Passwords are the keys to your virtual data storage on the Internet - from your mail account, online game, personal page on a social network, etc. Of course, it must 100% meet the criterion of reliability. That is, it must be resistant to hacking or picking. Unfortunately, many users ignore this simple but mandatory requirement for passwords. And in the end, as a rule, they become victims of attackers. They lose money, confidential data, gameplay achievements, etc.
It is known that 1% of network users, either because of laziness or negligence when registering, prefer to use primitive combinations that can be selected in 3-4 attempts. Examples: “123456”, “qwerty”, “mypassword”. This, of course, is very stupid. An “easy” key for the user is also “easy” for the cracker.
This article will tell you how to create strong passwords and how to test them for their resistance to hacking.
What password can be called reliable?
Good account keys have the following characteristics:
1. Length of at least 10-15 characters (the most stable combinations are even longer - 20-35 characters).
2. Character composition: large and small English letters, numbers, special characters.
3. The combination does not contain dictionary words (parol, kod, vhod), personal data (phone number, name, e-mail, etc.), logical sequences of letters and numbers (1234, 246810, abcdefg).
The more complex and reliable the combination, the more difficult it is to select it. It may take over 1.5 million years to establish a user-created sequence of 12 characters.
Creating a secure password
If, based on the results of the analysis, it turns out that you can’t expect to sleep peacefully for at least the next few billion years, I suggest you use the online password generator service. It will help you create an extremely strong password, which is distinguished by the fact that it cannot be cracked by brute force. To do this, it must contain:
- at least 8 characters (preferably more than 12)
- lowercase and uppercase letters of the alphabet
- numbers
- symbols
All options are easily configured using the appropriate checkboxes. I took one of the passwords generated by this service and tested it for cracking speed. You can evaluate the results yourself:
Friends, no one will take care of the safety of your personal data except you. It is always better to prevent unpleasant consequences in advance than to solve problems that arise later. The online services described today will help you in the best possible way to prevent possible troubles. Good luck!
I also recommend that you familiarize yourself with the email protection service from StarForce.
Creating a complex key
Ordinary Internet users and security specialists have already found many correct answers and solutions to the question “How to create a strong password?” In this article we will get acquainted with the three most practical methods.
Method number 1: substitution of letters
Not all early mobile phones supported the Russian language, and their owners sent SMS using transliteration. That is, they wrote in Russian in Latin letters, and replaced the missing letters with symbols. For example: “h” - “4”. The phrase “What are you doing?” looked like “4to delaesh?” The same principle underlies this method of compiling keys.
Take a word or phrase, and then write it down using “tricky” notations. Instead of spaces, you can use any special characters “~”, “/”, “.” etc. For example, you can come up with the following combination:
We will write “Danger Zone” as “onACHA9I#3OHA”.
As you can see, we wrote the words in Latin letters and, in addition, replaced some Russian letters. Instead of “p” - “n”, “i” - “9I”, “z” - “3” (the number “three”). And they put a separator “#” between the words. So it turned out to be a rather complex option. To solve this type of symbolic combination, computer villains will have to work hard.
To help, a table of symbolic designations of Russian letters:
Method No. 2: creating a “readable” key in the generator
1. Open the online service in your browser - https://genpas.peter23.com/.
2. In the “Operation mode” option, click the “Pronounceable password...” radio button.
3. Additionally enable/disable character sets for key combinations and set its length.
4. Click the "Generate" button.
5. Select the most optimal option from the generated sequences.
6. Break the selected password into fragments of 2-3 characters and give each fragment a specific meaning. In such a “logical chain” it is very easy to remember the most complex combination. As an example, let's look at the key created in this generator:
Xoh)ohfo1koh
- Xoh) - can be read as “Xoh” + “smiley”;
- oh - “oh”;
- fo1 - let it be some kind of mysterious abbreviation;
- koh - koh - again a variation of the initial syllable.
Method No. 3: adding special characters to simple words
1. Take as a basis a word you know well:
space2017
2. Come up with a combination of special characters of 2 or 3 characters.
«+_&»
3. Add a combination at the beginning and end of the word in a mirror image.
+_&space2017&_+
4. As a result, you will get a fairly “strong” key. Of course, it cannot be called the most stable, but it is easy to remember and is not primitive in its structure.
Attention! Before creating a password, be sure to read the requirements of the service you are registering for. For example, on the Mail.ru portal you cannot use the Cyrillic alphabet (Russian letters).
Checking password complexity in JavaScript
Many sites have a password complexity check
.
There are many different options for checking how complex a password is, and I will show one option for checking password complexity in JavaScript
in this article.
