What is a network sniffer
Network analyzers make snapshot copies of data transmitted over a network without redirection or modification. Some analyzers work only with TCP/IP packets, but more sophisticated tools work with many other network protocols and at lower levels, including Ethernet.
Years ago, analyzers were tools that were used exclusively by professional network engineers. Nowadays, such software is available for free on the Internet, and they are also popular among Internet hackers and people who are interested in network technology.
Network analyzers are sometimes called network sensors, wireless analyzers, Ethernet analyzers, packet sniffers, packet sniffers, or simply snooping tools.
How are packet sniffers used?
There is a wide range of applications for analyzing packets of data. Most packet sniffers can be used inappropriately by one person and legitimately by another.
For example, a program that captures passwords could be used by a hacker, but the same tool could be used by a network administrator to collect network statistics, such as available bandwidth.
Network monitoring is also used to test firewall or web filters, and to troubleshoot client/server problems.
How network sniffing works
A packet sniffer connected to any network intercepts all data transmitted over that network.
In a local area network (LAN), computers typically communicate directly with other computers or devices on the network. Everything connected to this network is exposed to all this traffic. Computers are programmed to ignore all network traffic that is not intended for that purpose.
Network sniffing software allows access to all traffic by exposing the computer's network interface card (NIC) to listen to that traffic. The software reads this data and performs analysis or data extraction.
After receiving network data, the software performs the following actions:
- The contents or individual packets (sections of network data) are recorded.
- Some software only records the header section of data packets to save space.
- The captured network data is decoded and formatted so that the user can view the information.
- Packet analyzers analyze errors in network communications, troubleshoot network connections, and restore the integrity of data flows destined for other computers.
- Some web search software retrieves sensitive information such as passwords, PINs, and personal information.
How to prevent network eavesdroppers attacks
If you're concerned that network surveillance software is monitoring network traffic coming from your computer, there are ways to protect yourself.
There are ethical reasons why someone might want to use a network sniffer, such as when a network administrator is monitoring the flow of network traffic.
When network administrators are concerned about the malicious use of these tools on their network, they use anti-sniff scanning to protect against sniffer attacks. This means that corporate networks are generally secure.
However, it is easy to obtain and use a network sniffer with malicious intent, making its illegal use on your home Internet a cause for concern. For some, it may be easy to connect such software even to a corporate computer network.
If you want to protect yourself from someone spying on your Internet traffic, use a VPN that encrypts your Internet traffic.
Definition
A sniffer is a traffic analyzer. In turn, traffic is all information that passes through computer networks.
This analyzer looks at what information is being transmitted. To do this, it must be intercepted. In fact, this is an illegal thing, because in this way people often gain access to other people's data.
This can be compared to a train robbery - a classic plot of most Westerns.
You are transferring some information to another user. It is carried by a “train”, that is, a network channel.
The idiots from Bloody Joe's gang intercept the train and rob it completely. In our case, the information goes further, that is, attackers do not steal it in the literal sense of the word.
But let's say that this information is passwords, personal notes, photographs and the like.
Attackers can simply rewrite and photograph all this. This way they will have access to sensitive data that you would like to hide.
Yes, you will have all this information, it will come to you.
But you will know that complete strangers know the same thing. But in the 21st century, information is most valued!
Rice. 1. Train robbery
In our case, exactly this principle is used. Certain people stop traffic, read data from it and send it on.
True, in the case of sniffers, everything is not always so scary. They are used not only to gain unauthorized access to data, but also to analyze the traffic itself. This is an important part of the work of system administrators and simply administrators of various services and resources. It’s worth talking about the application in more detail. But before that, we will touch on how these same sniffers work.
Network traffic analysis tools
Wireshark (formerly known as Ethereal) is widely known as the world's most popular network analyzer. It is a free and open source application that displays traffic data, color-coded to indicate which protocol was used to transmit it.
On Ethernet networks, its user interface displays individual frames in a numbered list and is highlighted in separate colors, regardless of whether they are sent over TCP, UDP, or other protocols.
Wireshark also aggregates the message streams sent back and forth between the source and destination (which are mixed with traffic from other connections over time).
Wireshark supports traffic capture via a push-button start/stop interface. The tool also includes filtering options that limit the data displayed and included in records. This is a critical feature because most network traffic contains routine control messages that are not of interest.
Over the years, many different sensing applications have been developed. Here are some examples:
- tcpdump (command line tool for Linux and other Unix-based operating systems)
- CloudShark
- Cain and Abel
- Microsoft Message Analyzer
- CommView
- OmniPeek
- Capsa
- Ettercap
- PRTG
- Free Network Analyzer
- NetworkMiner
- IP Tools
Some of these network analysis tools are free, while others cost something or have a free trial. Additionally, some of these programs are no longer supported or updated, but are still available for download.
Sniffers: full analysis
darkmagazin.info
Definition
A sniffer is a traffic analyzer. In turn, traffic is all information that passes through computer networks.
This analyzer looks at what information is being transmitted. To do this, it must be intercepted. In fact, this is an illegal thing, because in this way people often gain access to other people's data. This can be compared to a train robbery - a classic plot of most Westerns. You are transferring some information to another user. It is carried by a “train”, that is, a network channel. The idiots from Bloody Joe's gang intercept the train and rob it completely. In our case, the information goes further, that is, attackers do not steal it in the literal sense of the word. But let's say that this information is passwords, personal notes, photographs and the like. Attackers can simply rewrite and photograph all this. This way they will have access to sensitive data that you would like to hide. Yes, you will have all this information, it will come to you. But you will know that complete strangers know the same thing.
But in the 21st century, information is most valued!
In our case, exactly this principle is used. Certain people stop traffic, read data from it and send it on.
True, in the case of sniffers, everything is not always so scary. They are used not only to gain unauthorized access to data, but also to analyze the traffic itself. This is an important part of the work of system administrators and simply administrators of various services and resources. It’s worth talking about the application in more detail. But before that, we will touch on how these same sniffers work.
Principle of operation
In practice, sniffers can be portable devices that are literally placed on a cable and read data and programs from it. In some cases, it is simply a set of instructions, that is, codes that must be entered in a certain sequence and in a certain programming environment. In more detail, traffic interception by such devices can be read in one of the following ways:
- By installing hubs instead of switches. In principle, listening to a network interface can be done in other ways, but all of them are ineffective.
- By connecting a literal sniffer to the place where the channel breaks. This is exactly what was discussed above - the cable is cut and a small device is installed, which reads everything that moves along the channel.
- Installation of a traffic branch. This fork is routed to some other device, possibly decrypted and sent to the user.
- An attack whose goal is to completely redirect traffic to the sniffer. Of course, after the information reaches the reading device, it is again sent to the end user for whom it was originally intended. Hacking in its purest form!
- By analyzing electromagnetic emissions that occur due to traffic movement. This is the most complex and rarely used method.
Here is an approximate diagram of how the second method works. True, it is shown here that the reader is simply connected to the cable. In fact, doing it this way is almost impossible.
The fact is that the end user will still notice that there is a break in the channel at some point.
The very principle of operation of a conventional sniffer is based on the fact that within one Ethernet segment, packets are sent to all connected machines. Quite a stupid, but so far no alternative method! And between segments, data is transmitted using switches. This is where the possibility of intercepting information using one of the above methods appears.
Actually, this is what is called cyber attacks and hacking! By the way, if you install these same switches correctly, you can completely protect the segment from all kinds of cyber attacks. There are other methods of protection, which we will talk about at the very end.
Application
Of course, first of all, this concept has the application discussed above, that is, hacker attacks and illegal acquisition of user data.
Capturing Passwords with Wireshark
Many users do not realize that by filling out a login and password when registering or authorizing on a closed Internet resource and pressing ENTER, this data can easily be intercepted. Very often they are transmitted over the network in an unsecured form. Therefore, if the site you are trying to log into uses the HTTP protocol, then it is very easy to capture this traffic, analyze it using Wireshark, and then use special filters and programs to find and decrypt the password.
