutoken or Yubikey, which can be used as not only an additional, but also the main means of identification (in the general case), as well as for encryption, access to mail, electronic money, and so on. Fortunately, standards for such devices and circuits have long been adopted and are being actively implemented.
Yubikey tokens
A hardware token usually costs around $50. If you really don’t want to spend money to protect yourself, then you can use free software solutions. Most often, they use a one-time code generation algorithm based on the current time, or HMAC, so they only require correct time synchronization across all devices used. Perhaps the most popular two-factor authentication solution is Google Authenticator. The description of working with it is described in some detail in the service help. Well, to get started we only need a Google account and a smartphone. You need to start registering with this wizard. All you need to do is share your mobile phone number with Google, and a smartphone with Android, iOS, Blackberry or WP7. (Option available with SMS or voice message confirmation for emergencies, as well as backup codes.)
After specifying the number, an SMS will be sent to it with a link to the corresponding application, which must be installed and launched. In it we select an account for which two-factor authentication will be active and follow the advice of the setup wizard. It is recommended to specify a backup phone number and e-mail in your account settings and print out codes to log into your account without a phone. After setting up your account, Google Authenticator will begin generating one-time passwords for it. When you next try to log in through the web interface, for example, in Gmail, you will be asked to enter not only your login and password, but also the current one-time code. For convenience, the PC from which you are logging in can be added to the list of trusted ones, so as not to have to go looking for your phone again. For applications like Google Talk or email clients that cannot work with two-factor authentication, you will have to generate special passwords (for each separately) that must be entered instead of the usual password for Google services. Answers to frequently asked questions about using the application can be found here.
In principle, Google Authenticator is based on open standards and has a PAM module with available source codes, which can be “screwed on” to almost any PAM-enabled system. For example, secure your SSH connection. It is also possible to find alternative solutions that implement the same standards for other platforms. However, the opposite is also true - some platforms and services already support two-factor authentication. To add a new account, you must either read the QR code with your smartphone’s camera (at first launch you will be prompted to install a suitable scanner) or enter a long identification code. For example, in this way we can increase the security of Amazon’s cloud services, which are so beloved by us (okay, well, beloved by the author).
On the page for enabling MFA, at the bottom there is a button Enable AWS MFA Device, clicking on which will open the IAM console. Opposite the Root Account MFA item, click on the Manage MFA Device button, and in the wizard that opens, select A virtual MFA Device. The user will be shown a QR code, and below, just in case, it is the same, but in text form. In Google Authenticator, in the application menu, go to the “Set up account” section, where to add a new profile, choose between scanning the code or manually entering it. Finally, in the last step, Amazon will ask you to enter two one-time passwords generated one after the other. In the future, as in the case of a Google account, temporary codes will be required from you or the attacker. If you get tired of this whole thing, you can disable two-factor authentication in the settings at any time or re-register your profile in Google Authenticator.
This is just a small example. Setting up other online services or programs is usually no more difficult. Alas, there are not very many of them now. In addition to the free Google service, there are many commercial solutions for increasing security through one-time codes, but they are mainly intended for corporate clients, and therefore are “tailored” for slightly different products and cost a lot of money. Among those that may be useful to ordinary users, it is worth noting the excellent Duo Security project, which also charges money only for SMS and calls, leaving other services free for personal use. The SecurEnvoy and PhoneFactor projects are no less interesting. The latter, by the way, was bought by Microsoft a month ago.
Duo Security asks
Of course, using one-time passwords is not a panacea for all possible threats. However, we recommend enabling two-factor authentication and other security systems wherever possible, from online banking systems to social networks. It definitely won’t be superfluous, but you still shouldn’t wait for thunder out of old habit. Well, we traditionally urge our readers to be as attentive as possible to their personal data and protect them to the best of their ability. Good luck!
Other recovery methods
Via a backup address. Above we looked at the option of restoring mail through a security question. But if during registration the user specified a backup address, then the procedure will look like this:
1. At the authorization stage, click the “Forgot your password?” button. and enter the name of the mailbox whose control we want to return.
2. Then a window will be displayed in which it will be written that the recovery link has been sent to the same backup address. All you have to do is enter the code from the picture and click the “Restore” button.
3. Now go to the backup email client and open the letter from the mail.ru support service. There will be a link in the body of the email, by clicking on which you can set a new password for the system.
4. Specify a new password, enter it again and click “Login to mail”.
That's all! Account management has been restored.
By phone number. Another way to regain control of your account is through a phone number. However, recovery by phone number is only possible if it was specified during registration. In this case, you need to do the following:
1. Click the “Forgot your password?” button. at the authorization stage and enter the name of the mailbox in the appropriate line.
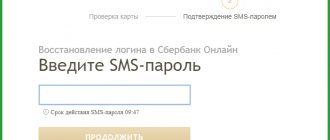
2. A window will then open indicating that the recovery code will be sent to your phone number. All you have to do is enter the code from the picture and click the “Receive code via SMS” button.
3. Wait for the SMS with the confirmation code and enter it in the appropriate cell. At the end, click “Done”.
After this, the already known recovery form will be displayed on the screen, in which you need to specify a new password and enter it twice.