First, let's create a simple HTML form
:
Password:
And now the checkPassword()
:
function checkPassword(form) { var password = form.password.value; // Get the password from the form var s_letters = "qwertyuiopasdfghjklzxcvbnm"; // Lowercase letters var b_letters = "QWERTYUIOPLKJHGFDSAZXCVBNM"; // Uppercase letters var digits = "0123456789"; // Numbers var specials = " [email protected] #$%^&*()_-+=\|/.,:;[]{}"; // Special characters var is_s = false; // Does the password contain lowercase letters var is_b = false; // Does the password contain uppercase letters var is_d = false; // Does the password contain numbers var is_sp = false; // Are there any special characters in the password for (var i = 0; i < password.length; i++) { /* Check each character in the password to see if it belongs to one type or another */ if (!is_s && s_letters.indexOf(password ) ! = -1) is_s = true; else if (!is_b && b_letters.indexOf(password ) != -1) is_b = true; else if (!is_d && digits.indexOf(password ) != -1) is_d = true; else if (!is_sp && specials.indexOf(password ) != -1) is_sp = true;
} var rating = 0; var text = ""; if (is_s) rating++; // If the password contains lowercase characters, then increase the difficulty rating if (is_b) rating++; // If the password contains uppercase characters, then increase the complexity rating if (is_d) rating++; // If the password contains numbers, then increase the complexity rating if (is_sp) rating++; // If the password contains special characters, then increase the complexity rating /* Next, the length of the password and the resulting rating are analyzed, and based on this, a text description of the password complexity is prepared */ if (password.length < 6 && rating < 3) text = “Simple "; else if (password.length < 6 && rating >= 3) text = “Average”; else if (password.length >= 8 && rating < 3) text = “Average”; else if (password.length >= 8 && rating >= 3) text = “Difficult”; else if (password.length >= 6 && rating == 1) text = “Simple”; else if (password.length >= 6 && rating > 1 && rating < 4) text = “Average”; else if (password.length >= 6 && rating == 4) text = “Difficult”; alert(text); // Display the final password complexity return false; // We do not send the form } The function, although not very small, but its essence is extremely simple. First of all, we check for the presence of various characters in the password. The more different types of symbols, the better. Then, by analyzing the length and the resulting rating, you can display one or another password complexity.
Of course, there are options for checking password complexity in JavaScript
there are a lot, and you now know how to implement one of them.
And if you want to learn how to create similar scripts yourself, and even much more complicated ones, then you need to learn JavaScript
. This can be done here.
- Created 01/29/2014 13:19:21
- Mikhail Rusakov
Using Google to check passwords
The service will tell you which passwords were previously in the hands of hackers.
Today you can check whether your passwords stored in your Google account are in the hands of criminals. To do this, just go to the password manager: it will compare your data with the database of all major leaks.
Google collects information about leaks itself. Most of the data comes from open sources, but sometimes the company finds stolen passwords on the dark web.
If Google discovers that some of your passwords have previously become publicly available, it will offer to change them. The service will also notify you if you use the same password on a large number of sites. The dispatcher will also warn you about passwords that are too weak and easy to guess.
Comfortable? Undoubtedly! Safely? Don't think.
How it works?
Of course, you know that Google has had a password manager for quite some time that syncs between Chrome and Android. In this manager, the company is adding a “password check” feature that will analyze your logins to make sure they were not part of a serious security breach, because there have been many, many such password leaks to date.
Password verification was previously available as an extension, but Google is now building it right into Google Account controls. You can check your passwords at passwords.google.com, which is a URL shortcut to Google's password manager.
Your credentials are compared to millions of millions of compromised accounts that were part of serious breaches. Google says it also has some control over the dark web for collecting passwords, but most of the database against which password checks are compared comes from crawling the open web.
It is worth understanding that Google is by no means the only service that does such checks. In an era of constant leaks and security breaches in large companies that affect tens, and maybe hundreds of millions of customers, haveibeenpwned.com turned out to be such a useful resource.
If your password is compromised or is too simple, Google will prompt you to change the corresponding password. The same goes for if Google sees that you are reusing passwords, which is a terrible practice; after all, all services must have a unique login password. And of course, Google will also notify you about accounts that use weak passwords that are easy to guess. Please note that passwords were hashed and encrypted before being sent to Google.
Because password verification relies on sending your sensitive information to Google, the company is keen to emphasize that it is encrypted and that it cannot view your data. Passwords are stored hashed and encrypted in the database, and any alerts about your data are entirely local to your computer.
Mark Risher, Google's director of account security, noted that consumers are increasingly being asked to store their passwords in multiple places at once. Apple has iCloud Keychain. Google has a password manager. And then you have password managers - 1Password, LastPass and other third-party password managers. What to do? Choose a manager and stick with it in the future? Or try to sync multiple password managers? The likelihood of a mismatch or old incorrect password in one of these places is quite high. There's really no good answer to this question
According to a Harris Poll examining the password habits of US users, the results are quite alarming. Too many still include items in passwords that a stranger could easily recognize—like birthday, pet name, etc. And few talk about the benefits of additional security measures like two-factor authentication (only 37% of respondents use it) and password managers (15%).
66 percent of those surveyed said they use the same password for multiple online accounts.
Password reuse is a major habit that Google is trying to break because using the same password for multiple services can put you in a terrible position if even one of the services is compromised. If you're not a fan of digital password managers, just write them down somewhere at home. Even this is a good option because you won't be repeating the same password.
Why won't I use this service?
First of all, because it ties me to the Google browser, and I don’t like that. Alas, using Google Chrome in a corporate environment, from my point of view, is a bad idea. Why?
Firstly, primarily because I have never learned how to centrally manage the settings of this browser using group policies. It may be possible, but I didn't see it.
Secondly, difficulties will arise with updating the browser. After all, you can update it only with administrator rights. And which of us in a sober mind will give the user local administrator rights? I think no one.
I agree that this service is primarily intended for personal users. And there are a number of questions here.
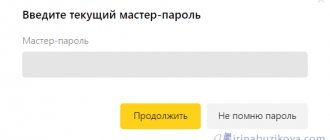
Do you trust Google? I have great difficulty. Remember “Passwords are stored in encrypted form.” And now the question. Where is the master password stored? You? Don't think. Most likely it is stored by Google specialists. In extreme cases, there is no reliable information about this.
But what if you use more than just the Google Chrome browser? For example, you use Chrome at home, but your tablet is from Apple, just like your iPhone. Then you will have to install Google's browser on all devices.
What do I recommend? Use third-party password managers. Fortunately there are many of them. And then, I would recommend using the paid versions.
However, of course, it’s up to you to choose.