The best place to intercept passwords is the core of the network, where the traffic of all users goes to closed resources (for example, mail) or in front of the router to access the Internet, when registering on external resources. We set up a mirror and we are ready to feel like a hacker.
Step 1. Install and launch Wireshark to capture traffic
Sometimes, to do this, it is enough to select only the interface through which we plan to capture traffic and click the Start button. In our case, we are capturing over a wireless network.
Traffic capture has begun.
Step 2. Filtering captured POST traffic
We open the browser and try to log in to some resource using a username and password. Once the authorization process is complete and the site is opened, we stop capturing traffic in Wireshark. Next, open the protocol analyzer and see a large number of packets. This is where most IT professionals give up because they don't know what to do next. But we know and are interested in specific packages that contain POST data that is generated on our local machine when filling out a form on the screen and sent to a remote server when we click the “Login” or “Authorization” button in the browser.
We enter a special filter in the window to display captured packets: http.request.method == “POST”
And we see, instead of thousands of packages, only one with the data we are looking for.
Step 3. Find the user's login and password
Quick right-click and select Follow TCP Steam
After this, text will appear in a new window that restores the contents of the page in code. Let's find the fields “password” and “user”, which correspond to the password and username. In some cases, both fields will be easily readable and not even encrypted, but if we are trying to capture traffic when accessing very well-known resources such as Mail.ru, Facebook, VKontakte, etc., then the password will be encrypted:
HTTP/1.1 302 Found Date: Mon, 10 Nov 2014 23:52:21 GMT Server: Apache/2.2.15 (CentOS) X-Powered-By: PHP/5.3.3 P3P: CP=»NOI ADM DEV PSAi COM NAV OUR OTRo STP IND DEM" Set-Cookie: non=non; expires=Thu, 07-Nov-2024 23:52:21 GMT; path=/ Set-Cookie: password=e4b7c855be6e3d4307b8d6ba4cd4ab91; expires=Thu, 07-Nov-2024 23:52:21 GMT; path=/ Set-Cookie: scifuser=networkguru; expires=Thu, 07-Nov-2024 23:52:21 GMT; path=/ Location: loggedin.php Content-Length: 0 Connection: close Content-Type: text/html;
Thus, in our case:
Username: networkguru
Password: e4b7c855be6e3d4307b8d6ba4cd4ab91
Step 4. Determine the encoding type to decrypt the password
For example, go to the site https://www.onlinehashcrack.com/hash-identification.php#res and enter our password in the identification window. I was given a list of encoding protocols in order of priority:
- MD5
- NTLM
- MD4
- L.M.
Step 5. Decrypting the user password
At this stage we can use the hashcat utility:
~# hashcat -m 0 -a 0 /root/wireshark-hash.lf /root/rockyou.txt
At the output we received a decrypted password: simplepassword
Thus, with the help of Wireshark, we can not only solve problems in the operation of applications and services, but also try ourselves as a hacker, intercepting passwords that users enter in web forms. You can also find out passwords for user mailboxes using simple filters to display:
- The POP protocol and filter looks like this: pop.request.command == "USER" || pop.request.command == "PASS"
- The IMAP protocol and filter will be: imap.request contains "login"
- The protocol is SMTP and you will need to enter the following filter: smtp.req.command == “AUTH”
and more serious utilities for decrypting the encoding protocol.
Step 6: What if the traffic is encrypted and uses HTTPS?
There are several options to answer this question.
Option 1. Connect when the connection between the user and the server is broken and capture traffic at the moment the connection is established (SSL Handshake). When a connection is established, the session key can be intercepted.
Option 2: You can decrypt HTTPS traffic using the session key log file recorded by Firefox or Chrome. To do this, the browser must be configured to write these encryption keys to a log file (FireFox based example) and you should receive that log file. Essentially, you need to steal the session key file from another user's hard drive (which is illegal). Well, then capture the traffic and use the resulting key to decrypt it.
Clarification. We're talking about the web browser of a person whose password they're trying to steal. If we mean decrypting our own HTTPS traffic and want to practice, then this strategy will work. If you are trying to decrypt the HTTPS traffic of other users without access to their computers, this will not work - that is both encryption and privacy.
After receiving the keys according to option 1 or 2, you need to register them in WireShark:
- Go to the menu Edit – Preferences – Protocols – SSL.
- Set the flag “Reassemble SSL records spanning multiple TCP segments”.
- “RSA keys list” and click Edit.
- Enter the data in all fields and write the path in the file with the key
WireShark can decrypt packets that are encrypted using the RSA algorithm. If the DHE/ECDHE, FS, ECC algorithms are used, the sniffer will not help us.
Option 3. Gain access to the web server that the user is using and obtain the key. But this is an even more difficult task. In corporate networks, for the purpose of debugging applications or content filtering, this option is implemented on a legal basis, but not for the purpose of intercepting user passwords.
Video:
How to properly connect to the network to capture traffic?
Capturing traffic on the client or server side
If problems arise with the user or the services he uses, all experts recommend starting to find and fix problems on the client side, if the requests are not widespread. We install the protocol analyzer locally or remotely on the user's workstation, and we are ready to remotely capture traffic and begin the diagnostic process.
Advantages when capturing traffic:
- on the client or server - a very simple process that only requires installing a protocol analyzer, often remotely;
- on the client or server – when launched correctly, the analyzer does not affect any services or processes on the client’s workstation;
- on the client – it is possible to capture wireless traffic;
- on the client – the ability to capture VPN traffic inside the tunnel;
- on the server – the ability to see sessions of other clients and evaluate their impact on the performance of the service and the server as a whole;
- on the server – the ability to see traffic between blades or virtual machines on a physical server.
We take into account when capturing traffic:
- on the client or server - when capturing traffic, you can see long packets. Why is this happening? When the operating system needs to transfer a large amount of data over the network, it first divides the entire volume into segments. Typically, segmentation is carried out at the TCP level and already segmented data is transferred to the network interface, this process is called TCP segmentation offload (TSO). For example, we need to transmit a 128KB packet, which by default will be divided into 92 segments of 1448 bytes, which will be transmitted through the network interface over the network. Thus, there is a reduction in the use of CPU resources for packet segmentation.
- on the client or server - if we use the free Wireshark protocol analyzer, then it is better not to use wireshark.exe or tshark.exe, but run it in the background using the DUMPCAP.EXE command.
How to configure Dumpcap correctly:
When analyzing complex problems, and especially analyzing short-term and intermittent problems, it is necessary to capture traffic over a long period of time. There is a problem on the network that appears once or twice a week and at different times. How to catch her? Many people have asked this question. Using Wireshark in this case is not a good option for several reasons. Firstly, the graphical interface of the protocol analyzer loads the memory and processor of the device on which it is running and secondly, Wireshark captures traffic and simultaneously analyzes it, which causes the use of additional resources and as the file grows, the number of allocated resources also increases.
How to launch and configure Dumpcap?
To solve problems of long-term traffic capture, it is better to use the Dumpcap.exe program, which is installed along with WireShark and is located in the appropriate folder:
To run the program, you must use the command line launched with administrator rights. The startup and syntax of the Dumpcap program is as follows:
dumpcap –i 4 –q – b filesize:200000 –b files:5000 –B 1024 –w c:\traces\mytrace.pcapng
Dumpcap launch options:
-i 4 – index of the network interface through which traffic is captured.
-q – run the program in the background.
-b filesize: 200000 - file size in kilobytes. In this case, the file is 200 MB in size.
-b files: 5000 - the number of files that will be written to the folder. In this case, 5000 files. Those. the total volume will be 1 TB of data - 5000 files of 200 MB each.
-B 1024 is the size of the buffer in MB into which captured packets are pre-stored.
-w c:\traces\mytrace.pcapng – path to the folder where the files will be saved
For convenience, you can create an executable file with the bat extension so that you always have it at hand with the correct syntax.
Colleagues from Trimelab have made an excellent online command line configurator Dumpcap.
In its fields, you just need to enter the launch parameters described above, and at the output you will receive text, which, by copying it into the command line, you can immediately start capturing traffic.
How to work with Dumpcap?
Packets are captured by the network interface driver that we specified when activating the program and are then placed in a buffer to smooth out traffic peaks. The buffer size can be configured by the user. When working on 64-bit machines, we recommend using 1 GB; for a 32-bit operating system, no more than 500 MB. The "npf.sys" process is part of a program that is installed when you install WireShark called WinPcap. Then the “dumpcap.exe” program, using two libraries “wpcap.dll” and “packet.dll”, moves packets from the buffer to files in the folder that we specified on the command line with the extension “pcap” or “pcapng”.
In our example, we indicated that the number of files should be 5000, so when saving the 5000th file, the program will begin to overwrite the first one, and so on in a circle. For a 64-bit operating system, we recommend using files no larger than 200 MB, for a 32-bit operating system no more than 100 MB, but 50 MB is better. This does not affect the traffic capture process, but when you start analyzing captured files using WireShark, loading and analyzing (filters, changing columns, etc.) larger files will be very slow. With the settings in our example (200 MB per file and 5000 files), the folder volume will be 1 TB and when capturing traffic at a speed of 1 Gbit/sec and loading it at 50%, the recording speed will be 450 MB per hour. So in Terabyte we will have traffic for the last two hours.
Dumpcap can be run on any device - workstation or server. This will not create any significant processor and memory load, unless of course you have specified a large buffer size for recording packets from the network card driver. The input/output system will experience a greater load, i.e. disks for recording files. Therefore, it is not recommended to use system drives to save files. A good solution is to save data to an external USB drive.
Further use of the program follows a very simple scenario. As soon as the problem is detected, go to the folder where the traffic captured by Dumpcap is stored. Saved files are timestamped to the nearest second. We select the files that were saved at the time the problem occurred and carry out their further decoding and analysis using Wireshark.
In this case, we will be able to capture traffic indefinitely. This will be useful if we are catching a problem that is not permanent. Plus, when the process is launched in this way, it will not cause additional problems to the user and practically does not use the resources of the workstation.
- on the client or server – we do not use system disks to save data so as not to affect the performance of the client’s computer. It is better to use external USB drives.
- on a server – the volume of traffic is significantly larger, so the USB drive must be of the correct size. When capturing traffic at a speed of 1 Gbit/s and loading the interface at only 50%, the recording speed will be 450 MB per hour. Thus, to store traffic for the last hour you will need about 500 MB.
- on the server - you should take into account the possible consolidation of network cards in order to increase fault tolerance at the level of the network adapter and, accordingly, network traffic. Failure of a group network adapter does not lead to loss of network connection; the server switches network traffic to healthy group adapters. Also, combining network cards allows you to aggregate the bandwidth of the adapters included in the group. When performing network operations, such as copying files from shared folders, the system can potentially use all adapters in the group, improving performance.
Capture on the switch by setting up a mirror or SPAN
The second most popular way to capture traffic in an IT environment is to set up a mirror or SPAN session. After entering special commands, the switch copies all traffic from the source port and sends a copy to the port to which we can connect a laptop with Wireshark or a specialized server with a protocol analyzer installed. To correctly configure this function, we recommend that you refer to the switch user manual.
This method is useful in several scenarios if:
- it is necessary to capture traffic between devices without interrupting the service itself.
- it is necessary to understand the source of the problem, which affects not only one client or server, but the whole group. In this case, we can set up a SPAN session for the Uplink port and see all traffic from clients to servers and back. But in this case, we will not see communication between servers if the application is multi-level.
- You need to understand the source of the problem, which affects a group of servers or users. If we can set up a session for an entire virtual local network (VLAN), then, unlike the first case, we will also see traffic between servers if they are part of the same VLAN. But with this version of the SPAN session, we can see traffic doubling.
In modern networks, to increase the fault tolerance of servers, they are connected to the network with two network adapters and they are grouped according to any of the standards (IEEE 802.3ad or IEEE 802.1ax LACP). If we are solving a problem with such a server, then we need to mirror both ports on the switch to which it is connected. If the server is connected to different switches, then it is necessary to use a hardware analyzer with several interfaces and connect it to two SPAN ports on different switches.
