Rootkits are a type of malicious software that is embedded into the operating system (OS) of a computer and allows an attacker unlimited access to it via a remote connection.
Initially (more than 20 years ago), rootkits were intended to hide remote manipulations by an attacker or traces of viruses and Trojans on the victim’s computer. Today, rootkits are any set of utilities that:
- hide their activities or the activities of other processes;
- manipulate OS processes;
- provide access to OS tools via the network;
- collect user data and send it over the network.
What is a rootkit?
A rootkit is one or more programs that hide the presence of unwanted applications on a computer, helping attackers operate undetected. It contains absolutely the entire set of malware functions. Since this application is often located deep in the depths of the system, it is extremely difficult to detect it using an antivirus or other security tools. A rootkit is a set of software tools that can read stored passwords, scan various data, and also disable PC security. In addition, there is a backdoor function, which means that the program provides the hacker with the opportunity to connect to the computer from a distance.
In other words, a rootkit is an application that is responsible for intercepting system functions. For the Windows operating system, the following popular rootkits can be identified: TDSS, Necurs, Phanta, Alureon, Stoned, ZeroAccess.
ROOTKIT
Launch the downloaded file. No installation is required and it is advisable to have an active internet connection.
Click the “Accept” button twice.
In the “Everything is ready for testing” window, click on the “Start scanning” button. You can leave the “Change settings” option untouched and wait for the scanning process to complete and the detected threats to be neutralized.
This article ends for those users whose rootkit was found and successfully neutralized. And for me, after completing the scan, it turned out that the assumption about the introduction of rootkits into the operating system was initially incorrect. The anti-rootkit utility did not detect any threats.
If you find yourself in a similar situation, first of all run the OS anti-rootkit utility, and then, if all else fails, change your antivirus. Only if it is not Kaspersky Anti-Virus, but one of the free ones.
Free is not always better. Thank you for your attention!
PS If you are interested in video instructions on how to install Ubuntu OS next to Windows, then go to.
Varieties
There are several variants of these virus programs. They can be divided into two categories: user-mode (user) and kernel-mode (kernel-level rootkits). Utilities of the first category have the same capabilities as regular applications that can be run on the device. They can use the memory of already running programs. This is the most popular option. Rootkits of the second category are located deep in the system and have full access to the computer. If such a program is installed, then the hacker can do almost whatever he wants with the attacked device. Rootkits of this level are much more difficult to create, which is why the first category is more popular. But a kernel-level virus program is not at all easy to find and remove, and protection against computer viruses is often completely powerless here.
There are other, rarer variants of rootkits. These programs are called bootkits. The essence of their work is that they gain control of the device long before the system starts. More recently, rootkits have been created that attack Android smartphones. Hacker technologies develop in the same way as computer software - they keep up with the times.
Antiviruses and other automated tools
A rootkit known to the antivirus can be easily detected by scanning email attachments or network packets, but even in this case, the hacker has many ways to break the horns of the antivirus. Let's say a rootkit is thrown through a hole in a browser that does not process TIFF files correctly. Then the attacker just has to lure the victim to a link like https://www.xxxx.com so that the antivirus will miss the necessary network packets.
As for searching for active rootkits, even if they are known to the antivirus, they still have every chance of escaping retribution, especially if the antivirus is known to rootkits. For example, there is such an interesting utility as Rootkit Revealer from Mark Russinovich . According to its creator, it detects all rootkits presented on www.rootkits.com, which is not true - a trivial check reveals a large number of malware that monitors the launch of Rootkit Revealer and modifies its code in memory so that it does not show anything . Naturally, this technique only works with strictly defined versions of Rootkit Revealer (the rootkit must know the exact location of machine instructions in memory). And since malware developers have no desire to track the release of new versions, they limit themselves to an attack like WM_X, which boils down to manipulating elements of the user interface by sending appropriate messages (Window Messages) that remove detected rootkits from the list displayed by Rootkit Revealer, which works with all versions. But detected rootkits still end up in the log file.
In addition, Rootkit Revealer finds only those rootkits that: a) modify the registry and/or file system ; b) hide traces of their presence . If at least one of these conditions is not met, the rootkit will not be detected. Analysis of the code of some rootkits shows that they monitor the appearance of the Rootkit Revealer window and stop their disguise while it is running. It is high time for developers of security utilities to take polymorphism into their arsenal - as long as they are detected by rootkits, there can be no talk of any kind of protection! An antivirus should not have a permanent signature (as well as windows with pre-known titles)!
The world of rootkits is not limited to the demos posted on www.rootkits.com. Judge for yourself: developing a high-quality rootkit is a complex engineering task , and such rootkits are not written in one evening. Only the most needy (or desperate) dare to trade rootkits (due to their semi-legal status). So what is the point in releasing a rootkit to the public? Perhaps in order to make a name for yourself and compete in coolness with other hackers. But! Professional programmers have long passed the stage of self-assertion and, instead of working for an idea, they prefer to code for money on individual orders (at least they will have something to hire a lawyer for).
Reuse (that is, reuse of code) practically does not occur in such rootkits, and only a few end up in anti-virus databases. As mentioned above, a properly planned attack involves the self-destruction of the rootkit after some time. And how can you catch it if it exists only in RAM?! You can, of course, transfer a core dump of the operating system to antivirus companies, but there are three caveats. First of all, what antivirus company would poke around in it? Secondly, that’s a lot of traffic! Thirdly, in addition to the rootkit, the dump may contain a ton of secret information that is highly undesirable to disclose, such as passwords.
It is important to understand that, unlike viruses and worms , which spread from computer to computer and sooner or later fall into anti-virus traps, real rootkits exist in single copies , and therefore only proactive technologies, such as heuristic analysis, can detect them. However, if the customer of the rootkit is at least a little smart, he will definitely check whether the rootkit is fired by the latest versions of antiviruses using the strictest heuristic mode (in which the antivirus swears even at honest programs), and, if so, will return it back for revision.
Therefore, as a working thesis, it is necessary to accept that rootkits are not detected by antiviruses , no matter how brainwashed we are by the creators of antiviruses.
Homemade rootkits
A huge number of infected computers are located on the so-called zombie network and are used to send spam messages. At the same time, users of these PCs do not suspect anything about such “activity”. Until today, it was common to think that only professional programmers could create these networks. But very soon everything could change dramatically. You can actually find more and more tools for creating virus programs on the Internet. For example, using a kit called Pinch, you can easily create a rootkit. The basis for this malware will be the Pinch Builder Trojan, which can be enhanced with various functions. This application can easily read passwords in browsers, recognize entered data and send it to scammers, and cleverly hide its functions.
Literature about rootkits
The topic of malware tools is very extensive and often deserves at least several articles devoted to all aspects of the use of rootkits, bootkits, firmware backdoors, hooks, injections into executable processes and replacements. Since the scope of this article does not allow us to talk about everything, we can recommend to you, dear friend, several good books and resources on the Internet for self-study of materiel :).
Rootkits: Subverting the Windows Kernel (Greg Hoglund, Jamie Butler)
One of the few books generally devoted to rootkits and technologies for their detection in Windows systems. A real must-have for a novice researcher inexperienced in the intricacies of Windows.
Inside Windows Debugging (Developer Reference)
Quite an interesting book that tells step by step from the very basics about technologies for debugging various programs under Windows OS, the architecture features of this OS, debugging tools and techniques, features and other equally important details.
Rootkits and Bootkits. Reversing Modern Malware and Next Generation Threats
A book that is worth recommending first. A most valuable collection of information about rootkits and bootkits, their operating algorithms, implementation features in the OS, detection and countermeasures methods.
Rootkits and Bootkits
Wasm.ru archive dedicated to low-level programming. No comments needed - the largest collection of Russian-language materials on low-level programming, writing drivers, system modules and applications running in ring 0.