Two-factor authentication Mail.ru
Hello again everyone. We continue our series of articles on improving account protection in popular services. We have already looked at how you can improve security in Yandex and Google. Now we will look at how to protect your account from Mail.ru.
Let us remind you that the security of your data is very important today. Therefore, it is not recommended to neglect it. Because if your account is hacked, attackers can get all your information from your correspondence, delete all letters, send spam messages on your behalf, and much more.
Thanks to mail.ru two-factor authentication, a hacker, even if he guesses the password to your mailbox, will not be able to gain access to it. Since you will need to enter a special code that will be sent to the phone attached to your account
If you do not yet have an account with the free mail service Mail.ru, then create one.
We go to the mail using our data. Then in the upper right corner of the browser (in our case – Opera Neon) click on the name of our account and select “ Password and security ”
We will be taken to the settings section dedicated to security.
We recommend reading “Secret tricks when working with a mouse”
Here, in the “ Two-factor authentication ” block, click on the “ Enable ” button.
A pop-up window will open asking you to enter a phone number.
Indicate a real number to which you always have access. Enter your phone number and click “ Continue ”
An SMS message with a code will be sent to this number almost immediately. Enter it in the first field, and in the second - the current password from your account and click " Accept "
After this, our two-factor authentication is enabled. Now, after entering the password, you need to specify an 8-digit code that will be sent to your gadget (tablet, smartphone, mobile phone). We'll see what this looks like later.
In the meantime, we are offered to set up two-factor authentication. This is not necessary, but it is recommended in case mobile communications suddenly become unavailable and you will not be able to receive SMS messages with verification codes. Let's look at them in more detail.
Methods to receive a verification code
Mobile app.
This method involves installing a special application on your smartphone or tablet to generate a random password. To do this, click on the “Connect” link, then select an application from those offered, then enter the password from SMS, install this application on your gadget, and scan the QR code to activate. We did something similar when we connected Yandex Key.
Reserve codes.
If, say, you sent your phone in for repair or, God forbid, you lost it or had it stolen from you, then these backup passwords will help you log into your account. Each set of numbers is valid only once.
To receive 10 one-time codes, click on the “ Create and Print ” button. Next, enter the current password and code from SMS. After which you will see a list of 10 combinations of numbers. Keep them in a safe place. In this way, you can create the next 10 passwords or simply replace the current ones.
Passwords for external applications (programs)
If you use email clients such as The Bat, Mozilla Thunderbird (you will find a series of articles for it on our website. See the first article here) or use an email application on a smartphone or tablet, then for correct operation you need a special password. We will get it here. Click on the “ + Add application ” button.
We give a name, for example, “The Bat” or “mobile application”, then indicate the current password for the account and you will see a set of characters that you need to enter into the mail client or application as the password to your mailbox from mail.ru.
Are your eyes tired? Exercise for them
Stop trusting all devices.
In order to understand why this setting is needed, let's log out of our account and log in again. We indicate our main password.
And click Login
Literally in a second you will receive an SMS with a code on your smartphone or tablet, enter it in this field
Don’t ask for this device checkbox will be checked just below . This means that the next time you access your mailbox from this device, you will be logged in automatically, without a one-time password from SMS.
If you don’t want your email to be logged in automatically (for example, you logged in from someone else’s computer, you lost your phone, etc., or you simply forgot to uncheck the “Don’t ask for this device” checkbox), then this setting will reset it. After clicking on the “Stop trusting all devices” button, you will again receive an SMS with a code to enter your mailbox.
Disable two-factor authentication
In order to disable two-factor authentication, you need to go back to the “ Password and Security ” settings (see screenshots 1 and 2) and click on the Disable link
You will then be able to log into your account without verification codes. This is the only way your account becomes less protected. In this case, do not forget to change your password at least once every six months. To create a strong and complex password, use a special online service or use a password card.
So, perhaps, we'll end here. Today we looked at how to protect your mail.ru account using two-factor authentication. Please write in the comments if you use a similar method to protect your account.
Good mood to you all. See you again!
I am just a lucky coincidence for Russia.
Mikhail Illarionovich Kutuzov
What other ways are there to recover your Mail ru password?
You can contact the site’s support service by first creating an email where you will receive responses from technicians. And the recovery process itself looks like this:
- You should enter the corresponding dialog box and go to the section using the support link.
- In the dialog box, enter the personal data specified during registration - first and last name, date of birth, and gender.
- indicate the email to which replies will be sent.
Next, describe in detail the data that you were able to remember:
- this is the name of the folders saved in your account.
- the latest letters coming to you - who they were from and what the subject was, date and time.
- also try to remember the year or approximate period of creation of your own account.
As a rule, the technical support service responds within 2-3 days, but often no answers came from them at all.
4 facts about the Tele2 tariff for children - mobile communications for a child without the Internet.
The cheapest roaming abroad: which operator is best to travel with is discussed in this review.
Instructions for checking the authenticity and counterfeit of banknotes using your phone: