Advantages of WPA over WEP
WPA, WiFi Protected Access is a new, currently most modern, mechanism for protecting wireless networks from unauthorized access. WPA, and its further development WPA2, replaced the WEP mechanism, which had begun to become obsolete by that time. Once again, let's look at the principle of operation of WEP: 1. A data frame consists of an encrypted and an unencrypted part. The encrypted part contains data and checksums (CRC32), the unencrypted part contains the initialization vector and key identifier. 2. Each data frame is encrypted with an RC4 stream cipher using an initialization vector with a WEP key appended to it as the encryption key. Thus, for each data frame, its own encryption key is generated, but at the same time, each new encryption key differs from the other only by the initialization vector. (24 bits, when the key length can be 40 or 104 bits) Thus, if an attacker intercepts a large number of packets, he will receive the following: - a large number of initialization vectors - a large amount of encrypted data - the encryption key for each subsequent frame differs from the previous one by 4 bits (initialization vector length) Thus, it is possible to extract the key by performing mathematical operations on packets. In order to successfully obtain a WEP key, an attacker needs the following: - to be in a place where it is possible to receive a network signal (an RSSI of -85 dBm is quite enough) - to capture about 100-200 thousand initialization vectors, depending on the key length (WEP-40 or WEP-104). Typically, this requires intercepting 25-50 MB of traffic transmitted on the network. If there is high network activity (downloading files (especially using peer-to-peer networks), video conferences), 5-10 minutes will be enough to capture the required amount of traffic. Also pay attention to how the attacker performs traffic capture. Typically, wireless network adapters operate in normal mode - they only accept packets that are sent to their MAC address, provided that they are connected to this wireless network. However, nothing physically prevents the wireless network adapter from capturing all packets that are within its range on the selected channel. To implement this feature, there are special unofficial drivers and software. Moreover, such software is sold quite legally, and it is used to monitor wireless networks. An example of such a program is CommView for WiFi from TamoSoft. Next, the attacker analyzes the captured traffic. Since WEP was cracked many years ago, you can find utilities on the Internet that automatically extract the key from a CAP file with traffic, the most common of which is Aircrack. Thus, WEP has the following disadvantages - predictability of the encryption key for the frame - lack of authentication means on the network - weak mechanism for checking data integrity Therefore, many enterprises refused to use wireless networks altogether to avoid leakage of corporate information. However, with the advent of WPA, and subsequently WPA2, the situation changed, and more and more enterprise users began to use WPA. Indeed, in comparison with WEP, it has a number of advantages: - mathematical independence of encryption keys for each packet - a new mechanism for calculating the checksum - WPA includes authentication tools for the 802.1X protocol
How to protect your data if Wi-Fi no longer guarantees security?
The fact that WPA has been hacked is alarming news that affects many electronic devices, but there is no cause for alarm.
Essentially, researchers have found a vulnerability in the Wi-Fi protocol that makes wireless traffic potentially eavesdropping on attackers. In other words, anyone can use this flaw in network security to spy on other people’s actions on the Internet, steal credit card numbers, passwords, intercept messages in instant messengers, etc.
Fortunately, manufacturers of many gadgets have already managed to improve and finalize their devices, eliminating the found vulnerability. And besides, WPA2 is far from the only wall of protection between a hacker and users’ personal data.
To hack someone else's Wi-Fi, an attacker, firstly, needs to position his receiving antenna within range of the radio channel, and secondly, most of the information on the Internet is transmitted in encrypted form, and the hacker will not be able to read it in any case.
The https protocol, which most web servers run on, adds an extra layer of security to your connection, just like using a VPN service.
That's why you should always remember the padlock icon in your browser's address bar. If the small padlock is not displayed there, it means that the site does not use the https protocol, and all information entered into forms, including passwords, may be accessible to third parties.
That's why before you send your home address or payment details anywhere, you should always make sure there is a padlock in the address bar.
Almost immediately after the news of the Wi-Fi protocol vulnerability, all leading software developers released corresponding patches for their products. For example, Microsoft released an update for Windows in October 2020. Apple also patched its macOS and iOS operating systems around the same time.
Google released an update to Android in November, so anyone with a device running the platform should check the About section of their phone or tablet's settings to see when the latest security update was available. If it was performed before November, and the phone has Android 6 or an earlier version of the OS, then an update must be made.
How WPA works
The first modifications of WPA were an improvement on WEP. Let's consider one of the first WPA protocols, WPA-TKIP. It uses a 48-bit initialization vector, and the rules for constructing the vector are changed; it also uses MIC (Message Integrity Code) to calculate the checksum, which is used instead of the outdated and less reliable CRC32. And the most important improvement is that the length of the encryption key is now 128 bits, instead of 40. There is a special hierarchy for managing the keys, which is designed to prevent the encryption key from being predictable for each frame. With TKIP, the encryption key for each data frame is generated in such a way that they do not repeat each other, even if only partially. Thus, WPA networks are completely protected from replay (key repetition) and forgery attacks (substitution of packet contents), which could not be said about WEP, where it was possible to bypass the CRC32 checksum check and also send a frame with exactly the same encryption key , like the previous one. At the same time, WPA has integrated authentication mechanisms: EAP, and also provides full support for 802.1X standards for authentication. EAP - Extensible Authentication Protocol, one of the most common authentication protocols. It is used for authentication in wired networks, and therefore a WPA wireless network can be easily integrated into an existing infrastructure. A mandatory condition for authentication is the user presenting an access token confirming his right to access the network. To obtain a token, a request is made to a special database, and without authentication, the user will be prohibited from working on the network. The verification system is located on a special RADIUS server, and Active Directory is used as a database (in Windows systems). Thus, WPA is a synthesis of the following technologies and standards: WPA = 802.1X + EAP + TKIP + MIC However, TKIP protection was partially hacked in 2008. To successfully bypass it, your wireless router must use QoS. An attacker may be able to intercept and decrypt data transmitted over the network, as well as forge packets transmitted over the network. Therefore, WPA2 was developed, which is an improved WPA.
Types of protection
So, let's start with the fact that until recently the WEP structure was considered the most secure connection security technology. It used key integrity verification when connecting any device wirelessly and was an IEEE 802.11i standard.
WPA2-PSK WiFi network protection works, in principle, almost the same, but it checks the access key at the 802.1X level. In other words, the system checks all possible options.
However, there is a newer technology called WPA2 Enterprise. Unlike WPA, it requires not only a personal access key, but also the presence of a Radius server providing access. Moreover, such an authentication algorithm can operate simultaneously in several modes (for example, Enterprise and PSK, using AES CCMP level encryption).
How WPA2 works
The discovery of vulnerabilities in WPA led to the creation of the WPA2 security method. Its significant difference from WPA is that traffic on the network is encrypted not only from devices not connected to this network, but also from each other. In other words, each device has its own encryption keys for exchanging data with the access point. There are several encryption keys on the network: 1) Pairwise Transient Key (PTK). Using this type of key, the personal traffic of each client is encrypted. In this way, the network is protected from the inside so that one client authorized on the network cannot intercept the traffic of another. 2)Group Temporal Key (GTK). This key encrypts broadcast data. WPA2 is used as the CCMP encryption algorithm
CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol), a block encryption protocol with a message authentication code and block and counter chaining mode, is an encryption protocol for the WPA2 network, using the AES algorithm as the basis for data encryption. A 128-bit encryption key is used in accordance with the FIPS-197 standard. The main difference from TKIP and WEP is centralized packet integrity management, which is performed at the AES level. Structure of a CCMP encrypted packet
The CCMP packet is extended by 16 octets. The CCMP header consists of three parts: PN (packet number, 48-bit), ExtIV (initialization vector), and key identifier. Data encapsulation using CCMP: 1) The packet number is incremented by a certain number to avoid repeated packets 2) Additional authentication data is created 3) A nonce service field is created 4) The packet number and key identifier are placed in the packet header 5) The nonce field and additional authentication data are encrypted using a temporary key. Data decapsulation using CCMP: 1) Additional identification fields and a nonce field are created using the packet data. 2) The additional identification data field is extracted from the header of the encrypted packet 3) The A2 field, the packet number and the priority field are extracted 4) The MIC field is extracted 5) The packet is decrypted and its integrity is checked using the packet ciphertext, additional identification data, the temporary key and the actual MIC 6) The package is assembled in decrypted form. 7) Packets with a duplicate number are discarded. This encryption method on the network is currently the most reliable.
WPA2-PSK: what is it?
Let's say right away: this is a system for protecting any local connection to a wireless network based on WI-Fi. This has nothing to do with wired systems based on network cards that use a direct connection using Ethernet.
WiFi network protection using WPA2-PSK technology is the most advanced today. Even somewhat outdated methods that require a username and password, and also involve encryption of confidential data during transmission and reception, look, to put it mildly, like baby talk. And that's why.
Authentication methods in WPA\WPA2
Authentication, that is, confirmation by the user of rights to access resources, is a prerequisite for the operation of WPA\WPA2. For this, the classic implementation of WAP\WPA2 includes support for 802.11 and EAP. In other words, in order for a client device to successfully complete the connection process, it must identify itself. In practice, this looks like this: the user is asked to enter a login and password to access the network. Credential verification is performed on the RADIUS server, which in turn communicates with the authentication server. A Windows Server 2008R2 domain controller is used as an authentication server, and it is also used as a RADIUS server. A similar approach to implementing WPA\WPA2 is called WPA-Enterprise. It is used in large production networks where Active Directory infrastructure is already deployed. However, it is obvious that deploying Active Directory and RADIUS in a small business or home environment is almost impossible. Therefore, in order for the WPA\WPA2 standards to be used in the home, the Wi-Fi Alliance has developed a simplified implementation called WPA-PSK (Pre-Shared Key). It uses the same encryption protocols, but its user authentication scheme is greatly simplified. In order for a device to receive a network access token, a special passphrase called a Pre-Shared Key must be entered on the device. The length should be from 8 to 32 characters, and you can use special characters, as well as characters from national alphabets. After entering the passphrase, it is placed in a special association packet (key exchange packet, handshake), which is transmitted to the access point. If the passphrase is correct, the device is issued a network access token. This approach is many times simpler than WPA-Enterprise, and therefore is widely used among small businesses and home users.
Wi-Fi Security Modes
Confused yet? All you really need to do is choose the one that is the safest option on the list that works with your devices.
Here are the options you're likely to see on your router:
- Open (risky) : Open Wi-Fi networks do not have a passphrase. You shouldn't set up an open Wi-Fi network - it's like removing the lock from your front door.
- WEP 64 (Risky) : The old standard WEP protocol is vulnerable and you should not use it.
- WEP 128 (risky) : This is the same as WEP, but with a larger encryption key size. In fact, it is as vulnerable as WEP 64.
- WPA-PSK (TKIP) : Uses the original version of the WPA protocol (essentially WPA1). It has been replaced by WPA2 and is not secure.
- WPA-PSK (AES) : Uses the original WPA protocol, but replaces TKIP with the more modern AES encryption. It is offered as an intermediate option: devices that support AES will almost always support WPA2, and devices that require WPA will almost never support AES encryption. So this option makes little sense.
- WPA2-PSK (TKIP) : Uses the modern WPA2 standard with the older TKIP encryption. This is not secure, and is suitable if you have older devices that cannot connect to a WPA2-PSK (AES) network.
- WPA2-PSK (AES) : This is the most secure option. It uses WPA2, the latest Wi-Fi encryption standard, and the latest AES encryption protocol. You must use this option. On some devices, you'll simply see a "WPA2" or "WPA2-PSK" option. If you do this, it will probably be to use AES, since it is a common sense choice.
- WPAWPA2-PSK (TKIP/AES) : Some devices offer and even recommend this mixed mode option. This option allows you to use both WPA and WPA2, with both TKIP and AES. This ensures maximum compatibility with any legacy devices you may have, but also allows attackers to infiltrate your network by hacking the more vulnerable WPA and TKIP protocols.
WPA2 certification became available in 2004. Since 2006, WPA2 certification has become mandatory. Any device manufactured after 2006 with the "Wi-Fi" logo must support WPA2 encryption.
Since your Wi-Fi enabled devices are likely no more than 10 years old, you won't have any problems choosing WPA2-PSK (AES). If the device stops working, you can always change it. Although, if your safety is important to you, then it is better to buy a new device released after 2006.
Vulnerabilities in WPA\WPA2
For all its advantages, WPA\WPA2 is not without vulnerabilities. Let's start with the fact that back in 2006, TKIP encryption in WPA was broken. The exploit allows you to read data transmitted from the access point to the client machine, as well as transmit fake information to the client machine. To implement this attack, the network must use QoS. Therefore, I also do not recommend using WPA to secure your wireless network. Of course, it is more difficult to crack than WEP, and WPA will protect you from an attack by schoolchildren with Aircrack, however, it will not withstand a targeted attack on your organization. For the greatest security, I recommend using WPA2. However, WPA2 is not without vulnerabilities. In 2008, a vulnerability was discovered that could allow a man-in-the-middle attack. It allowed a network participant to intercept and decrypt data transmitted between other network participants using their Pairwise Transient Key. Therefore, when working in such a network, it makes sense to use additional means of encrypting transmitted information. (PSKZI “Shipka” for example) At the same time, please note that in order to take advantage of this vulnerability, an attacker must be authorized and connected to the network. However, I would like to focus on the “home” implementation of WPA-PSK. It simplifies the authorization scheme; the bottleneck in it is the Pre-Shared Key itself, since entering this key gives the device full access to the network (if MAC filtering is not enabled). The key itself is stored at the access point. Depending on the model and firmware of the device, methods of protecting it are implemented. In some cases, it is enough for an attacker to gain access to the web control panel and obtain the Pre-Shared Key, which is stored there in clear text. In some cases, the field with it is protected like a password field, but it is still possible to extract it if an attacker is able to remove the memory chip from the device and gain low-level access to it. Therefore, pay attention to the physical security of your wireless equipment. And finally, the latest vulnerability is the ability to intercept handshake packets, in which the Pre-Shared Key is transmitted when a device connects to the network. As long as the Pre-Shared key is encrypted, the attacker has only one option left - a brute force attack on the captured association packets. On the one hand, this is irrational, but it is worth understanding that for this you do not need to be near the access point at all, and for such a brute force (or dictionary) attack, an attacker can use large computing resources. It is also worth noting that in order to intercept a handshake, an attacker does not have to wait until a new device is connected to the network. On some wireless adapters, when using non-standard drivers, it is possible to send reassociation packets to the network, which will interrupt network connections and initiate a new key exchange on the network between clients and the access point. In this case, in order to capture the required packets, it is necessary that at least one client is connected to the network. Also, the attacker needs to be close to the access point so that the power of his adapter (and such adapters are usually low-sensitive and low-power, and overheat greatly during operation) is enough to SEND reassociation packets (remember WEP, where you just needed to “catch” a sufficient amount of traffic ). Finally, a brute force attack takes a long time, but using a computing cluster makes the task much easier.
AES vs TKIP
TKIP and AES are two different types of encryption that can be used by a Wi-Fi network.
TKIP is an older encryption protocol introduced with WPA to replace the insecure WEP encryption. TKIP is actually very similar to WEP encryption. TKIP is no longer considered secure and is deprecated.
In other words, you shouldn't use TKIP.
AES is a more secure encryption protocol introduced with WPA2. AES is not some rigid standard designed specifically for Wi-Fi networks. This is a serious global encryption standard that is used even by government agencies. For example, when you encrypt a hard drive with TrueCrypt, it may use AES encryption.
AES is considered fairly secure, and the main disadvantages may be susceptibility to brute force attacks and security breaches in other aspects of WPA2.
The short explanation is that TKIP is an older encryption standard used in the old WPA. AES is a new Wi-Fi encryption solution used by the new and secure WPA2 standard. In theory, this is the end! But, depending on your router, choosing WPA2 may not be a good enough solution.
While WPA2 must use AES for optimal security, it can also use TKIP when backward compatibility with legacy devices is needed. In this state, devices that support WPA2 will connect to WPA2, and devices that support WPA will connect to WPA. Therefore, "WPA2" does not always mean WPA2-AES. However, on devices without a visible "TKIP" or "AES" option, WPA2 is usually synonymous with WPA2-AES.
What are we protecting ourselves from?
You need to know the enemy by sight, so below we will briefly go through the mechanics of possible attacks against the WPA2-Enterprise network with authentication using domain accounts.
Connecting clients to a false access point. Knowing the network name SSID (ESSID if the network is built on several access points) and the MAC address of the access point (BSSID), an attacker can deploy an illegitimate access point.
To increase their chances of success, attackers use the following simple techniques:
- an illegitimate access point has a stronger signal than a legitimate one;
- an illegitimate access point is deployed where the signal of legitimate access points does not reach, but where there are clients who usually connect to this network.
In order to have somewhere to connect this access point, the attacker deploys his own RADIUS server, to which the illegitimate access point will connect. This RADIUS server does not have the task of authenticating the client and checking whether the client specified the correct password. The main thing is to receive from the client authorization data, login and a response to the challenge provided by the false Radius server. The attacker will use them to guess the password offline and then connect to the target corporate wireless network.
Without broadcast monitoring, detecting the location of an illegitimate access point is not always easy. The attacker is unlikely to look like a person with a huge backpack, a bunch of antennas and a diesel generator on a cart.
For example, for their pentests, colleagues from Digital Security use a portable household router with a built-in battery (like this one). They reflash using OpenWRT and install a custom package. The output is an access point with a built-in RADIUS server, which can, if necessary, listen to the air and collect data. If you wish, you can even use a regular telephone.
The placement of such access points is limited only by the ingenuity of the attacker. If the victim's office is located in a business center, then you can deploy the access point in the foyer to the turnstiles or lobby with sofas. It is convenient to place such an access point in an elevator car: it moves away from legitimate access points at high speed, so the client device is trapped and is likely to connect to a false access point. An attacker can even ride with a false access point on corporate transport, which takes employees to the metro after work.
Forced deauthentication . If the client is already connected to a legitimate access point, then it needs to be somehow disconnected from it (forcibly deauthenticated) in order to reconnect to the false one. The attacker is listening to the broadcast. To do this, he switches his Wi-Fi adapter to monitor-mode. Typically, the aicrack-ng set of utilities is used for this. With its help, the attacker begins to send messages to wireless clients that the legitimate access point to which the client is already connected is disconnected and goes off the air. This effect is achieved by injecting wi-fi management frames (Management Frames), namely: deassociation and deauthentication frames.
As a result, the client disconnects from the access point and begins to look for a new access point with the same ESSID. In this situation, an access point with a stronger signal comes in handy. The client device is trying to connect to it. If a client authenticates to a false RADIUS server, an attacker can hijack the username and MSCHAPv2 authentication session.
The main causes of the error “Saved, WPA\WPA2 protection”
Authentication is a special protection technology that prevents uninvited guests (users) from entering the work area and personal data. In public places, special access points are installed, to which countless clients can connect to use the Internet channel and traffic.
There may be attackers among them. That is why it is important to prevent unauthorized connections, create high-quality encryption technology, and choose the original password.
The most common authentication method is WPA-PSK/WPA2. The main types of encryption include:
- Code for all subscribers. Connection to the network occurs either with a general password (key), or each client is given personal access in the form of a password made up of numbers and Latin letters of different case.
- Code for companies with an increased level of digital content security. A huge number of users and office employees are connected to such a network. This is where secure authentication becomes most important.
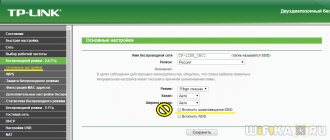
Note! Often this situation arises because errors occur in the router settings. Before changing the settings of your phone or tablet, you need to understand the router.