Advantages of SPAN for copying traffic:
- Very easy to set up
This is often done remotely, or even using RSPAN, if possible.
- There is absolutely no impact on traffic and communication between devices
You need to be careful when setting up SPAN on Cisco. There is no “foolproof” here and you can “put down” the port.
- You can get a copy of traffic from several sources
On inexpensive switch models, in the documentation you can find the ability to copy at least all 23 ports into one, but remember to load the interfaces you are copying and the bandwidth of the port to which you connect the analyzer. A laptop with a gigabit card is only useful if the output load is 10-15% of the gigabit.
- You need to see the traffic of the entire VLAN
We just remember once again that in this case the traffic may be doubled and you need to be careful when analyzing TCP retransmissions. You should pay attention to the SEQ number of the package and IP ID. If they are the same, then it is a double. If different, then this is a package that has been sent again.
- Does not have any noticeable effect on the switch
We take into account when setting up SPAN to copy traffic:
- The switch will not allow you to see errors at the physical and data link levels of the OSI model.
- It is necessary to control the bandwidth of the recipient port of copied traffic so as not to overload it and start losing packets. Rx and Tx full duplex 1 Gbit/s at 100% load - this is 2 Gbits of traffic on the SPAN port.
- A free port is required to receive copied traffic.
- Limited number of available SPAN sessions on the switch.
- It is necessary to read the documentation for the switches, as there are restrictions on the speed of copied traffic.
Sniffer programs
CommView. The program is paid, like everyone else on our list. One minimum license costs $300. But the software has rich functionality. The first thing worth noting is the ability to independently set rules for tracking other people's traffic. For example, you can make ICMP or TCP (these protocols) completely ignored. It is also noteworthy that the program allows you to view details and a log of all sent packets. There is a regular version and a Wi-Fi version.
SpyNet. This is, in fact, the Trojan that we are all so tired of. But it can also be used for noble purposes, which we talked about above. The program intercepts and decrypts packets that are in the traffic. There are many unusual features. For example, you can recreate pages on the Internet that the “victim” visited. It is noteworthy that this software is free, but it is quite difficult to find.
All information is provided by the DarkMagazin team darkmagazin.info
Problems with network sniffers
Network sniffing tools offer a great way to learn how network protocols work. However, they also provide easy access to some private information, such as network passwords. Contact the owners to obtain permission before using the analyzer on their network.
Network probes only intercept data from the networks to which their host computer is connected. On some connections, sniffers only capture traffic addressed to that specific network interface. In any case, the most important thing to remember is that anyone who wants to use a network analyzer to monitor traffic will have a difficult time doing so if that traffic is encrypted.
Operating principles of packet sniffers
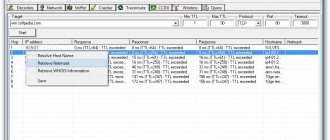
Further in this article we will consider only software sniffers designed for Ethernet networks. A sniffer is a program that operates at the NIC (Network Interface Card) level (link layer) and secretly intercepts all traffic. Because sniffers operate at the data link layer of the OSI model, they do not have to play by the rules of higher-layer protocols. Sniffers bypass the filtering mechanisms (addresses, ports, etc.) that Ethernet drivers and the TCP/IP stack use to interpret data. Packet sniffers capture from the wire everything that comes through it. Sniffers can store frames in binary format and later decrypt them to reveal higher-level information hidden inside (Figure 1).
In order for the sniffer to capture all packets passing through the network adapter, the network adapter driver must support promiscuous mode. It is in this mode of operation of the network adapter that the sniffer is able to intercept all packets. This mode of operation of the network adapter is automatically activated when the sniffer is launched or is set manually by the corresponding sniffer settings.
All intercepted traffic is passed to a packet decoder, which identifies and splits packets into the appropriate hierarchy levels. Depending on the capabilities of a particular sniffer, the provided packet information can subsequently be further analyzed and filtered.