Ways to infect a device
Initially, rootkits are introduced into the system in the same way as other virus programs. If a plugin or browser is vulnerable, it will not be difficult for the application to get onto your computer. Flash drives are often used for these purposes. Sometimes hackers simply leave flash drives in crowded places, where a person can take the infected device with them. This is how a rootkit gets onto the victim’s computer. This leads to the application exploiting the weaknesses of the system and easily gaining dominance in it. The program then installs auxiliary components that are used to control the computer from a distance.
Methods of infection
Penetration methods are no different from other classes: viruses, worms, Trojans:
- visiting unreliable sites - exploiting “weak spots” in the browser;
- through other devices, sometimes attackers deliberately leave flash drives in visited places;
- suspicious files sent by mail, etc.
As a rule, all it takes to become infected is one small file that “hides” inside the operating system. Then he finds her vulnerabilities and gains administrator rights . Next, the rest of the software necessary for parasitic purposes is loaded.
Phishing
Often the system is infected through phishing. There is a high possibility of code getting onto your computer during the process of downloading unlicensed games and programs. Very often it is disguised as a file called Readme. We should never forget about the dangers of software and games downloaded from unverified sites. Most often, the user launches a rootkit on his own, after which the program immediately hides all signs of its activity, and it is very difficult to detect it later.
What are they doing
A rootkit is almost always written for one specific purpose: illegally obtaining money. If it eludes detection, it hides where no one can detect it and gives the attacker backdoor access to the computer. At this point, the criminal receives all the rights that a system administrator and programmer may have. With complete control, a hacker can view a computer remotely, stealing personal information (for example, bank account access data) and rewriting the software to suit his own purposes.
Once a rootkit is installed, it will remain hidden, but there are a number of signs that your computer has been infected:
1. The antivirus program stops working and/or cannot be reinstalled. 2. Some programs cannot be opened. 3. The mouse stops working. 4. The browser cannot be opened and/or Internet access is blocked. 5. The screensaver or desktop wallpaper has changed and cannot be changed. 6. The network suddenly becomes very busy, very slow, or goes down completely. 7. You do not see the taskbar 8. The computer does not boot and/or freezes.
Again, other than a rootkit, no other type of malware can evade detection by an antivirus program or firewall and successfully remain undetected after infiltrating a computer.
Why is a rootkit difficult to detect?
This program intercepts data from various applications. Sometimes the antivirus detects these actions immediately. But often, when the device has already been infected, the virus easily hides all information about the state of the computer, while traces of activity have already disappeared, and information about all harmful software has been deleted. Obviously, in such a situation, the antivirus has no way to find any signs of a rootkit and try to eliminate it. But, as practice shows, antivirus programs are capable of containing such attacks. And companies that produce security software regularly update their products and add the necessary information about new vulnerabilities.
AVZ
Multifunctional antivirus scanner created by Russian programmer Oleg Zaitsev. Capable of finding and neutralizing any type of virus (including SpyWare and Adware modules, Trojans, worms). Equipped with a special tool for effectively identifying rootkits - a custom Anti-Rootkit module.
To scan Windows for viruses using the AVZ utility, follow the guide below:
1. Go to the download page - z-oleg.com/secur/avz/download.php (the official web resource of the developer).
3. After downloading, unpack the archive: right-click → Extract all.
4. Run the AVZ file (the “shield and sword” icon) with administrator rights.
5. Update the signature database of the utility: in the vertical button bar located in the lower right part of the window, click on the “globe” button. In the new window, click Start.
6. Make preliminary settings on the tabs:
- “Search area”
- check the boxes next to the disk partitions that you want to scan; - “File types”
- enable the “All files” option; - “Search parameters”
: in the “Heuristic analysis” block, move the threshold control up (to the “Maximum level” value), turn on the “Advanced analysis” function; in “Anti-Rootkit” set the flags next to all add-ons (detect interceptors, block Rootkit User-Mode and Kernel-Mode).
7. To start checking the partitions, click on the “Start” button.
Shareware solution (trial - 180 days) from the domestic developer Greatis Software. It equally successfully fights both rootkits and browser hijackers and adware. Supports safe mode. Compatible with Windows 10.
To use the utility:
1. Download the installer from the offsite (greatis.com/unhackme/): click the “Download” button on the page.
2. Unpack the downloaded archive (right click → Extract all).
3. Run the unhackme_setup. Follow the installer's instructions.
4. Click the utility shortcut on your desktop.
5. In the application window, in the “Settings” section, in the “Search for rootkits...” block, check whether the “Active” option is enabled.
6. Go to the “Check” tab and click the red button with the same name.
7. In the menu that opens, select the scanning mode:
- “Online check...” - connecting databases located on the developer’s server;
- “... test” - operational testing;
- “Scanning…” - detection and neutralization in safe mode.
Search for rootkits on your computer
To search for these malicious programs, you can use various utilities specially created for this purpose. Kaspersky Anti-Virus copes well with this task. You just need to check your device for all kinds of vulnerabilities and malware. Such a check is very important to protect the system from viruses, including rootkits. Scanning detects malicious code that anti-unwanted program protection could not detect. In addition, the search helps to find operating system vulnerabilities through which attackers can distribute malicious programs and objects. Are you looking for suitable protection? Kaspersky is quite suitable for you. A rootkit can be detected by simply running a periodic search for these viruses on your system.
To search for such applications in more detail, you need to configure your antivirus to check the operation of the most important system files at the lowest level. It is also very important to ensure a high level of self-protection of the antivirus, since a rootkit can easily disable it.
What kind of virus is a rootkit?
A rootkit is a separate type of hacker utilities that are aimed at hiding the effects of viruses in system files and individual folders.
Such software appeared more than 20 years ago and still exists thanks to constant updating. Rootkit can be used to hide other viruses or act as a stand-alone injection tool.
The main “functions” of rootkits are:
- Organization of unauthorized access to a PC by hackers and intruders.
- Help in hiding program activities from antivirus systems and the built-in Windows scanner.
- Complete disabling of antivirus activity by penetrating the files of the defender program.
Most often used by attackers for phishing (theft of personal data), borrowing computer power for mining, organizing DDOS attacks, hiding the real location when conducting illegal operations on the Internet.
Rootkit is the most common and dangerous type of threat
Despite constant evolution and the possibility of hidden influence, most antiviruses are already able to detect the activity of a virus - thanks to in-depth search and intelligent analysis of the behavior of certain files.
However, this requires an increase in scanning time, as well as the use of additional power, which in combination slows down the computer, sometimes even disabling some programs.
Checking drives
In order to be sure that your computer is safe, you need to check all portable drives when you turn them on. Rootkits can easily penetrate your operating system through removable disks or flash drives. Kaspersky Anti-Virus monitors absolutely all removable storage media when they are connected to the device. To do this, you just need to set up a drive scan and be sure to keep your antivirus updated.
Rootkit Basics
From the average person's perspective, a rootkit is a nasty, scary, and even dangerous form of malware. It is one of the persistent and most serious security threats today. It enters the computer without the user's permission, silently disables anti-virus protection and allows the hacker to become an rogue administrator, gaining complete virtual control and access to your system. (And rootkits for mobile systems are already appearing.)
Rootkits do not differentiate based on which operating system they invade. Whether it's Windows , Apple , or Linux , an installed rootkit secretly replaces parts of the operating system with something that appears normal at first glance. This allows him to remain undetected and perform damaging actions. When you turn on your computer, the BIOS (Basic Input Output System) is used to start the system, and a rootkit can gain control of that too.
Security vulnerabilities (such as unpatched backdoors), infected torrents, or downloaded software allow a rootkit to gain access to your computer.
Removing a rootkit
There are many challenges in fighting these malicious applications. The main problem is that they are quite successful at resisting detection by hiding registry keys and all their files in such a way that antivirus programs cannot find them. There are helper programs for removing rootkits. These utilities were created to search for malware using various methods, including highly specialized ones. You can download a fairly effective program called Gmer. It will help destroy most known rootkits. You can also recommend the AVZ program. It successfully detects almost any rootkit. How to remove dangerous software using this program? This is not difficult: we set the necessary settings (the utility can either send infected files to quarantine or delete them independently), then select the type of scan - full or partial PC monitoring. Then we run the test itself and wait for the results.
A special program called TDSSkiller effectively fights the TDSS application. AVG Anti-Rootkit will help remove remaining rootkits. It is very important after using such assistants to check the system for infection using any antivirus. Kaspersky Internet Security will cope with this task perfectly. Moreover, this program is capable of removing simpler rootkits through its disinfection function.
You must remember that when searching for viruses with any security software, you should not open any applications or files on your computer. Then the check will be more effective. Naturally, you must remember to regularly update your antivirus software. The ideal option is daily automatic (set in the settings) program update, which occurs when connected to the Internet.
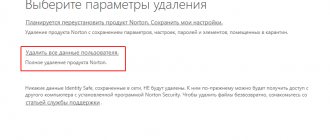
How to disable rootkit scanning in Kaspersky
Due to such restrictions, some users want to disable the option to search for rootkits in Kaspersky - but is it worth doing? In fact, without this aspect, checking files is almost useless - it will only help you find open infections, which are rarely used by sophisticated hackers.
As a result, the user gets rid of only basic Trojans and worms, and the device continues to be attacked in stealth mode. Therefore, disable the function at your own peril and risk - we offer simple instructions for this:
- Open the Kaspersky client and go to the main screen.
- At the bottom there is a gear familiar to everyone - press it and get into the program settings.
- In the right menu we find the “Performance” column.
- The last item “Search for programs designed to hide traces of malicious programs in the system” is what you need.
- Uncheck the box on the left and restart the computer to rescan and save the data.
Disabling search and scanning for rootkits in Kaspersky
You can't get rid of them
Now you know that if your antivirus program stops working, or your browser won't open, or your screensaver has changed unexpectedly, then most likely your computer has a rootkit.
At such a moment, a rootkit gives a whole new meaning to your life, when your computer “goes to pieces” and you realize that you haven’t made a backup copy for a long time.
If a rootkit is detected, it most often cannot be removed. Many programs claim to provide the ability to remove a rootkit, but at best this capability is fairly tenuous. As mentioned earlier, a hacker with administrator rights can do anything with a computer. It can be almost impossible to scan every program, every file of the operating system for remnants of infection.
Using an antivirus program and manually cleaning the computer are not options to solve the problem. You may notice that the solution is also not a system restore operation. A rootkit penetrates the very core of a computer's system, so any restore point is likely to be infected by it.
The only way to get rid of a rootkit that has entered the system is to erase all information from the hard drive and then install a new, clean copy of the operating system. Since it is never known whether a rootkit has been removed, this is the only way to ensure that the infection is eliminated.
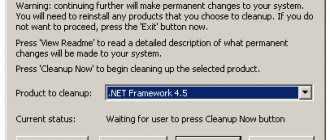
Download and Install
The first step is to download the installation distribution to your computer. Where and how to do this is up to everyone to decide for themselves. The demo version can be downloaded from the official website; it will work for 30 days, after which it will require activation. Once the distribution is on your computer, you will need to run it.
After launch you will see the following window:
When you click the “Install” button, the next tab will open with a license agreement, which, as usual, you just need to accept. Next is another agreement, after which the actual installation of the program on the computer begins. It lasts about 15 minutes.
The program will run for quite a long time, analyzing the operating system and the state of the computer as a whole.
After this, Kaspersky Internet Security will require you to enter a license key. If you have it, enter and activate the program; if not, choose the trial version.
This is the last step, after which KIS 2020 will be installed on your computer. You will be taken to the main menu and will find that the antivirus databases are very outdated. This is due to the fact that the installation distribution contains a minimum set of information with the expectation of using the Internet to regularly update anti-virus databases. What you will need to do is click on update and wait.
Types of rootkits
Rootkits can be divided into two main categories:
- User level
- have rights on the computer equal to other applications. They interfere with other processes and use their memory. The most common type. - Kernel level
- penetrate the system and gain almost unlimited access to any processes. They are noticeably less common, apparently because they are more difficult to create. They are less easily detected and removed.
Examples of common applications:
- Alureon;
- TDSS;
- Necurs.
In addition to the main ones, there are rarer forms - bootkits. They convert the bootloader and take over control
without waiting for the operating system to start. Due to the increasing importance of smartphones, rootkits running on Android can be found in the last few years.
How to remove a rootkit
Kaspersky TDSSKiller.
The free TDSSKiller utility from Kaspersky Lab is designed to treat a system infected with malware of the Rootkit.Win32.TDSS family, bootkits and other known rootkits. It is quick to use and does not require installation.
To download TDSSKiller for free, go to the official website support.kaspersky.ru
After launching the program, you can immediately start scanning or add objects to scan. To do this, go to the “Change scan parameters” tab and check the required boxes.
Dr.Web CureIt.
Using this utility, you can scan your computer not only for rootkits, but also for other malicious objects, followed by treatment. Dr.Web CureIt is free and does not require installation.
Today you will learn what a rootkit is.
and
how to remove a rootkit
from your computer, keeping your computer safe from these malware.
What is a Rootkit?
A rootkit is a program, script, or some set of software tools that gives an attacker (the owner of the rootkit) full access to another user’s computer or, in the worst case, the network as a whole. By “full access” here we directly mean access at the Head Administrator (SuperWiser)
.
It is worth understanding that a Rootkit is
not just a dangerous utility, it acts in such a way as to introduce harmful “add-ons” or applications onto your PC: Trojans, spyware and other viruses.
Why are rootkits so dangerous?
The main form of rootkit attack is stealth. They will be hidden deep in the depths of your computer. Since they have administrator level access, they can, for example, block your Windows search and hide any information about RootKits, control AntiVirus and literally “order” it to ignore Rootkit, hide from the list of active processes and much more!
The most famous Rootkit was installed on some Sony devices. Sony hid RootKit on people's computers as part of its digital rights management strategy. This gave them effective control over users' computers. Security expert Sysinternals discovered this RootKit and it caused a huge resonance in the global community. Sony offered users to download RootKit as additional software, and also presented it as a required process. This reinforces the fact that RootKits are very difficult to detect and this makes them dangerous.
How to remove Rootkit
It is very difficult to answer this question. Don't expect your antivirus or firewall to be 100% likely to help you here. The best RootKits can easily defeat your antivirus software, so in order to remove the rootkit
You need special tools.
There are special programs and services for this. One of the domestic developers can safely be considered Kaspersky Lab and a specially written “killer” of rootkits, which can be downloaded from this link. And in general, their products are quite high quality, so you can, and then, which is actually quite simple.
Similar news:
Security Security
And he told what it was, listed the main symptoms of infection and gave recommendations for ensuring computer security. If you haven't read it, be sure to check it out. After all, as they say, forewarned is forearmed.
Because today we will talk about how to remove rootkits using special . All actions will be performed manually.
The utilities discussed below are absolutely free and do not conflict with installed antivirus software. So feel free to use them. It is advisable to first boot into safe mode.
chkrootkit tool (Check Rootkit).
chkrootkit (Check Rootkit) is a Unix program designed to help system administrators check their system for known rootkits. This script uses common UNIX/Linux tools (such as strings and grep commands) to search for core system programs for networks/signatures by comparing filesystem/proc files with the output of the ps (process state) command to look for various discrepancies. The utility can be used by running a "rescue disk" (usually a Live CD) or the utility can be installed on the system.
The utility has modules for various scanning:
* chkrootkit - A module that checks your OS.
* ifpromisc - Used to search for interface(s) that operate in packet capture modes.
* chklastlog - Used to detect various facts of deleting records from the lastlog log file.
* chkwtmp - Used to detect cases of deleting records from the wtmp log file.
* check_wtmpx - Used to detect whether entries have been deleted from the log file (Solaris only).
* chkproc - Searches for traces of LKM Trojans (Linux Kernel Module - Linux kernel module.)
* chkdirs - Searches for traces of LKM Trojans.
* strings - A utility for quickly searching and replacing text strings.
Chkrootkit has a very good database for detecting various unwanted software and rootkits, I will give a list and show it in the figure below.
List of things chkrootkit can find
Installing chkrootkit for Debian/Ubuntu/Linux Mint.
To start the installation, just run the command:
# sudo apt-get install chkrootkit
Installing chkrootkit on RedHat/CentOS/Fedora
First you need to connect and install the EPEL repository, then run the command:
# yum install chkrootkit
Installation for other operating systems.
We go to the official website and download the latest version of the source code for the chkrootkit , this can be done as follows:
# cd /usr/local/src # wget ftp://ftp.pangeia.com.br/pub/seg/pac/chkrootkit.tar.gz
Then you need to unpack the archive and compile the utility:
# tar xfvz chkrootkit.tar.gz # cd chkrootkit* # make sense
As soon as the program compiles, we run it and scan it.
Using the chkrootkit utility.
To run the utility, just run the command (you just need to run it as root):
# chkrootkit
Options
-x : Shows help about working with the program. -V : Shows the version of the utility. -l : Lists the checks that the program supports. -d : Debug mode. -q : Option that can set the minimum output of information. -x : Option that specifies the output of additional information. -r : <directory>Specifies the name of the directories to use as root. -p : dir_1:dir_2:dir_N This option specifies the paths for external programs used by chkrootkit. -n : This option can be used to disable browsing of all NFS mounted directories.
Examples of using:
1. For example, we want to start searching for Trojan programs in ps and ls and detecting interfaces that operate in packet capture mode, then the utility needs to be launched like this:
# chkrootkit ps ls sniffer
2. If you need to find all suspicious lines in binary files, you need to run the following command:
# chkrootkit -x | more
The output will be carried out page by page. In my opinion this is very convenient.
3. You need to find all suspicious lines in binary files named “bin”:
# chkrootkit -x | egrep '^/bin'
The chkrootkit utility can use other checking utilities, such as awk, cut, egrep, find, head, id, ls, netstat, ps, strings, sed, uname. If these utilities are not available in the search path, then you need to specify the path to them using the -p option.
4. The command below will run chkrootkit tests using the utilities that are stored in the /bin directory on the CD and mounted on the system as /cdrom:
# chkrootkit -p /cdrom/bin
5. You can mount the partition using the command:
# chkrootkit -r /mnt1
This is needed when, for example, you need to scan a HDD on another PC that does not have infected files (if you are 100% sure).
6. You can also redirect the command output to a file. For example, you want a soap report to be sent to you after scanning your system:
0 3 * * * cd /usr/local/bin; ./chkrootkit 2>&1 | mail -s "chkrootkit output for HostName" captain
Every day at 3:00 a.m. a check will be performed, after completion a report will be sent to the local user captain for soap.
7. The LKM test allows you to see in your OS all processes that are hidden from the ps program:
0,10,30 * * * * cd /usr/local/bin; ./chkrootkit lkm 2>&1 | mail -s “LKM search for HostName” [email protected]
The report will be sent via email.
8. With the sniffer test, you can see all computers and interfaces on your network that operate in packet capture mode:
1,5,11,16,21,26,31,36,41,46,51,56 * * * * cd /usr/local/bin; ./chkrootkit sniffer 2>&1 | mail -s “Packet sniffer search result for HostName” captain