Using a smartphone, a network client can make sure that they are not entering incorrect data. He needs to enter the value “192.168.1.0” in the browser’s address bar, as indicated on the router. In the drop-down menu, the client is interested in only two lines: SSID and PSK.
The user tries to connect the device to Wi-Fi, and an error appears on the screen: “Saved, WPA\WPA2 protected.” A proven method for eliminating such a message is to reboot the router. However, this is not the only way to solve the problem.
The ultimate goal of users is to connect to the Internet, which is distributed by the Wi-Fi router. To achieve this, it is important to understand what causes this behavior of wireless networks, router or smartphone model.
The client’s actions when trying to access the network are logical and consistent:
- A Wi-Fi access point is selected.
- The password is entered.
- The status changes - “Connection - Authentication - …”.
And here it is, a “Chinese message” pops up - “Saved, WPA2 or WPA protection”, and then:
- "Authentication error." The root cause why this happens is to be found in problems with passwords or security settings on routers.
- "Saved." If the Internet connection is still closed, it means that the Wi-Fi network settings have failed.
Important! When changing the parameters and functionality of the router’s network, it is imperative to “cut” the saved network on the phone. In the Wi-Fi Setting tab, you need to select the desired network and hold it until the menu appears. In the “Change” item you can specify a new password.
Causes
Authentication failure can often be caused by entering an incorrect password. To do this, check the layout (Cyrillic, Latin), letter case. To simplify the procedure, many people change the router password to a digital one so as not to be confused about the letter meaning.
The tablet does not connect to Wi-Fi and writes “Saved, WPA2 protection” in cases where the wireless connection mode is simply not supported. This problem is relevant for “retro” models of digital equipment or budget versions based on Android OS. To solve the issue, just change the 802.11 b/g standard, that is, disable n or Auto. Then the connection to the Internet occurs again.
Note! In some cases, it will not help to change the password, but to change the location in the network settings (for example, to Germany, the USA, the UK).
Effective ways to resolve problems with authentication errors are the following:
- Change authentication and WPA encryption. Switching from WPA2-Personal (installed by default in some gadget models) to WPA (AES) often helps.
- Searching for a free channel for the network, changing its width by 10-20 MHz with weak signal reception. To do this, you will need an item in the Wireless - Channel Width section, where you need to select the Auto option or a drop-down list with several values.
- Configuring access points for IPv4, IPv6 with the BT modem disabled.
- Rebooting Flight mode. All that is required is to turn this item on and off, after which the likelihood of Wi-Fi “resuscitation” will increase and the network will connect without additional clicks.
- Fix problems automatically with the Android Fixer app, downloadable for free via Google Play. This software is able to fix numerous authentication-related errors.
Note! The above solutions will help get rid of the problem when Wi-Fi is saved but does not connect. It can occur both when trying to connect to a home network, and in cafeterias, airports, and train stations.
Have all the ways to get rid of the annoying “Saved, WPA\WPA2 protected” message failed? Don’t despair, because different devices, tablets, laptops, smartphones running on Android, do not always have the same settings and are full of numerous nuances.
Steps to resolve the error
When access to a Wi-Fi network is denied, the first thing to do is reboot the router. Users on the network recommend turning it off for 10 seconds, and then turning it on again.
It often happens that while sitting on the Internet scrolling social networks, communicating on Viber, Skype or using office applications, the Internet disappears. At the same time, the connection icon and the signal level are displayed on the screen. No matter how much Wi-Fi is turned on/off, the inscription does not go away.
Rebooting the router is not a guarantee that the Internet will resume operation. If this does not happen, you need to proceed to the following steps:
- mark the correct region in the router configurations or try moving it to another;
- check the password is correct;
- change the network operating mode in the router functionality;
- change the degree and type of protection (encryption), the router password to digital.
Important! There is no need to rush to change the model of your smartphone or tablet, or complain about the performance of the Android OS. To ensure a normal connection, it is better to connect to standard settings.